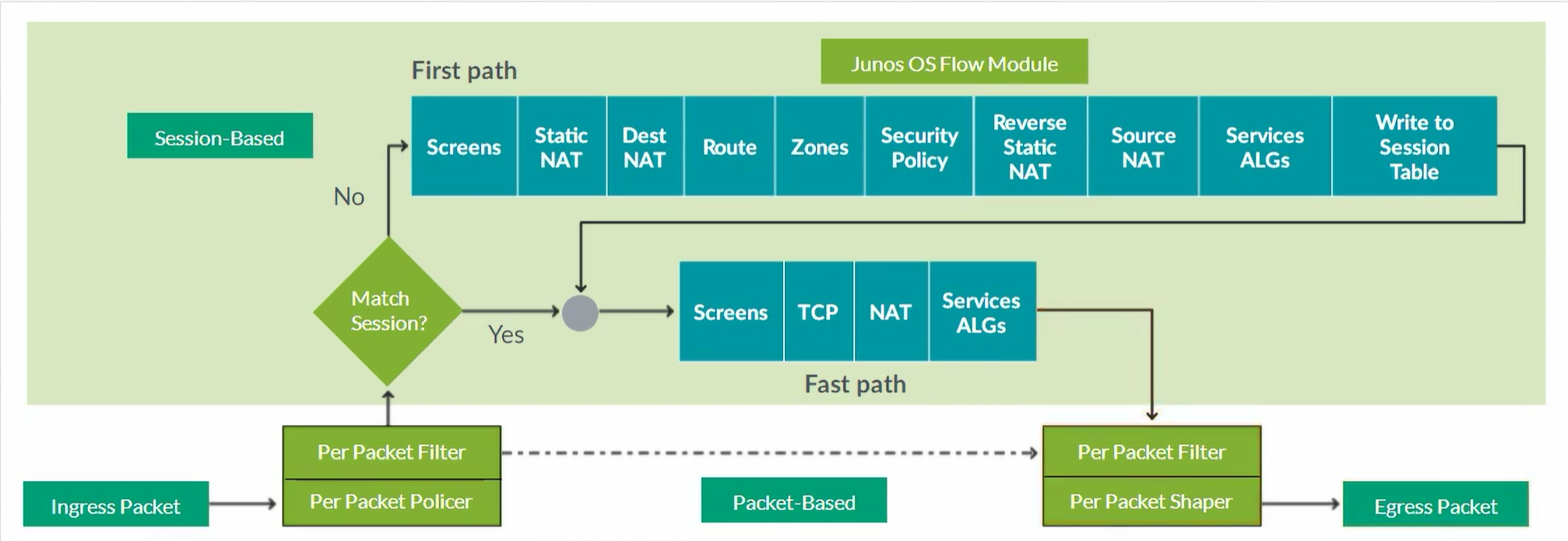
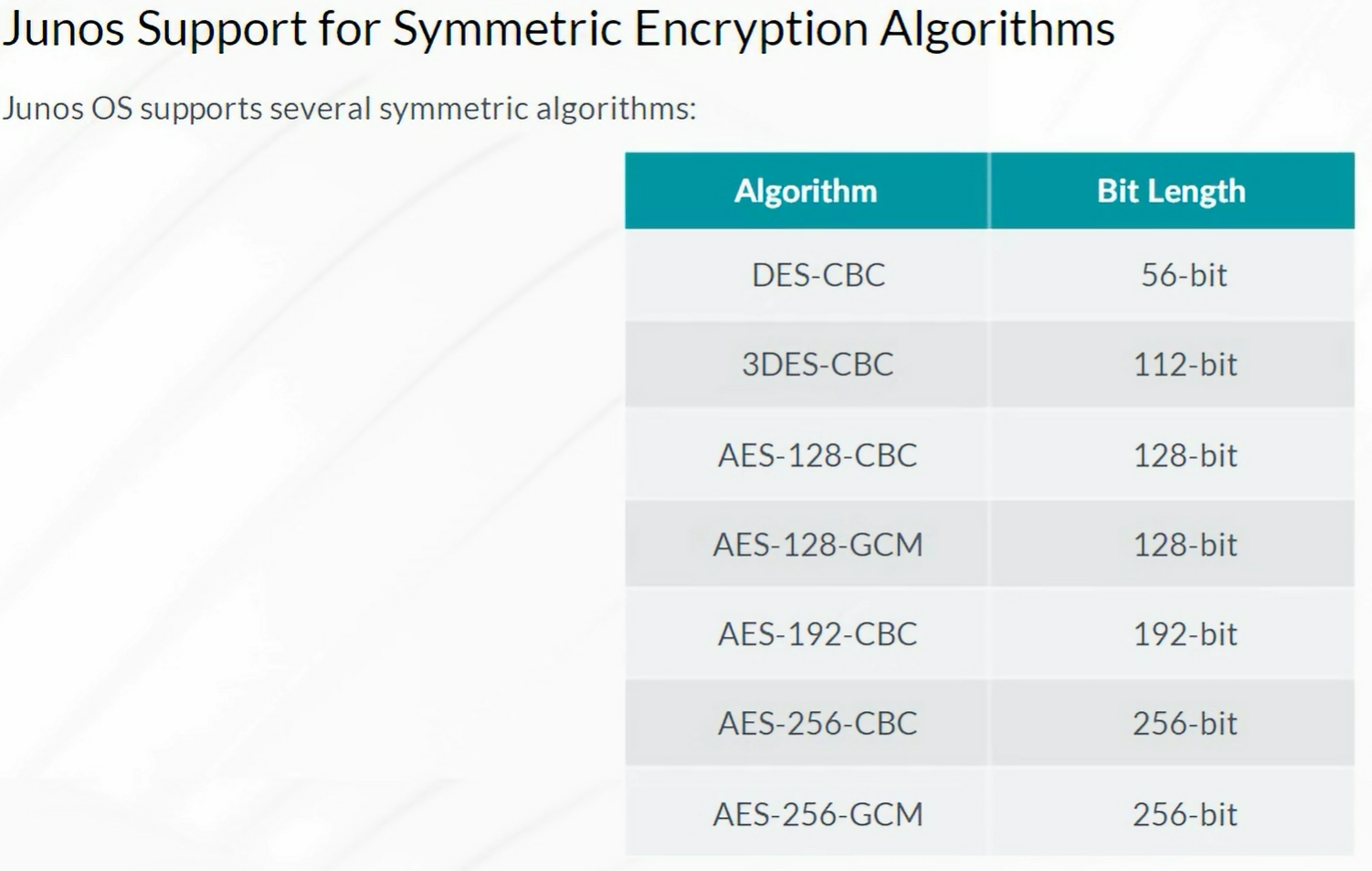
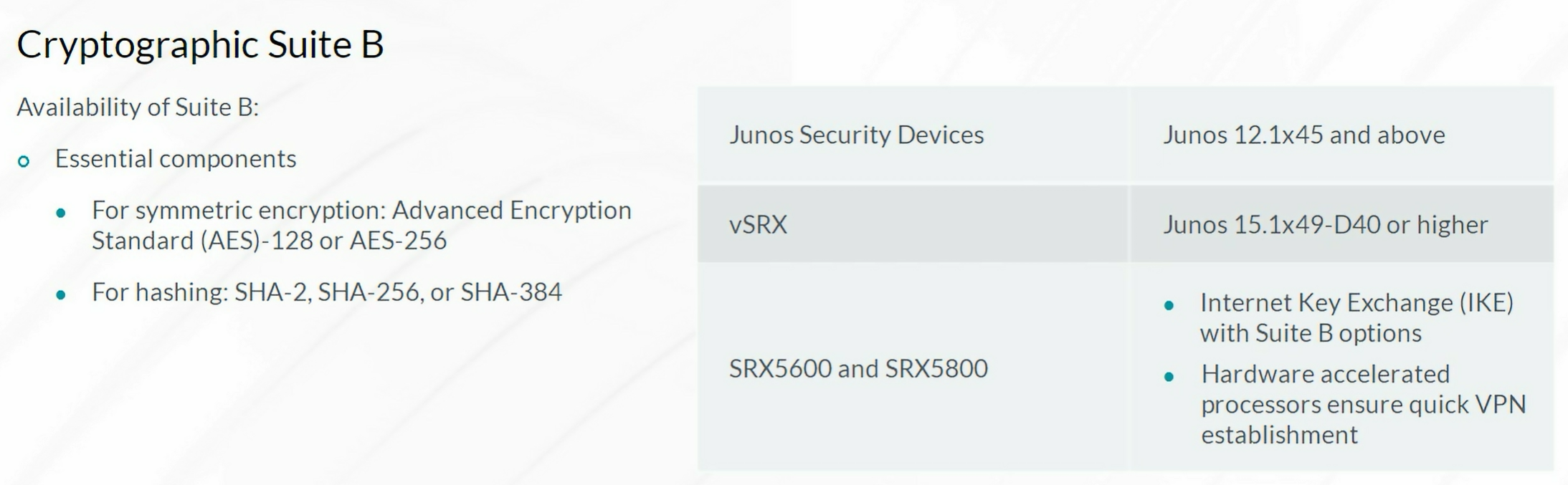
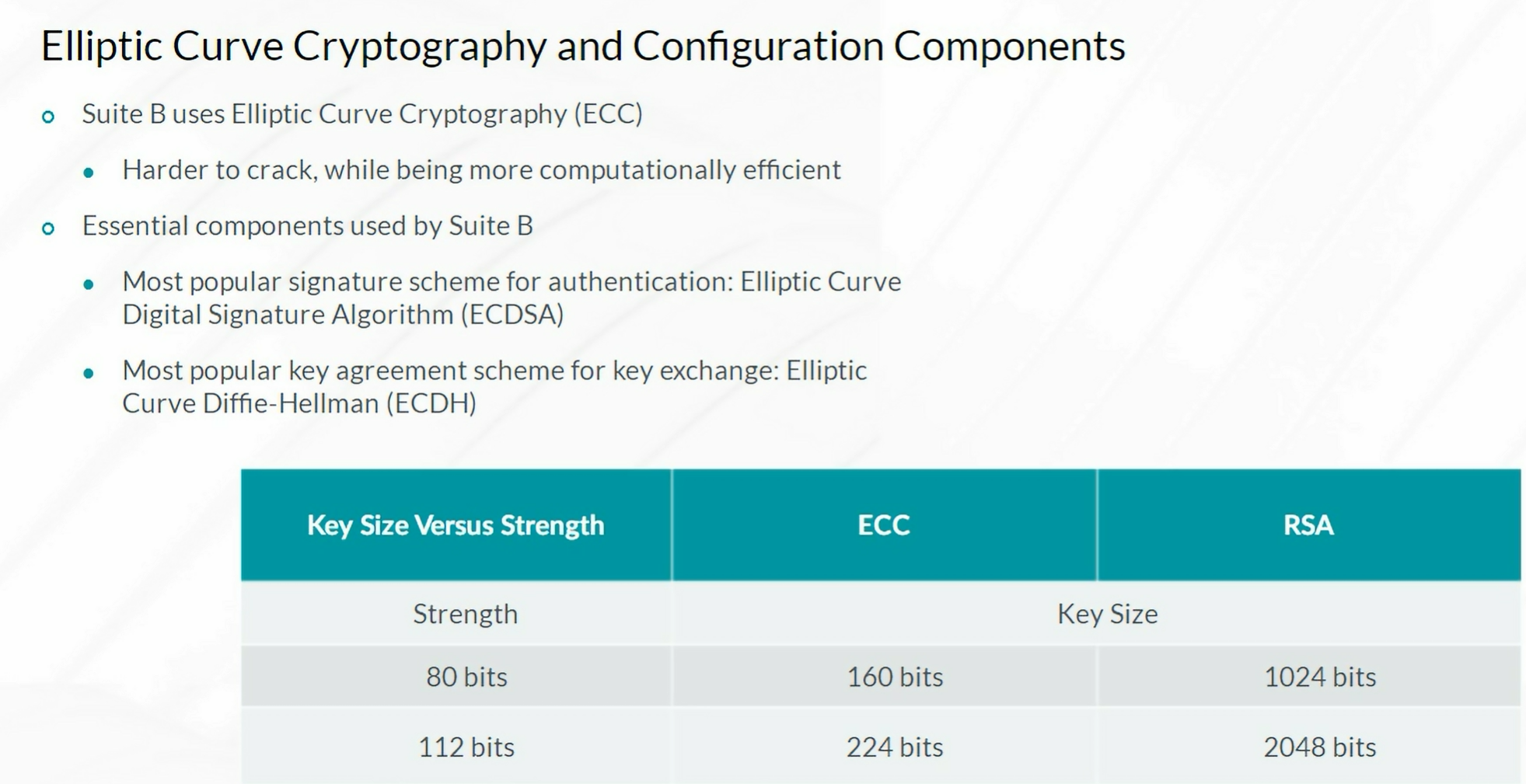
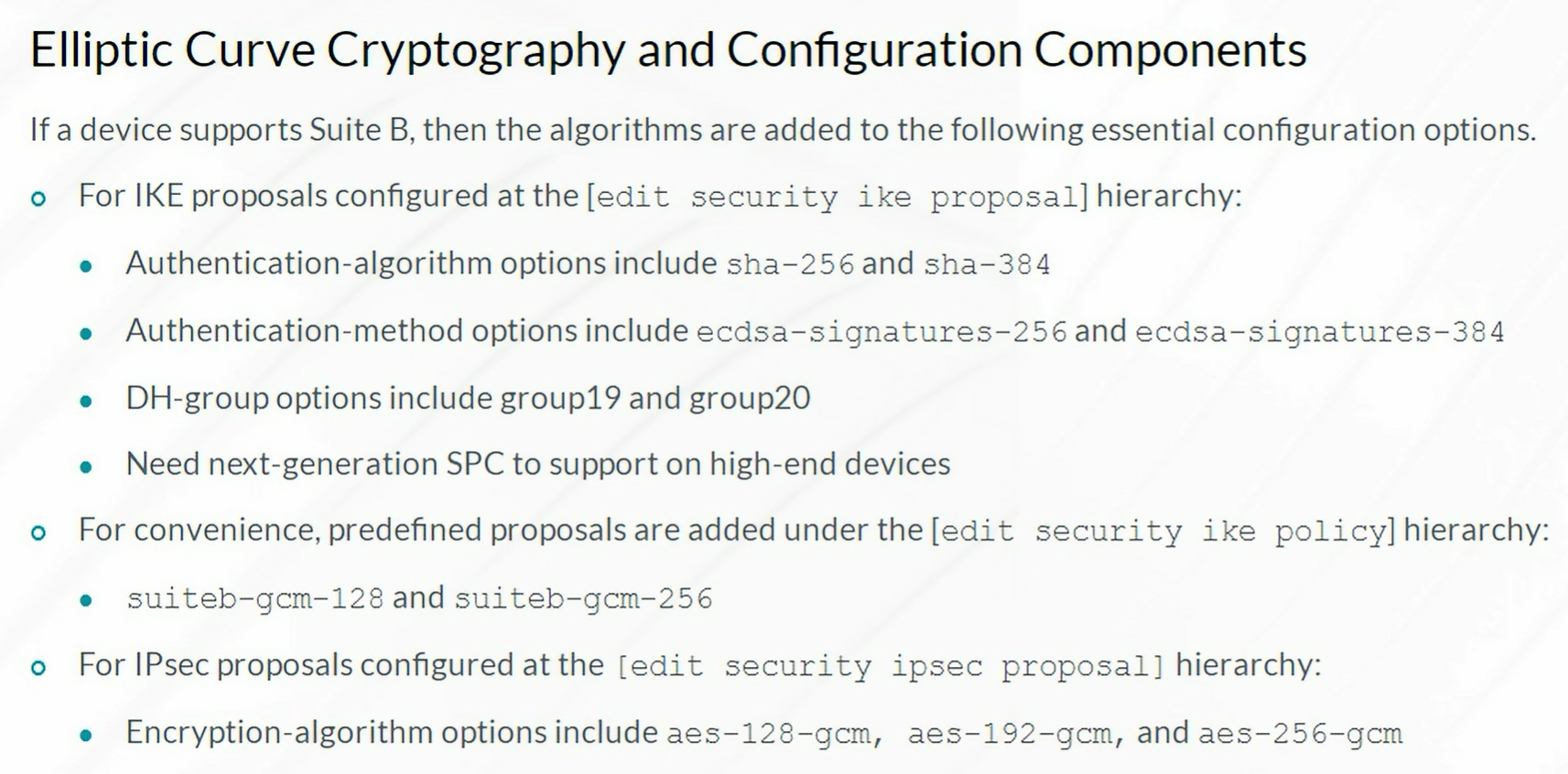
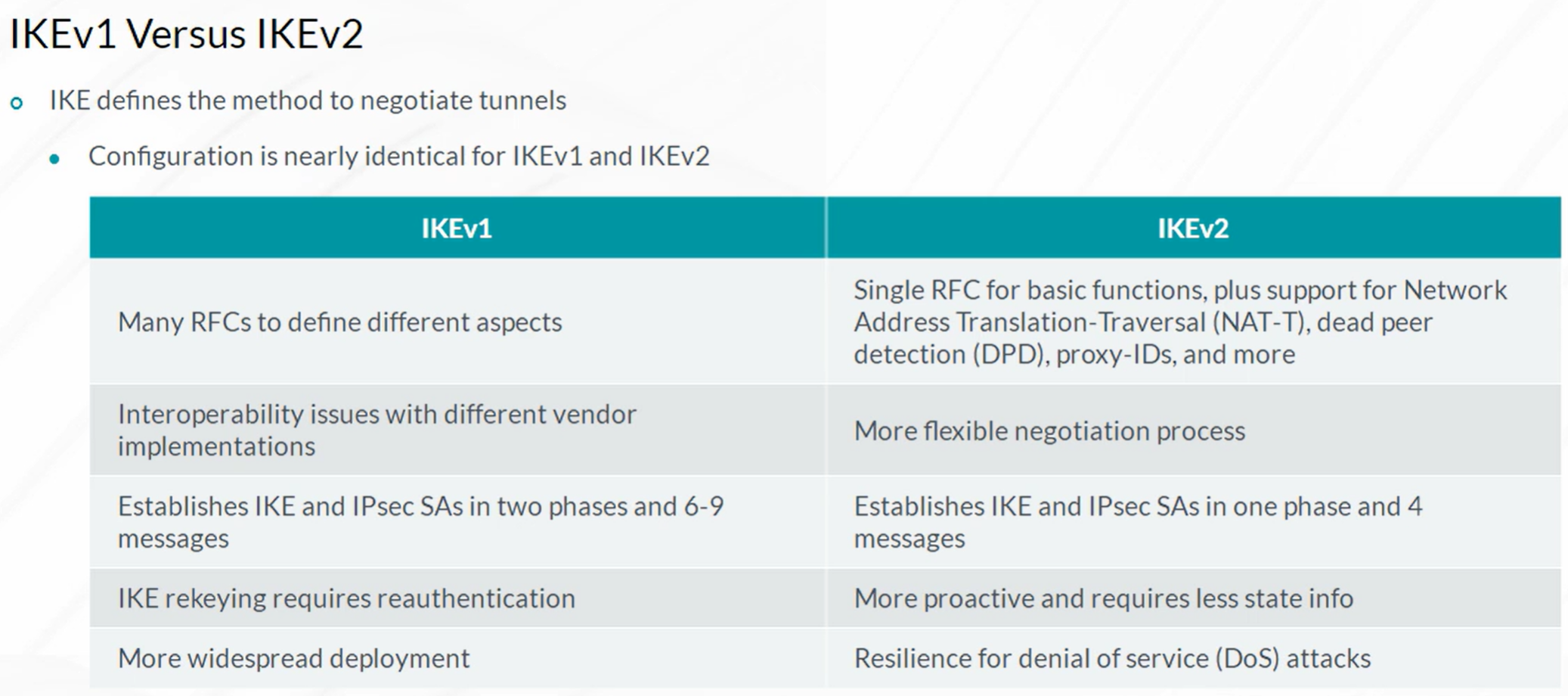
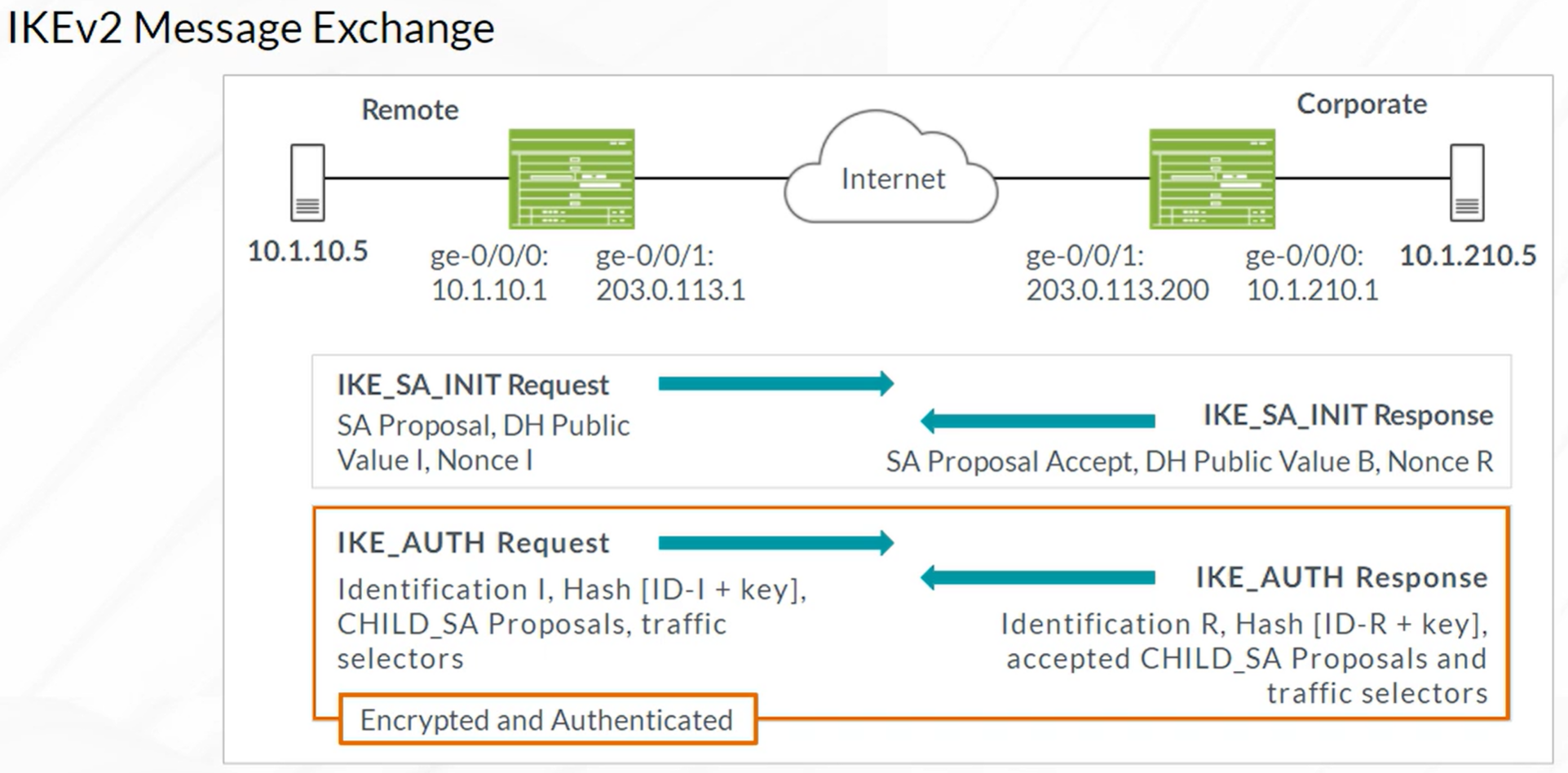
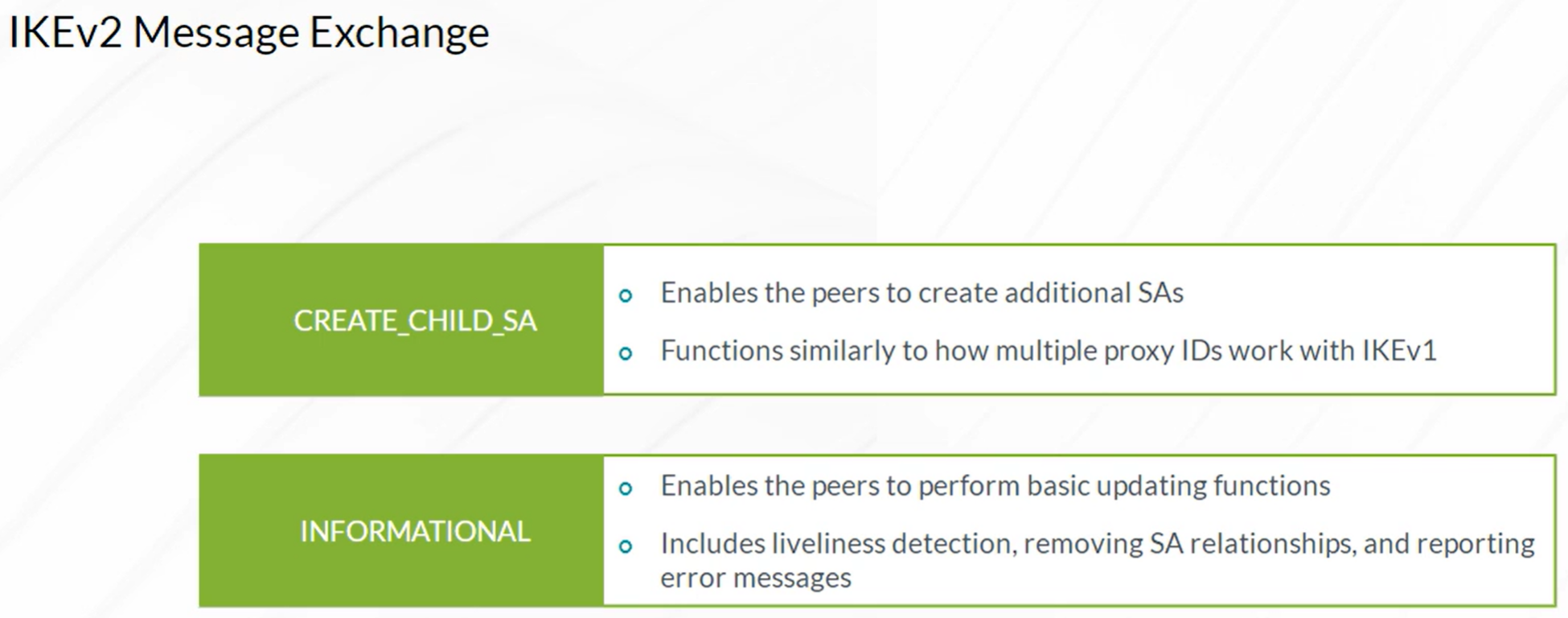
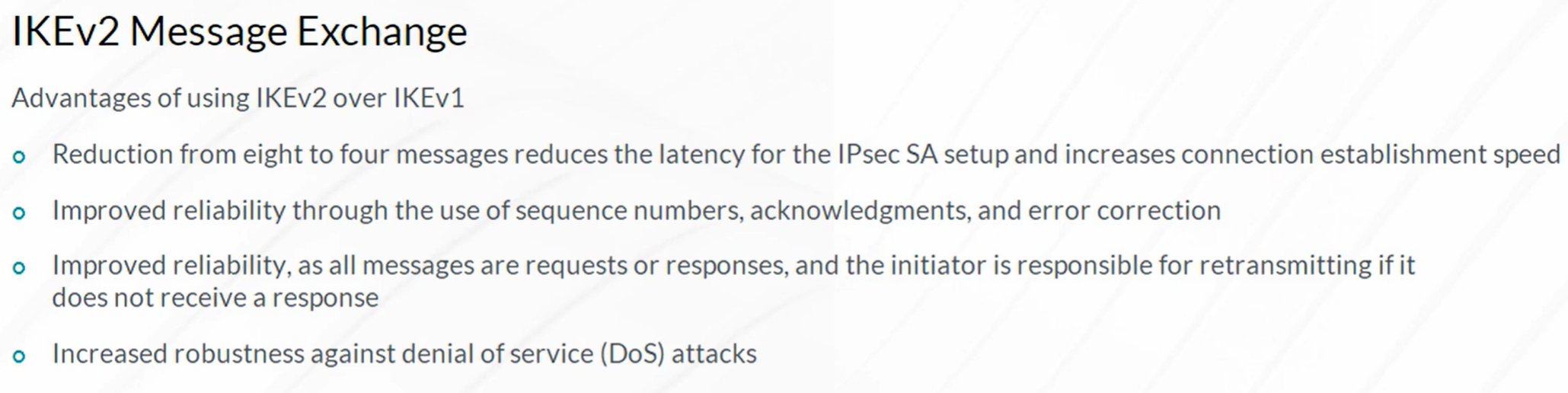
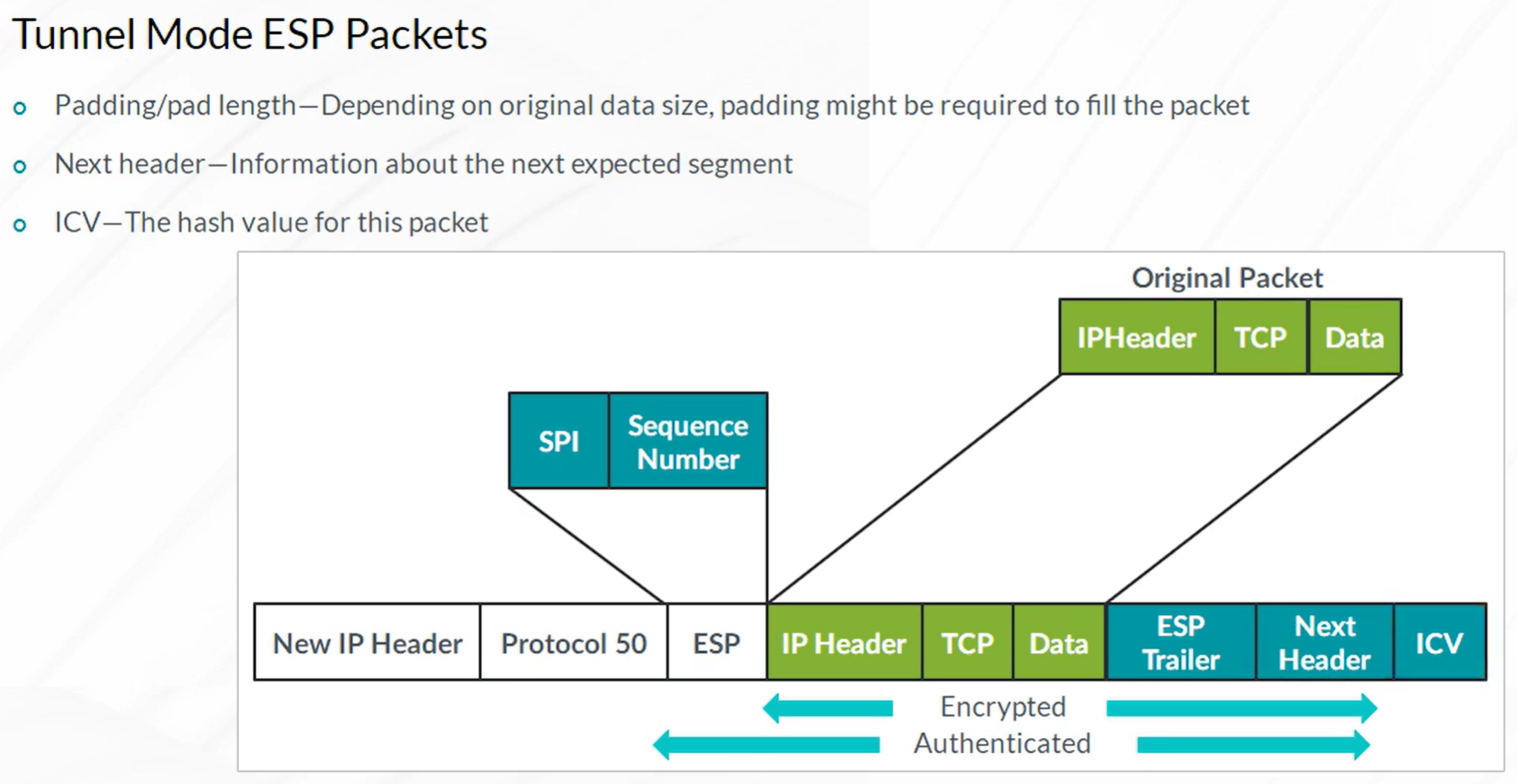
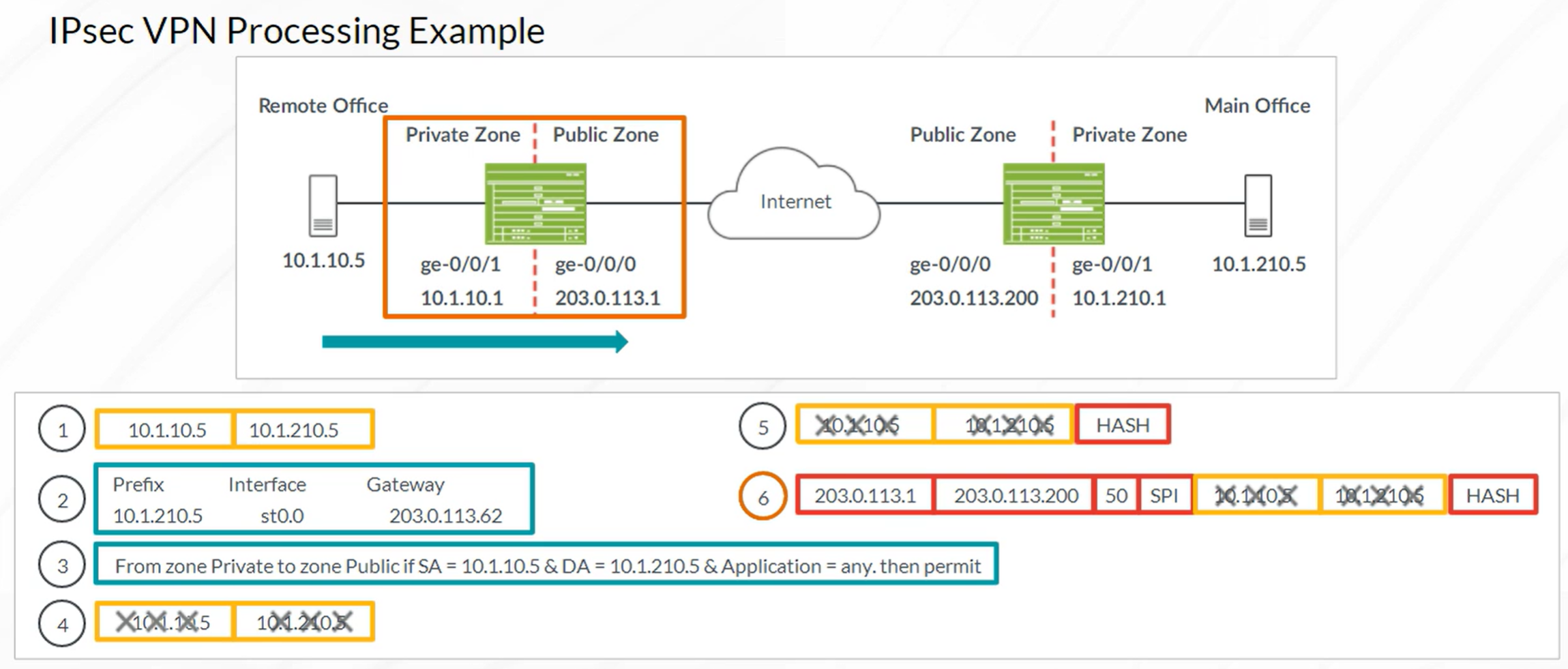
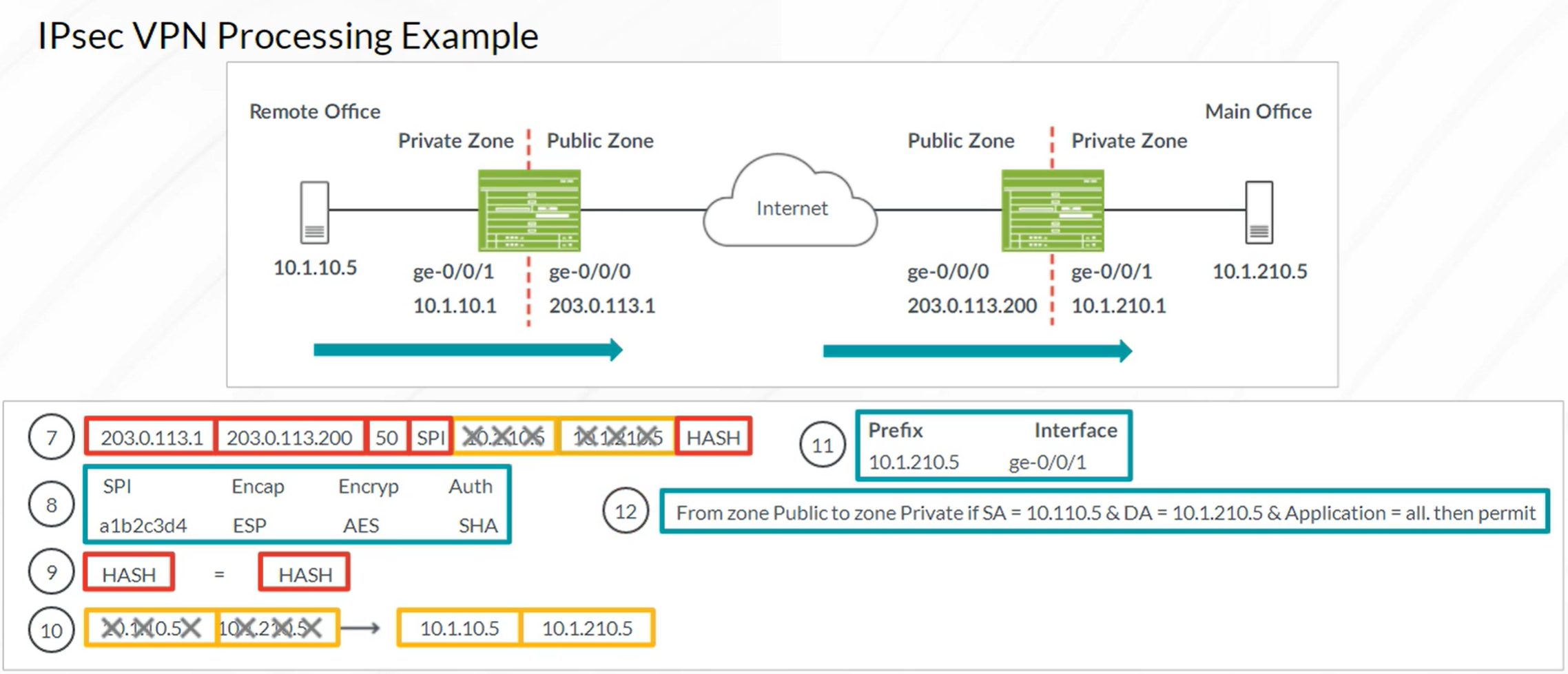
Packet Mode Processing
The SRX basically operates like a Router.
1
| set security forwarding-options family mpls mode packet-based
|
Logical Packet Flow
Branch SRX Series Factory-Default configuration
- Interface
ge-0/0/0 is set for untrust zone and to get IP via DHCP - Default IP address on
fxp0.0: 192.168.1.1/24 - Interface
irb.0 is the trust zone with address 192.168.2.1/24 - All other ports are configured as Layer 2
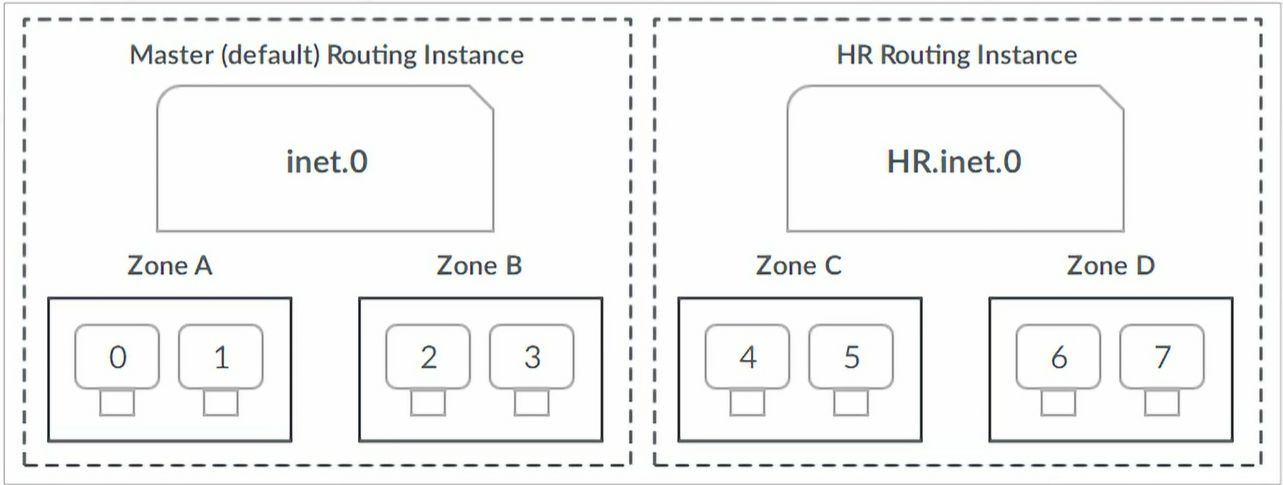
Security Zones
Interfaces can pass and accept traffic only if assigned to non-null zone.
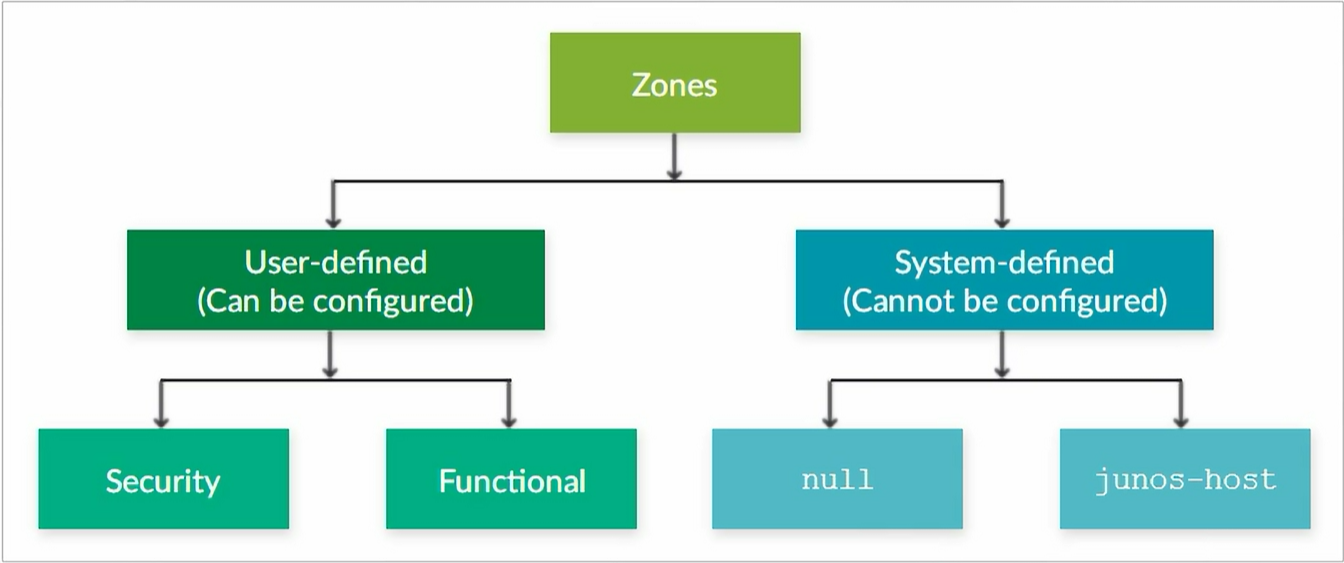
Types of Zones
Creating a Zone
1
2
3
4
5
6
7
| set security zones security-zone untrust interface ge-0/0/0.0
set security zones security-zone trust interface ge-0/0/1.0
set security zones security-zone dmz interface ge-0/0/2.0
set security zones security-zone Server interface ge-0/0/3.0
set security zones security-zone VPN interface st0.0
set security zones functional-zone management interface ge-0/0/3.0
|
Allow SSH and FTP inbound the Security Zone called “HR” and destined to the SRX
1
2
| set security zones security-zone HR host-inbound-traffic system-services ssh
set security zones security-zone HR host-inbound-traffic system-services ftp
|
Show commands
1
| show security zones <NAME>
|
Junos-Host Zone CLI Configuration
Junos-Host zone can be used to for additional checks for traffic destined to SRX itself. When not configuring any security policy to-zone junos-host, the traffic/packets will be validated based on host-inbound-traffic configured under security zones. If you configure security policy to-zone junos-host, that policy check will be done additional to host-inbound-traffic/services specified under zones.
Allow specific hosts from SRC_ZONE to SSH to the SRX
1
2
3
4
5
6
| set security policies from-zone <SRC_ZONE> to-zone junos-host policy ssh-management match source-address host1
set security policies from-zone <SRC_ZONE> to-zone junos-host policy ssh-management match destination-address any
set security policies from-zone <SRC_ZONE> to-zone junos-host policy ssh-management match application junos-ssh
set security policies from-zone <SRC_ZONE> to-zone junos-host policy ssh-management match dynamic-application none
set security policies from-zone <SRC_ZONE> to-zone junos-host policy ssh-management match url-category none
set security policies from-zone <SRC_ZONE> to-zone junos-host policy ssh-management then permit
|
Block all other SSH attempts from other hosts
1
2
3
4
5
6
7
| set security policies from-zone <SRC_ZONE> to-zone junos-host policy ssh-block match source-address any
set security policies from-zone <SRC_ZONE> to-zone junos-host policy ssh-block match destination-address any
set security policies from-zone <SRC_ZONE> to-zone junos-host policy ssh-block match application junos-ssh
set security policies from-zone <SRC_ZONE> to-zone junos-host policy ssh-block match source-identity any
set security policies from-zone <SRC_ZONE> to-zone junos-host policy ssh-block match dynamic-application none
set security policies from-zone <SRC_ZONE> to-zone junos-host policy ssh-block match url-category none
set security policies from-zone <SRC_ZONE> to-zone junos-host policy ssh-block then deny
|
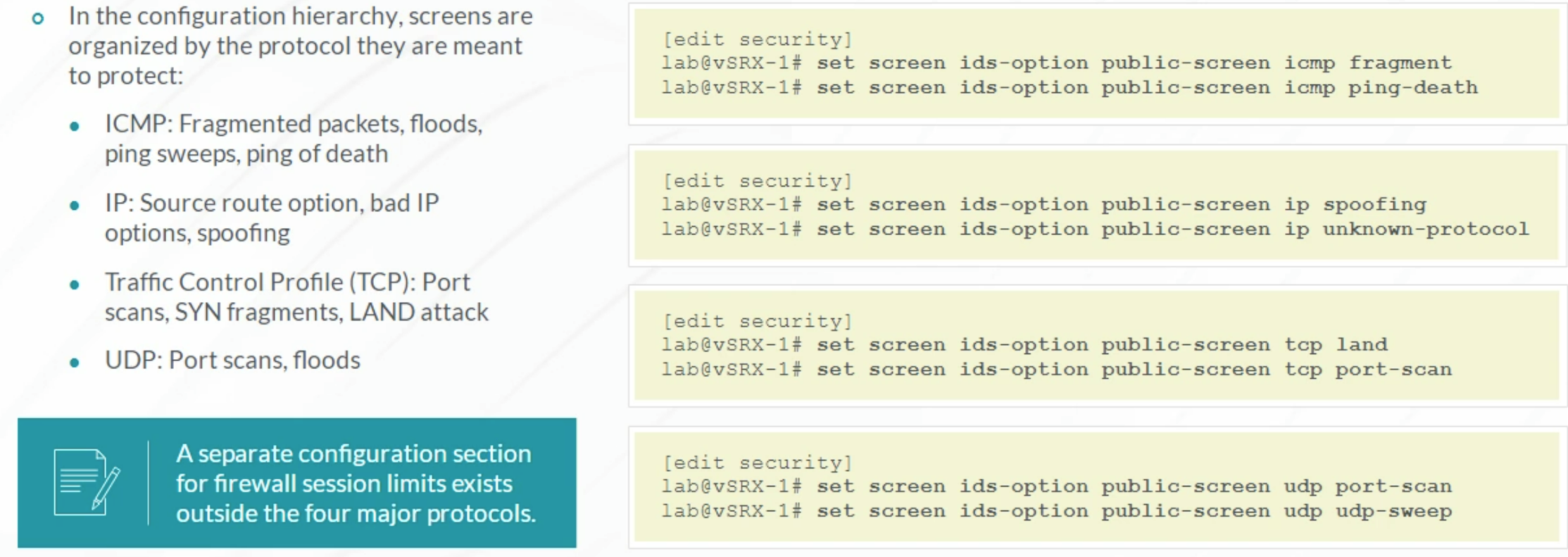
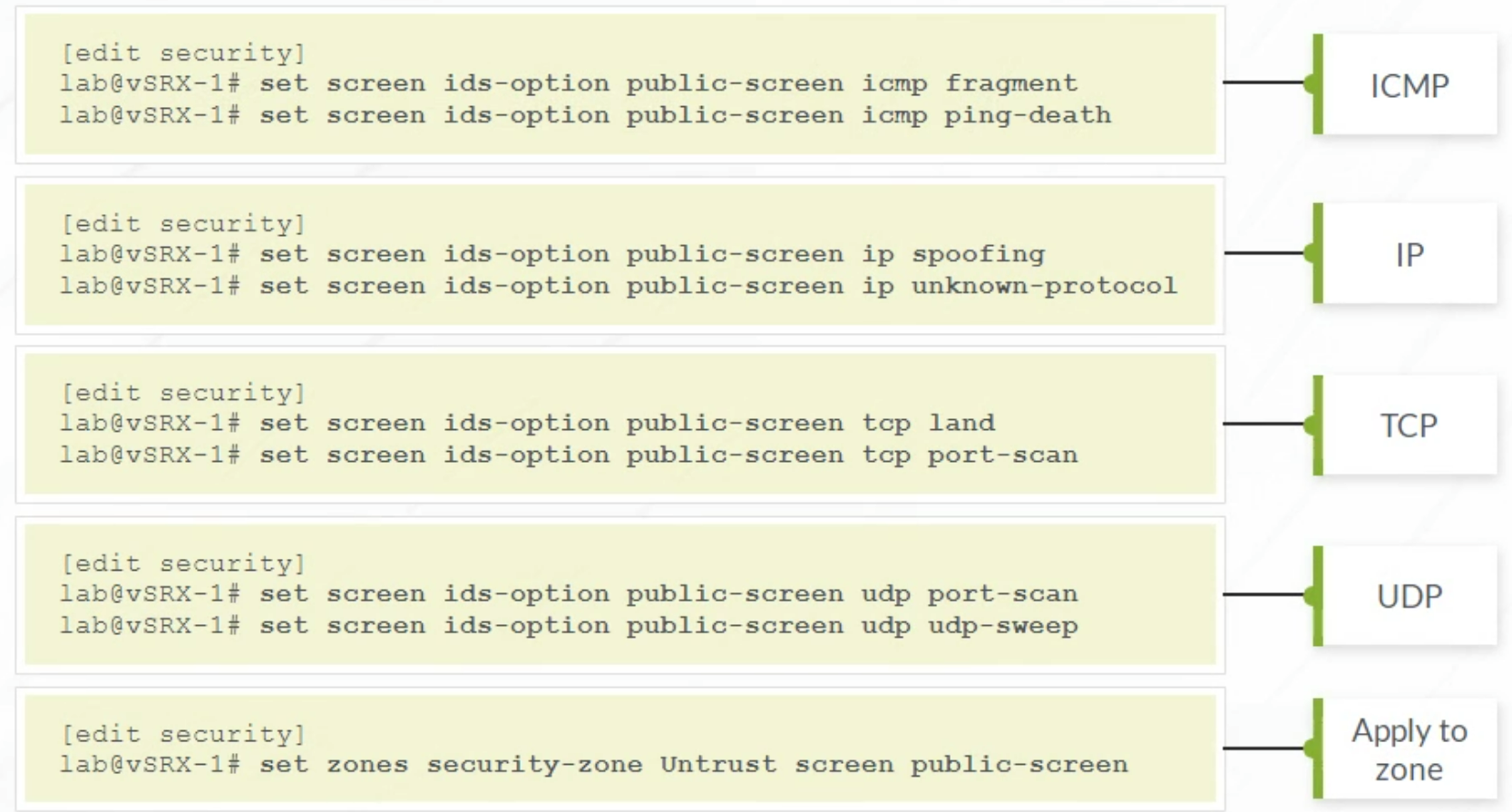
Screen Objects
Generate alarms without dropping packets.
1
| set security screen ids-option TEST alarm-without-drop
|
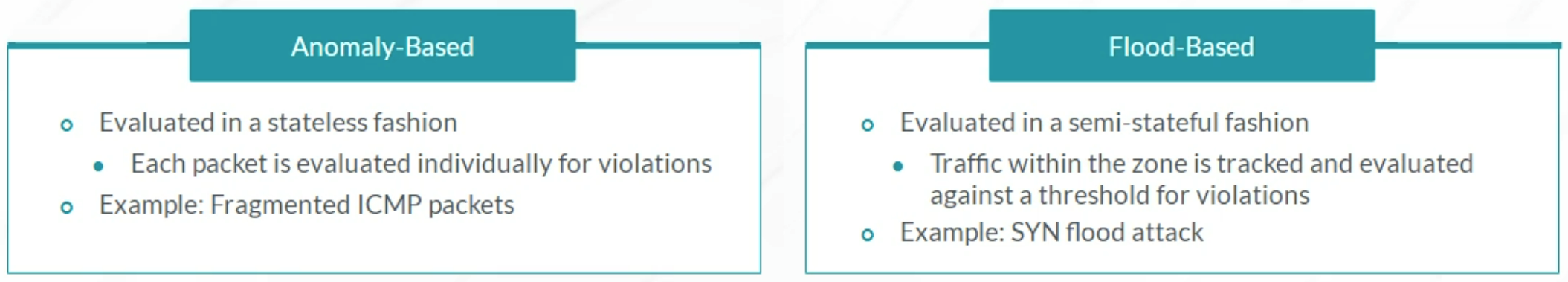
Screen Objects are evaluated only on the Ingress Zone.
Screen Types
Screen Categories
Configuring Screen Options
Address Objects
Address objects that are tied to a specific zone May only be used in security policies where the zone is referred
Define objects in a global address book to avoid duplicate entries for multiple zones Can be used by all security policies All objects must be unique
Creating Address Objects with the CLI
IP address
1
| set security address-book PRIVATE address HOST1 192.168.1.35
|
Wildcard address
1
| set security address-book PRIVATE address HOST1 wildcard-address 192.168.0.12/255.255.0.255
|
Domain name address
1
| set security address-book PRIVATE address HOST1 dns-name www.host1.com
|
Range address
1
| set security address-book PRIVATE address HOST1 range-address 192.168.1.100 to 192.168.1.150
|
To configure Global address books
1
| set security address-book global
|
1
| set security address-book TRUST_ADDRESSES description "Address objects for the trust zone" address HR-PRINTER-05 description "PRINTER IN HR BUILDING C ROOM 05" 192.168.50.45
|
Create and Address Set
1
| set security address-book TRUST_ADDRESSES address-set HR-PRINTERS address HR-PRINTER-1
|
Global Address Book attached to a specific Zone
1
| set security address-book TRUST_ADDRESSES attach zone TRUST
|
Service Objects
Display pre-defined Service Security Objects
1
| show configuration groups junos-defaults applications
|
Create Custom Applications
1
| set applications application MyFTP description "FTP with smaller timer" application-protocol ftp protocol tcp desination-port 21 inactivity-timeout 300
|
Application Sets
1
2
3
| set applications application-set access application junos-ping
set applications application-set access application junos-ssh
set applications application-set access application junos-https
|
Configuring Security Zones (LAB)
NOTE: The host-inbound-traffic interface settings overrides the host-inbound-traffic zone.
1
2
3
4
5
6
7
8
9
| set security zones security-zone UNTRUST interfaces ge-0/0/0.0
delete security zones security-zone TRUST host-inbound-traffic system-services all
set security zones security-zone TRUST host-inbound-traffic system-services ssh
set security zones security-zone TRUST host-inbound-traffic system-services https
set security zones security-zone TRUST interfaces ge-0/0/1.0
set security zones security-zone TRUST interfaces ge-0/0/1.0 host-inbound-traffic system-services telnet
set security zones security-zone DMZ interfaces ge-0/0/2.0
|
Configuring Screens (LAB)
1
2
3
4
| set security screen ids-option DMZ-SCREEN icmp large
set security zones security-zone DMZ screen DMZ-SCREEN
set security zones security-zone DMZ host-inbound-traffic system-services ping
|
1
| show security screen statistics zone DMZ
|
Configuring Global Addresses And Address Sets (LAB)
1
2
3
4
5
6
7
8
9
10
11
| set security address-book global address INTERNET-HOST 172.31.15.1/32
set security address-book DMZ-BOOK address DMZ-NET 10.10.102.0/24
set security address-book DMZ-BOOK address WebServer01 10.10.102.11/32
set security address-book DMZ-BOOK address WebServer02 10.10.102.12/32
set security address-book DMZ-BOOK address WebServer03 10.10.102.13/32
set security address-book DMZ-BOOK attach zone DMZ
set security address-book DMZ-BOOK address-set WebServerSet address WebServer01
set security address-book DMZ-BOOK address-set WebServerSet address WebServer02
set security address-book DMZ-BOOK address-set WebServerSet address WebServer03
|
Configuring Service Applications and Applications Sets (LAB)
1
2
3
4
5
6
| set applications application MY-APP protocol tcp destination-port 2020 activity-timeout 300
set applications application-set WebServerAppSet description "Applications for the Web Server"
set applications application-set WebServerAppSet application MY-APP
set applications application-set WebServerAppSet application junos-http
set applications application-set WebServerAppSet application junos-https
|
1
| run show configuration groups junos-defaults applications
|
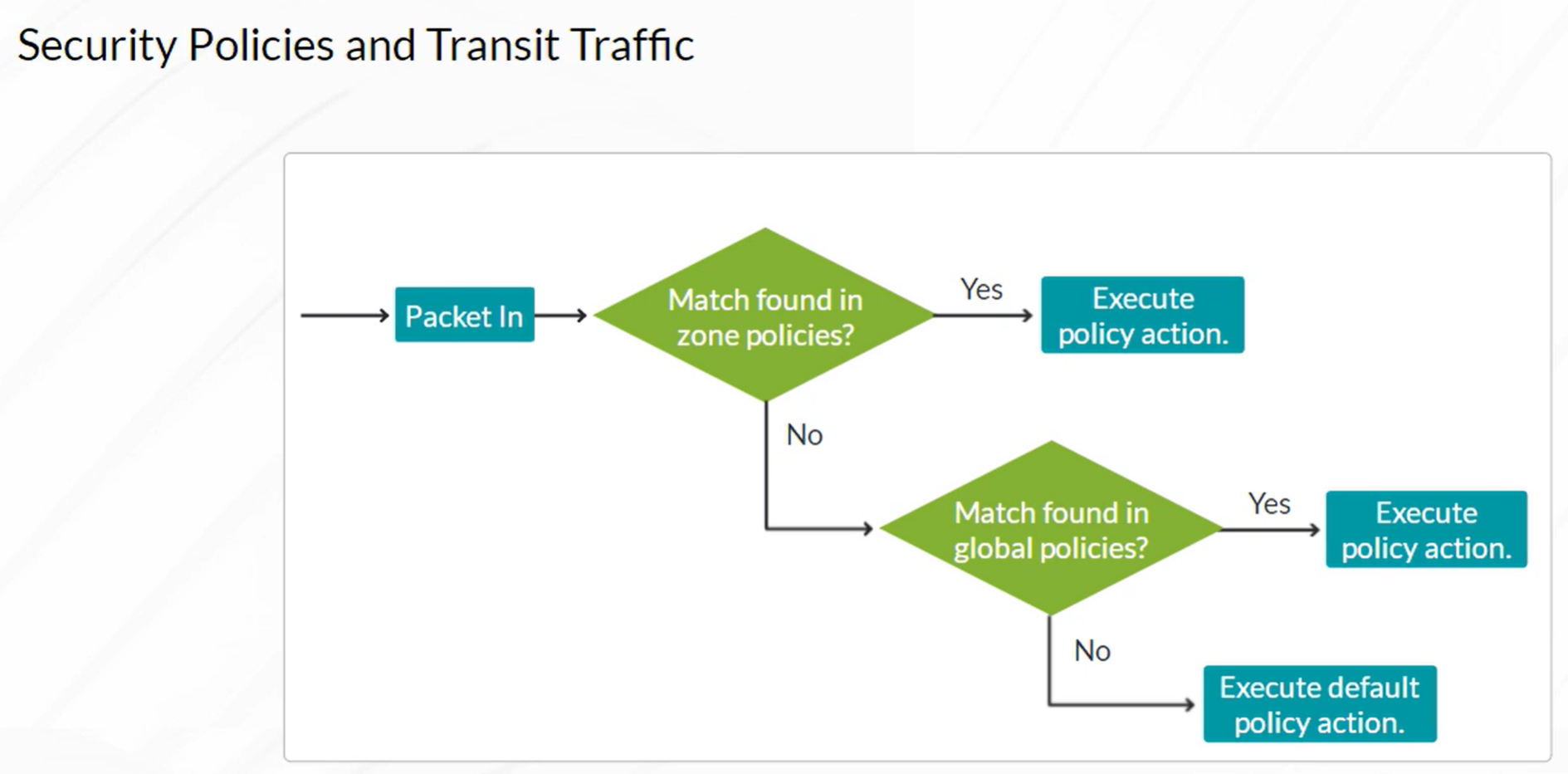
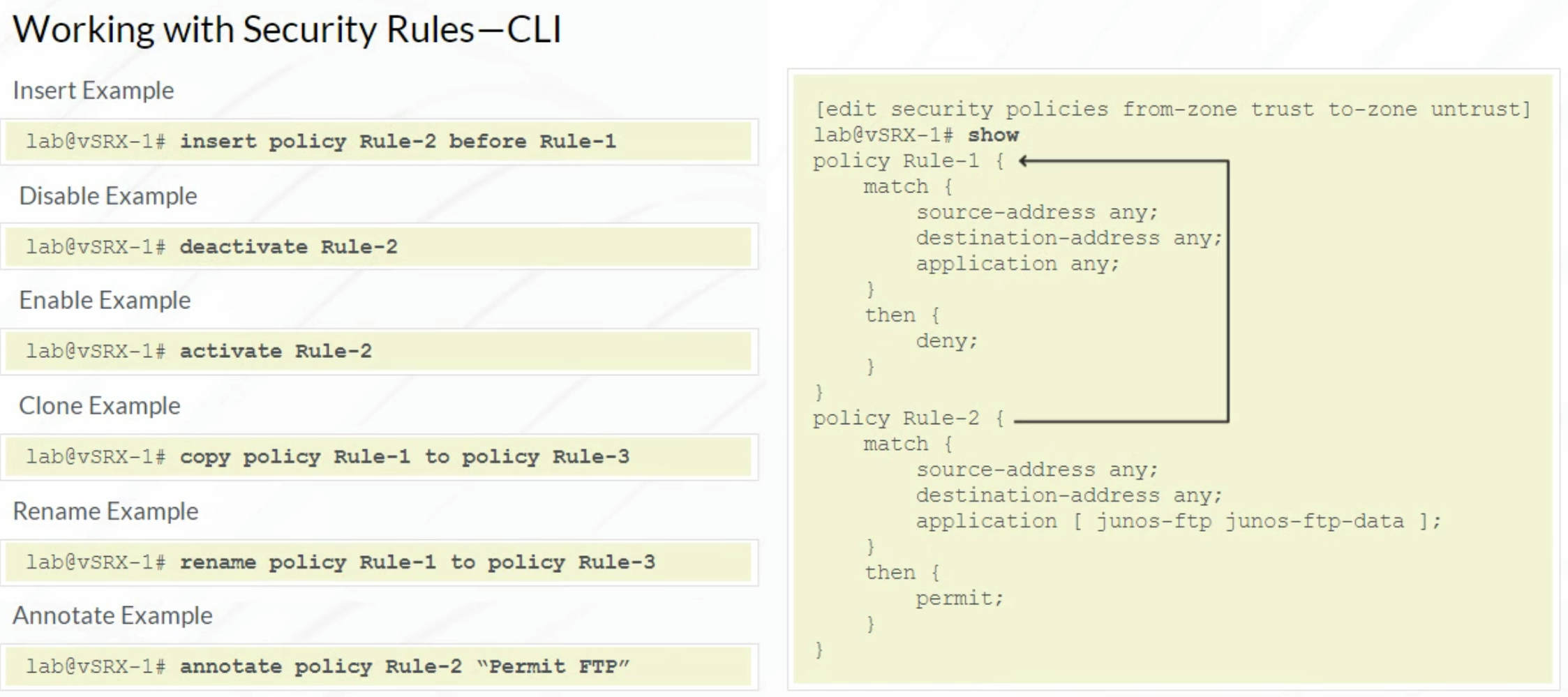
Security Policies
Security Policies are examined in the following order:
- Zone policies
- Global policies
- Default policy
Zone security policy example:
1
2
3
4
5
| set security policies from-zone UNTRUST to-zone TRUST policy POLICY-2 match source-address any destination-address any application any
set security policies from-zone UNTRUST to-zone TRUST policy POLICY-2 then deny
set security policies from-zone UNTRUST to-zone TRUST policy RULE-2 match source-address any desination-addresa any application any
set security policies from-zone UNTRUST to-zone TRUST policy RULE-2 then deny
|
Global security policy example:
1
2
| set security policies global policy GLOBAL-1 match source-address any destination-address any application any
set security policies global policy GLOBAL-1 then deny
|
Default security policy example:
Default is deny all traffic.
1
| set default-policy permit-all
|
Troubleshoot
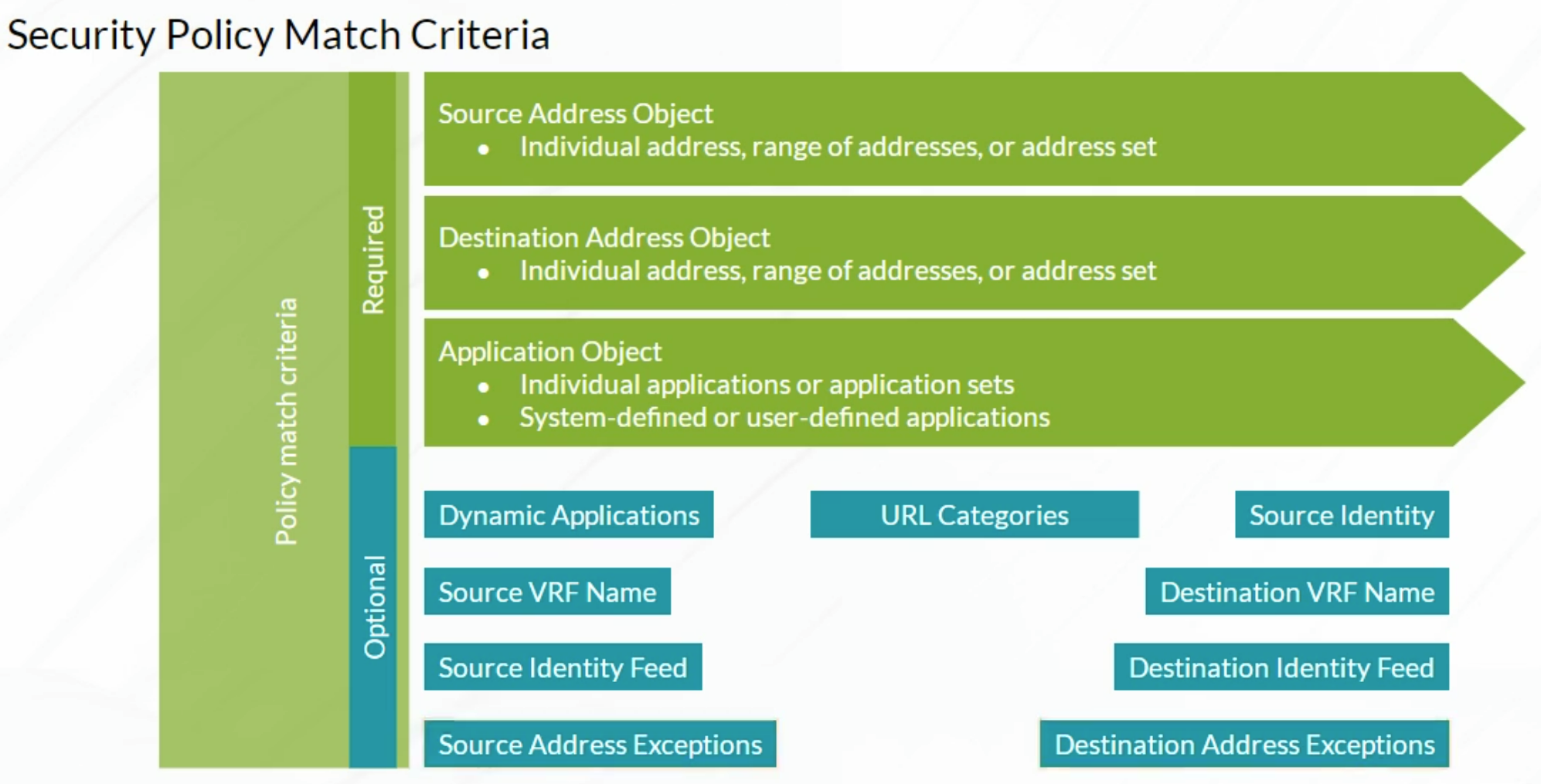
Security Policy Components
Configuring policy actions example:
1
2
3
| set security policies from-zone UNTRUST to-zone TRUST policy TEST then permit
set security policies from-zone UNTRUST to-zone TRUST policy TEST then deny
set security policies from-zone UNTRUST to-zone TRUST policy TEST then reject
|
1
2
3
4
| set security policies from-zone TRUST to-zone UNTRUST policy RULE-1 match source-address any destination-address any application any
set security policies from-zone TRUST to-zone UNTRUST policy RULE-1 then permit
set security policies from-zone TRUST to-zone UNTRUST policy RULE-1 then log session-init
set security policies from-zone TRUST to-zone UNTRUST policy RULE-1 then log session-close
|
1
2
3
4
5
| set security policies from-zone TRUST to-zonee UNTRUST policy POLICY-1 match source-address any destination-address any application any
set security policies from-zone TRUST to-zonee UNTRUST policy POLICY-1 then permit
set security policies from-zone TRUST to-zonee UNTRUST policy RULE-2 match source-address any destination-address any application [junos-ftp junos-ftp-data]
set security policies from-zone TRUST to-zonee UNTRUST policy RULE-2 then deny
|
Unified Security Policies
Example of unified security policy
1
| set security policy match source-address any destination-address any dynamic-application junos:FACEBOOK-ACCESS url-category Enhanced_Social_Web_Facebook
|
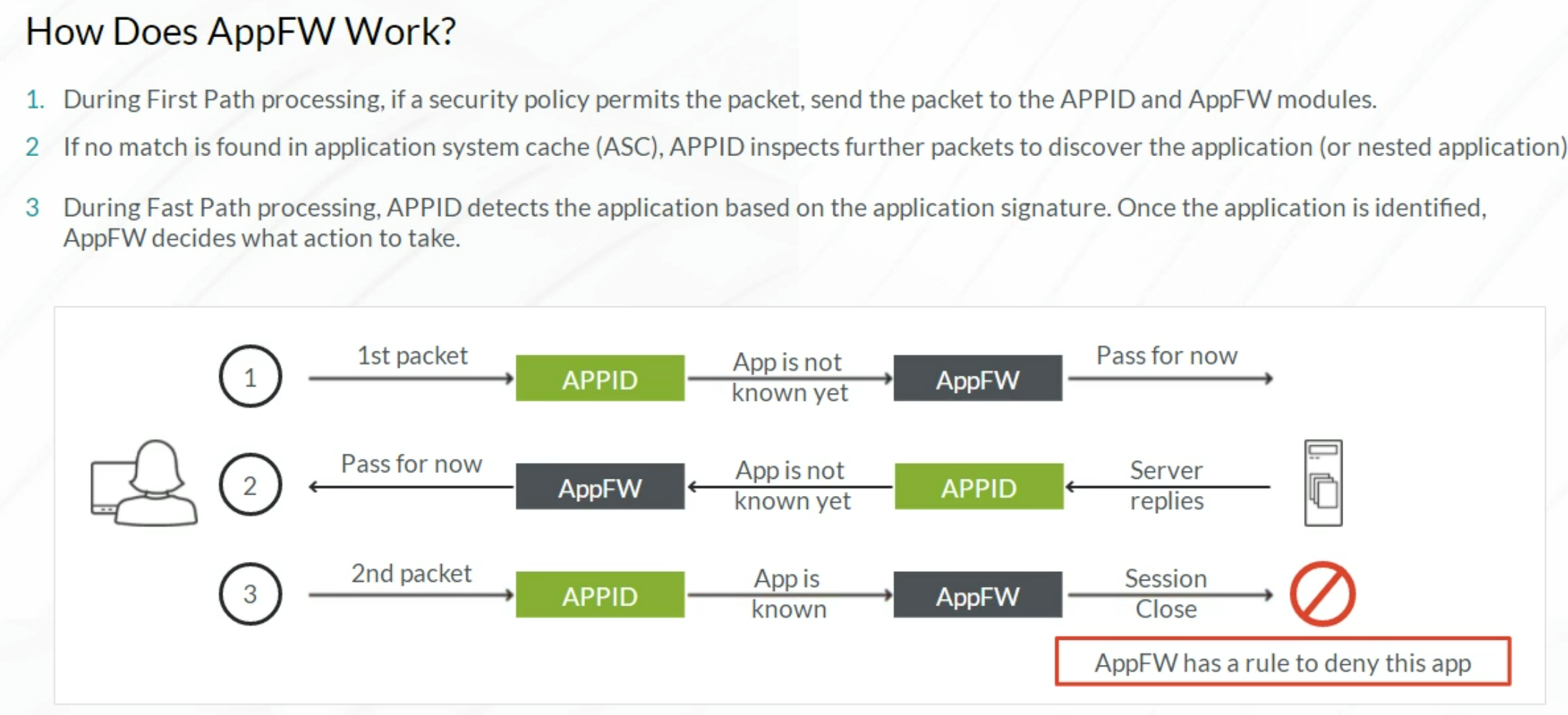
AppFW
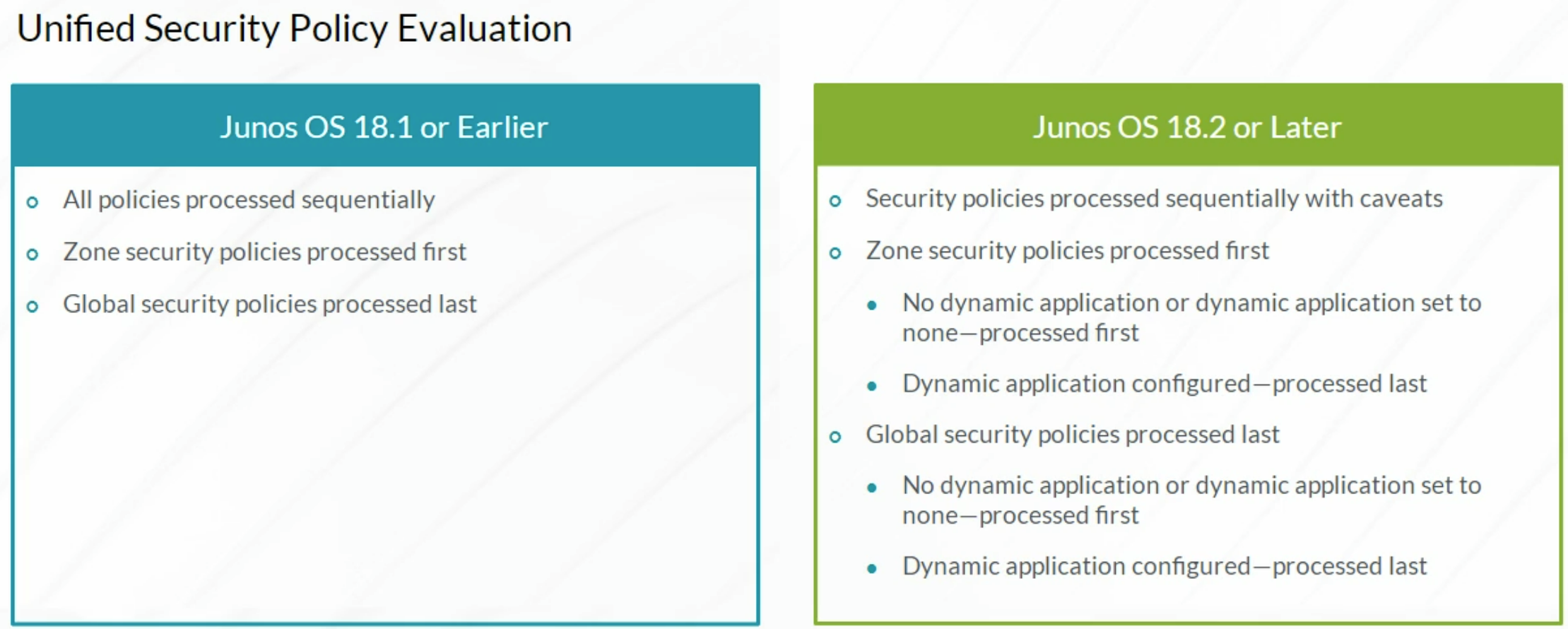
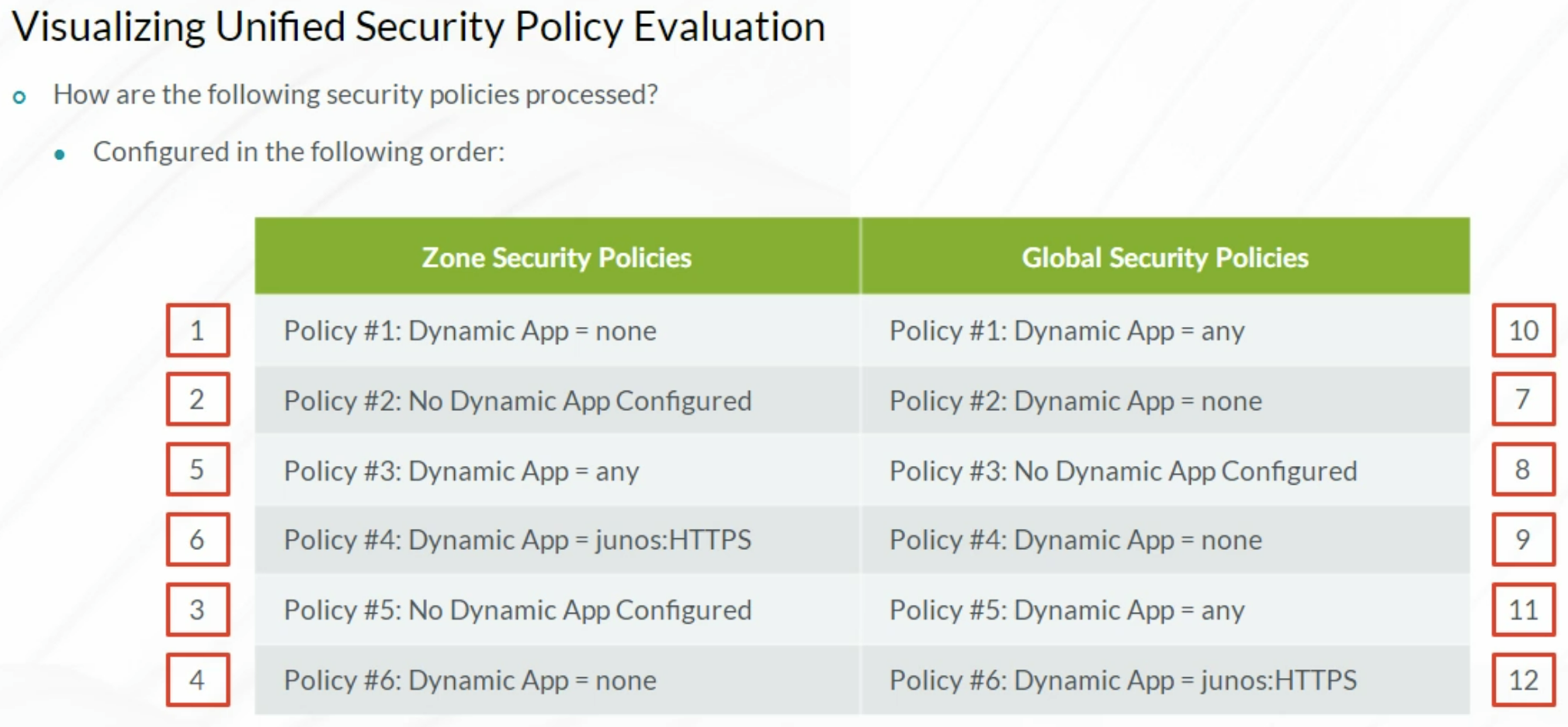
Unified Security Policy Evaluation
Configuring the Pre-ID Default Policy
1
2
| set security policies pre-id-default-policy then session-timeout icmp 4
set security policies pre-id-default-policy then log session-init
|
Configuring Security Policies
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
| edit security address-book global
set address TRUST-NET 10.10.101.0/24
set address DMZ-NET 10.10.102.2/24
top
edit security policies
edit from-zone TRUST to-zone UNTRUST policy TRUST-INTERNET-ACCESS
set match source-address TRUST-NET
set match destination-address any
set match application any
set then permit
set then count
top
edit security policies
edit from-zone TRUST to-zone DMZ policy TRUST-DMZ-ACCESS
set match source-address TRUST-NET
set match destination-address DMZ-NET
set match match application [ junos-ftp junos-ping ]
set then permit
up 1
edit policy TRUST-DMZ-BLOCK
set match source-address TRUST-NET
set match destination-address DMZ-NET
set match application junos-ssh
set then deny
set then log session-init
up 2
edit from-zone UNTRUST to-zone DMZ policy UNTRUST-DMZ-ACCESS
set match source-address any
set match destination-address DMZ-NET
set match application junos-ssh
set then permit
set then log session-init session-close
|
1
2
3
4
5
| show security policies
show security policies from-zone trust to-zone dmz
show log message | match TRUST-DMZ-BLOCK | match RT_Flow
show log message | match UNTRUST-DMZ-ACCESS | match RT_Flow
show security policies policy-name TRUST-INTERNET-ACCESS detail
|
IPS policies
Part 1: Deploying - Install License - Download and Install intrustion prevention system (IPS) signature database - Optionally, download and install policy templates
Part 2: Applying - Configure IPS policy - Policy templates can be used to assist with building a new policy - Templates can be customized - Configure security policy to send traffic for IPS evaluation
Manually download and update the signature database
1
2
3
4
| set security idp security-package url https://services.netscreen.com/cgi-bin/index.cgi
request security idp security-package download full-update
request security idp security-package download status
request security idp security-package install
|
Automatically download and update the signature database
1
2
3
| set security idp security-package url https://services.netscreen.com/cgi-bin/index.cgi
set security idp security-package automatic interval 48 start 2021-01-01.23.59.00
set security idp security-package automatic enable
|
IPS Templates and Policies
1
2
3
4
| request security idp security-package download policy-templates
request security idp security-package install policy-templates
set system scripts commit file templates.xls
set security idp active-policy recommended
|
Referencing IPS Policy
1
| set from-zone UNTRUST to-zone SERVER policy IPS-SEC then permit application-services idp-policy IPS_POLICY
|
Integraded User Firewall
Active Directory Configuration
1
2
3
4
5
6
7
| edit services user-identification active-directory-access
set authentication-entry-timeout 5
set wmi-timeout 10
set domain juniper.net user administrator password lab123
set domain juniper.net domain-controller DC1 address 172.16.10.253
set domain juniper.net user-group-mapping ldap base DC=juniper,DC=net
set domain juniper.net ip-user-mapping discovery-method wmi
|
Configure Access Profile
1
2
3
4
5
6
| set access profile LDAP-UFW authentication-order ldap
set access profile LDAP-UFW authentication-order password
set access profile LDAP-UFW ldap-options base-distinguished-name CN=Users,DC=juniper,DC=net
set access profile LDAP-UFW ldap-options search search-filter sAMAcountName=
set access profile LDAP-UFW ldap-options search admin-search distinguished-name CN=Administrator,CN=Users,DC=juniper,DC=net
set access profile LDAP-UFW ldap-options search admin-search password lab123
|
Security Policy
1
2
3
4
5
6
7
| edit security policies from-zone trust to-zone untrust policy test
set match source-address any
set match destination-address any
set match application any
set match source-identity authenticated-user
set then permit firewall-authentication user-firewall access-profile LDAP-UFW
set then permit firewall-authentication user-firewall domain juniper.net
|
Implementing Security Services (LAB)
IP Signature Database
1
| show security idp security-package-version
|
1
2
3
4
5
6
7
| set security idp security-package url <URL>
request security idp security-package download full-update
request security idp security-package download status
request security idp security-package install
request security idp security-package install status
set security idp security-package automatic enable interval 24 start-time 2021-09-15.15:30
|
IPS Policies
1
2
3
4
5
| request security idp security-package download policy-templates
request security idp security-package download status
request security idp security-package install policy-templates
request security idp security-package install status
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
| set system scripts commit file templates.xsl
show security idp
copy security idp idp-policy Recommended to idp-policy IJSEC-IPS
edit security idp idp-policy IJSEC-IPS
delete rulebase-ips rule TCP/IP
delete rulebase-ips rule ICMP
delete rulebase-ips rule FTP
delete rulebase-ips rule Malware
top
delete system scripts
edit security policies
set from-zone untrust to-zone dmz policy IPS-FW-Rule match source-address any destination-address any application any
set from-zone untrust to-zone dmz policy IPS-FW-Rule then permit application-services idp-policy IJSEC-IPS
|
Creating an Active Directory Profile
1
2
3
4
5
6
| set services user-identification active-directory-access authentication-entry-timeout 30
set services user-identification active-directory-access wmi-timeout 10
set services user-identification active-directory-access domain juniper.net user-group-mapping ldap base DC=juniper,DC=net user administrator password lab123@Lab
set services user-identification active-directory-access domain juniper.net user administrator password lab123@Lab
set services user-identification active-directory-access domain juniper.net domain-controller DC1 address 172.16.1.253
|
1
2
| show services user-identification active-directory-access domain-controller status
show services user-identification active-directory-access statistics ip-user-mapping
|
Security Policy
1
2
3
4
5
6
| ediit security policies
set from-zone Trust to-zone Server policy UserFW match source-identity authenticated-user
set from-zone Trust to-zone Server policy UserFW match source-address any
set from-zone Trust to-zone Server policy UserFW match destination-address any
set from-zone Trust to-zone Server policy UserFW match application any
set from-zone Trust to-zone Server policy UserFW then permit
|
1
| show services user-identification active-directory-access active-directory-authentication-table all
|
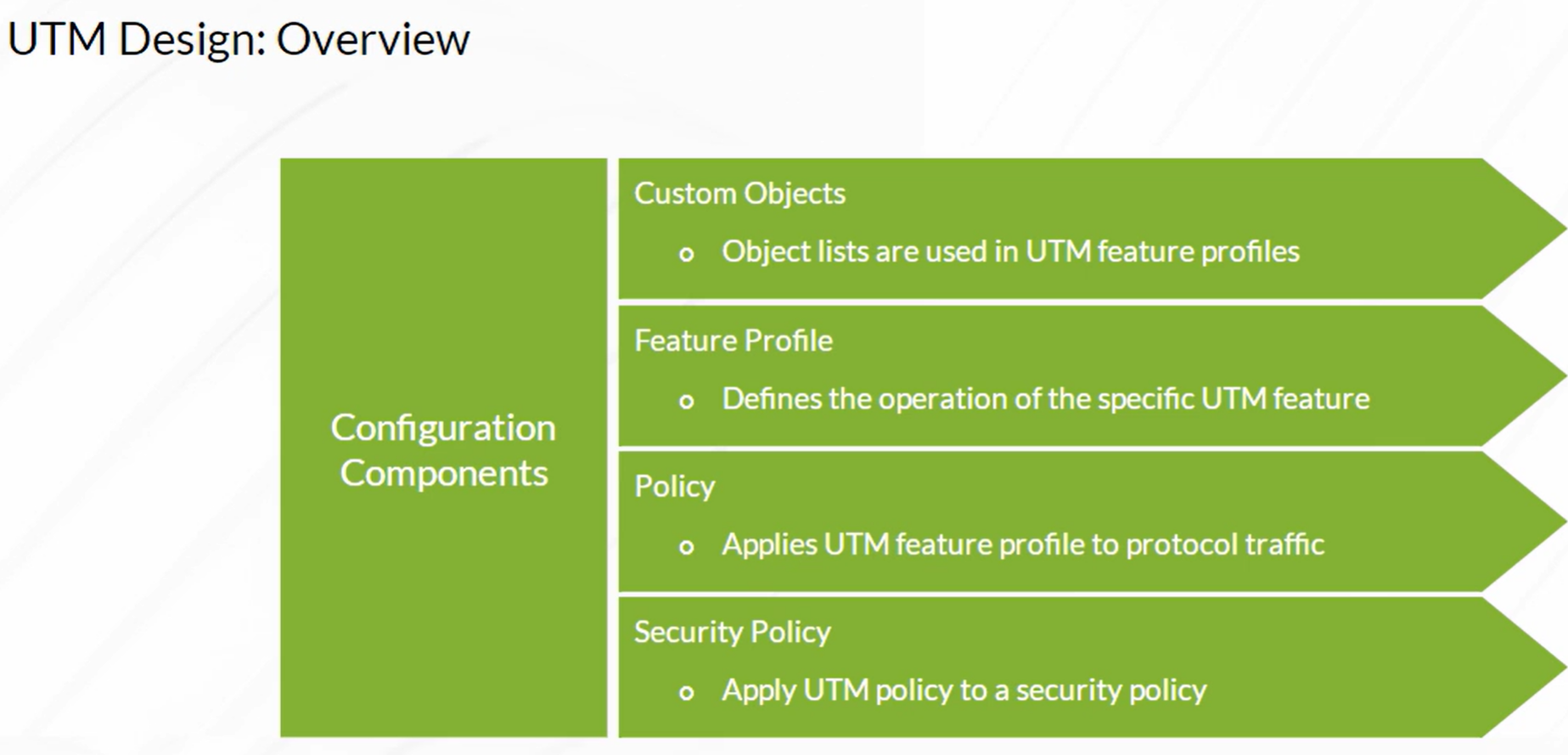
UTM (Unified Threat Management)
Create Custom Objects
1
| set security utm custom-objects url-pattern allow-list value goodcompany.com value partners.com value 90.79.129.7
|
Antispam Default Configuration
1
2
| edit security utm default-configuration
set anti-spam address-whitelist allow-list address-blacklist reject-list type sbl sbl custom-tag-string "***SPAM***" sbl-default-server spam-action tag-subject
|
Antispam Feature Profile
1
2
| edit security utm feature-profile
set anti-spam sbl profile AS-Profile-1 sbl-default-server custom-tag-string "***SPAM***" spam-action block
|
Antispamm Policy
1
2
| edit security utm
set utm-policy "Anti SPAM" anti-spam smtp-profile AS-Profile-1
|
Advanced Security Policy Settings
1
2
| edit security policies
set from-zone Trust to-zone Untrust policy AS-Policy then permit application-services utm-policy "Anti Spam"
|
Monitoring Antispam
1
2
| show security utm anti-spam status
show security utm anti-spam statistics
|
Antivirus
Creating URL Pattern Allowlist
1
2
3
| edit security utm custom-objects
set url-pattern Whilelist value *.goodsite.com value *.juniper.net value *.microsoft.com
set custom-url-category URL-Whitelist value Whitelist
|
Creating MIME Allowlist
1
2
| edit security utm custom-objects
set mime-pattern MIME-Whitelist value image/ value video/
|
Avira Antivirus Default Configuration
1
2
| edit security utm
set default-configuration anti-virus type avira-engine
|
Antivirus Feature Profile Configuration
1
2
3
4
5
| edit security utm feature-profile anti-virus
set profile AV-Profile-1 fallback-options default permit
set profile AV-Profile-1 notification-options fallback-block type message no-notify-mail-sender
set profile AV-Profile-1 notification-options fallback-non-block notify-mail-receipient custom-message "Virus Detected"
set profile AV-Profile-1 notification-options virus-detection type message notify-mail-sender custom-message "VIRUS WARNING"
|
Antivirus UTM Policy
1
2
| edit security utm
set utm-policy AV-Policy-1 anti-virus http-profile AV-Profile-1 pop3-profile AV-Profile-1
|
Security Policy Configuration
1
2
| edit security policies
set from-zone Trust to-zone Untrust policy AV-Policy then permit application-services utm-policy AV-Policy-1
|
Monitoring Antivirus
1
2
| show security utm anti-virus status
show security utm anti-virus statistics
|
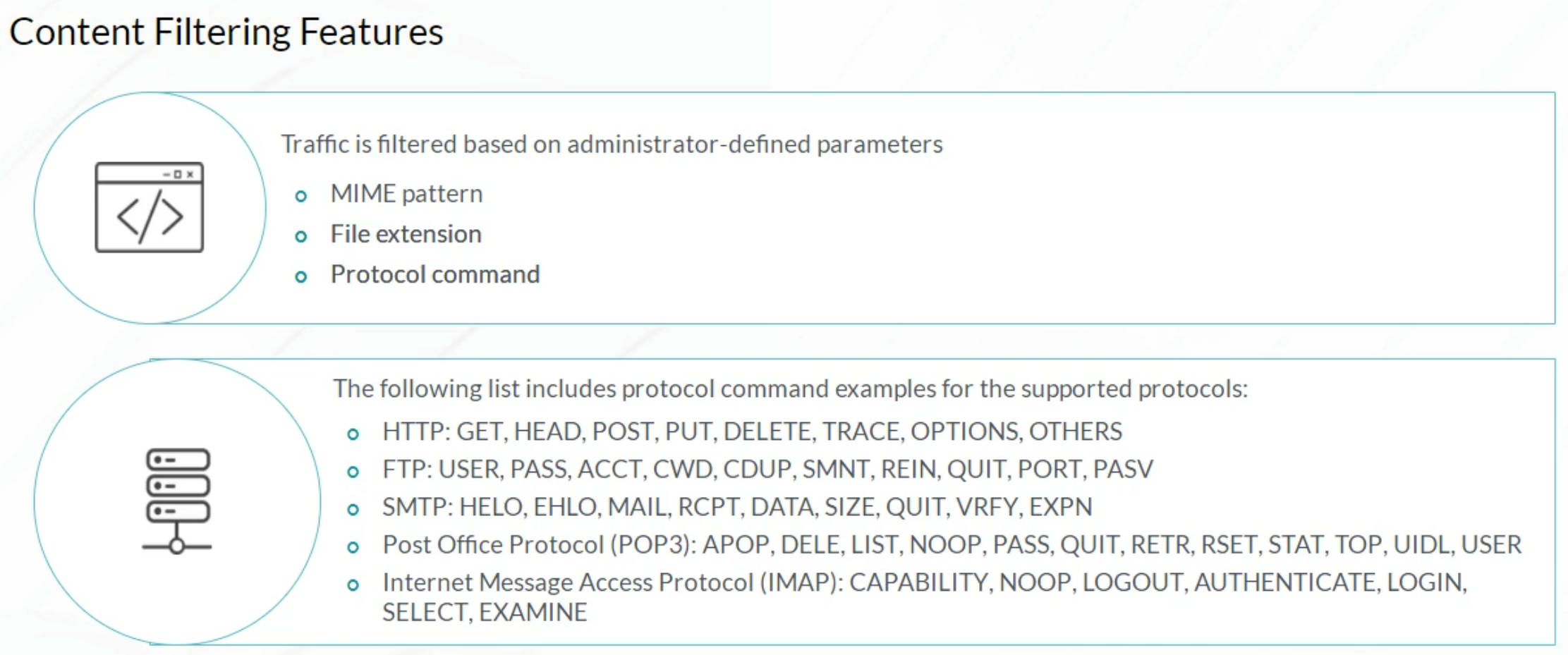
UTM: Content Filtering
Content Filtering Configuration: Custom Objects
1
2
| edit security utm default-configuration
set content-filtering block-extension junos-default-extension
|
Content Filtering Configuration: Default Options
1
2
3
| set content-filtering block-extension junos-default-extension block-mime list junos-default-bypass-mime
set content-filtering block-content-type zip exe java-applet http-cookie
set content-filtering notification-options type message custom-message "***BLOCKED***"
|
Content Filtering Configuration: Filter Profile
1
2
| edit security utm feature-profile
set content-filtering profile Content-Filter-1
|
Content Filtering Configuration: UTM Policy
1
2
| edit security utm
set feature-profile content-filtering profile Content-Filter-1
|
Content Filtering Configuration: Security Policy Configuration
1
2
| edit security policies
set from-zone Trust to-zone Untrust policy Policy-1 then permit application-services utm-policy Content-Filter-1
|
Content Filtering Verification
1
| show security utm content-filtering statistics
|
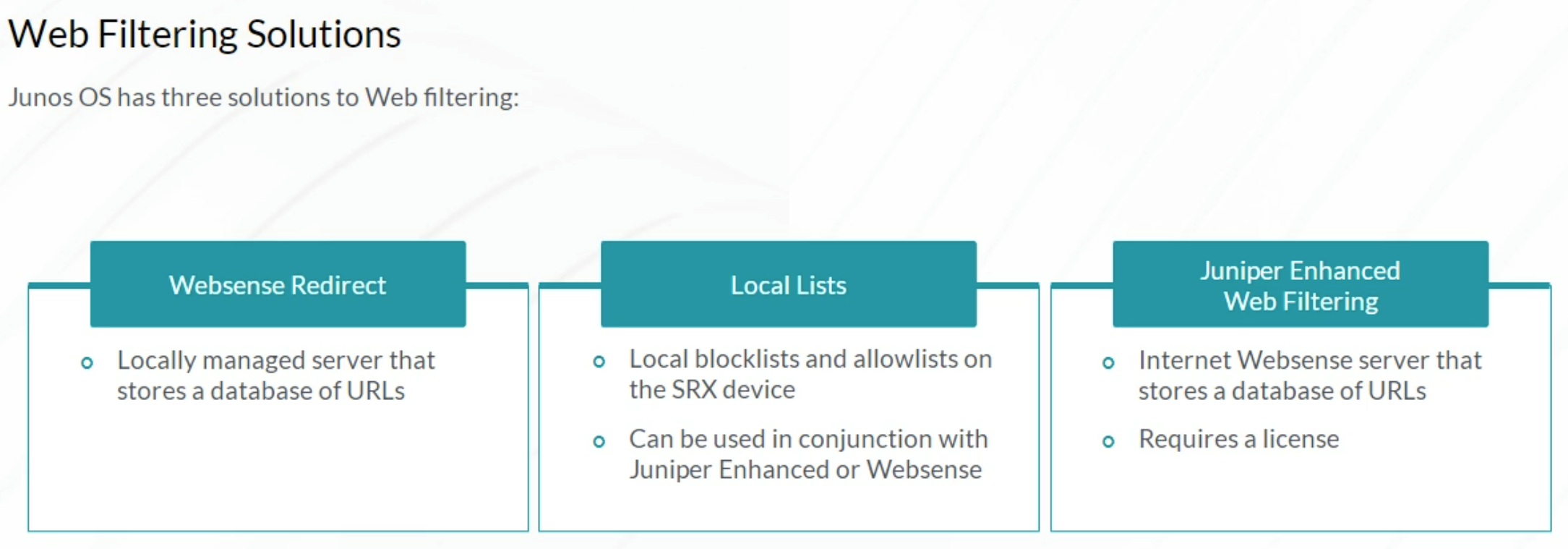
UTM: Web Filtering
Web Filtering Configuration: Custom Objects
1
2
| edit security utm
set custom-objects url-pattern Bypass-WF value *.juniper.net
|
Web Filtering Configuration: Default Options
1
2
| edit security utm
set default-configuration url-whitelist WF-Whitelist
|
Web Filtering Configuration: Filter Profile
1
2
3
4
5
| edit security utm
set feature-profile web-filtering juniper-enhanced profile WF-Profile-1 default block custom-block-message "Do not visit this website please"
set feature-profile web-filtering juniper-enhanced profile WF-Profile-1 fallback-settings default log-and-permit
set feature-profile web-filtering juniper-enhanced profile WF-Profile-1 site-reputation-action harmful block
set feature-profile web-filtering juniper-enhanced profile WF-Profile-1 category Enhanced_Gambling action block
|
Web Filtering Configuration: UTM Policy
1
2
| edit security utm
set utm-policy WF-Policy-1 web-filtering http-profile WF-Profile-1
|
Web Filtering Configuration: Security Policy
1
2
| edit security policies
set from-zone Trust to-zone Untrust policy WF-Policy then permit application-services utm-policy WF-Policy-1
|
Web Filtering Verification
1
2
| show security utm web-filtering statistics
show security utm web-filtering status
|
Working with UTM Anti-Virus (LAB)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
| edit security utm
set default-configuration anti-virus type sophos-engine
top
edit security utm feature-profile anti-virus
set profile av-profile fallback-options engine-not-ready block
set profile av-profile notification-options fallback-block type protocol-only no-notify-mail-sender custom-message "AV Fallback Block"
set profile av-profile notification-options virus-detection type protocol-only no-notify-mail-sender custom-message "VIRUS WARNING"
top
edit security utm
set utm-policy MyUTMPolicy anti-virus ftp download-profile av-profile
set utm-policy MyUTMPolicy anti-virus ?
top
edit security policies from-zone Untrust to-zone Server
set policy Untrust-Server then permit application-services utm-policy MyUTMPolicy
|
1
2
| show security utm anti-virus status
show security utm anti-virus statistics
|
Working with UTM Web Filtering (LAB)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
| edit security utm custom-objects
set url-pattern whitelist value http://utmserver.utm.juniper.net/good.html
set url-pattern blacklist value http://utmserver.utm.juniper.net/bad.html
set custom-url-category bad value blacklist
set custom-url-category good value whitelist
top
edit security utm default-configuration web-filtering
set url-whitelist good
set url-blacklist bad
set type juniper-local
set juniper-local custom-block-message "This site is not allowed!"
top
edit security utm feature-profile web-filtering juniper-local
set profile WebFilterPolicy default permit custom-block-message "This site is not allowed!"
top
edit security utm utm-policy MyUTMPolicy
set web-filtering http-profile WebFilterPolicy
|
1
| show security utm web-filtering statistics
|
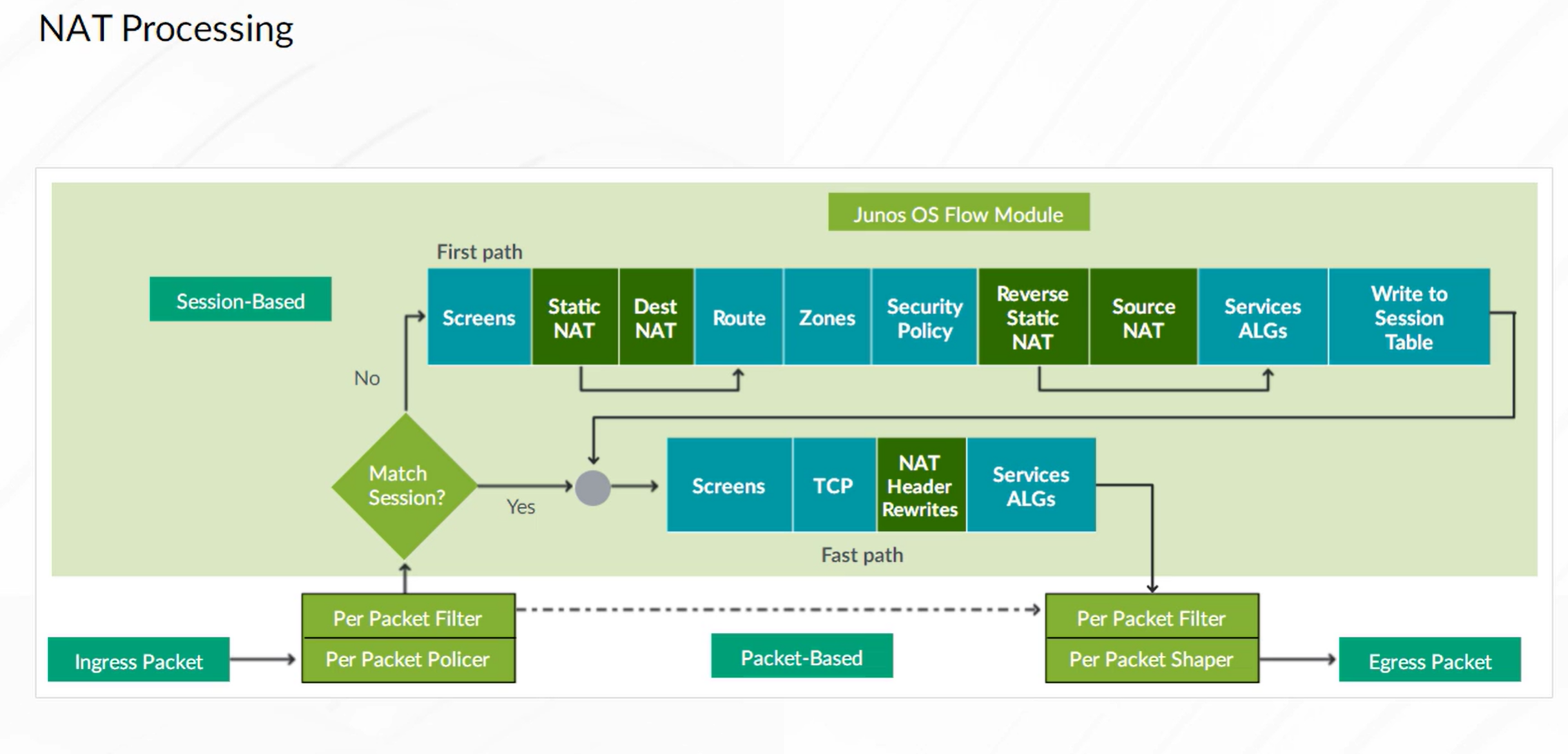
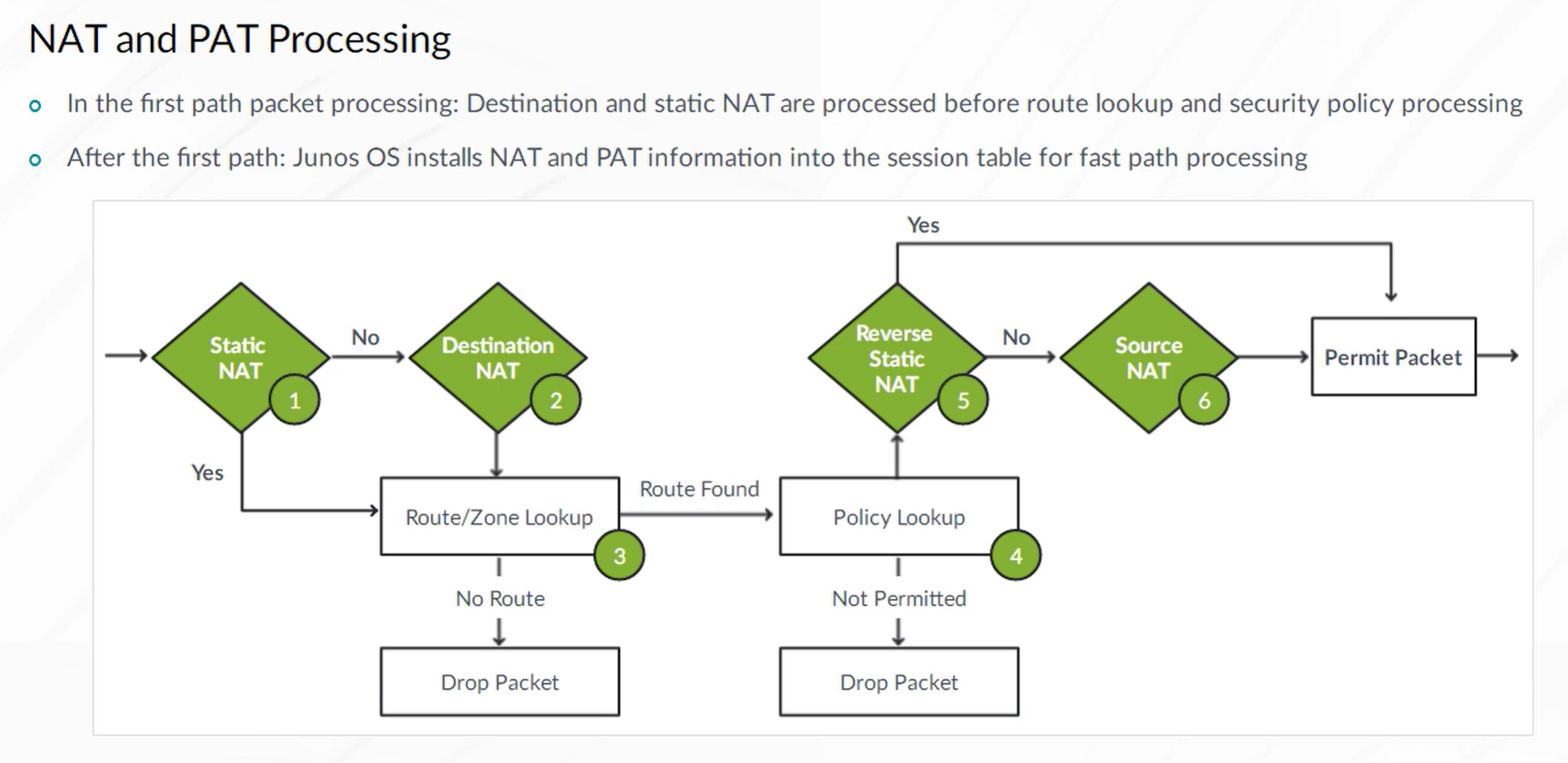
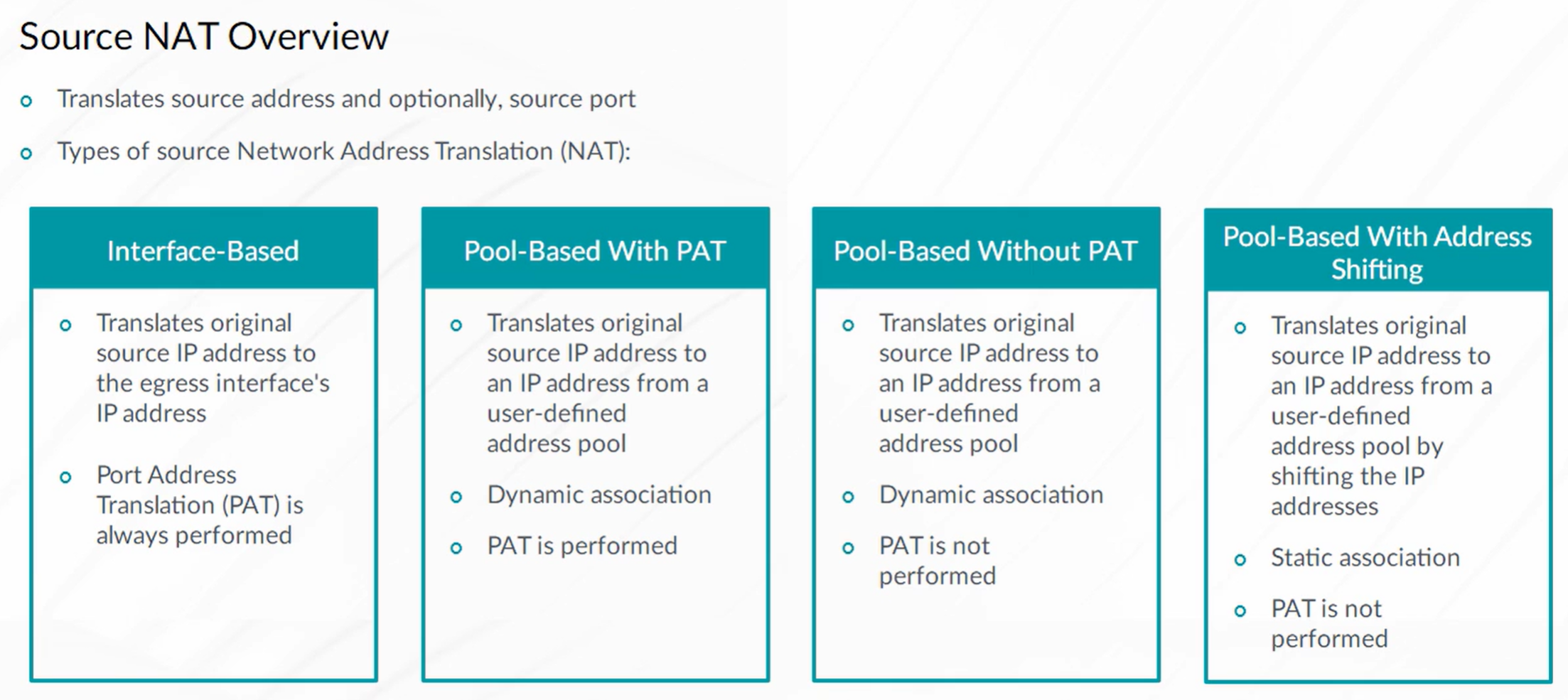
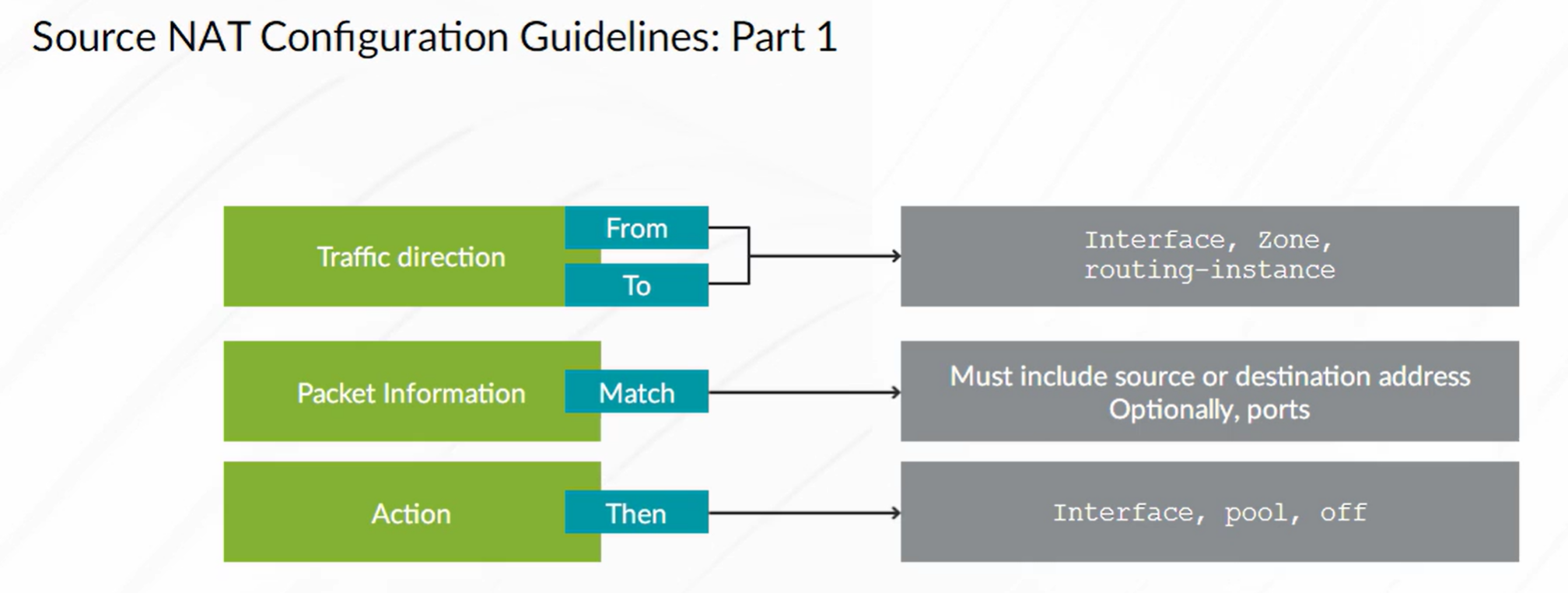
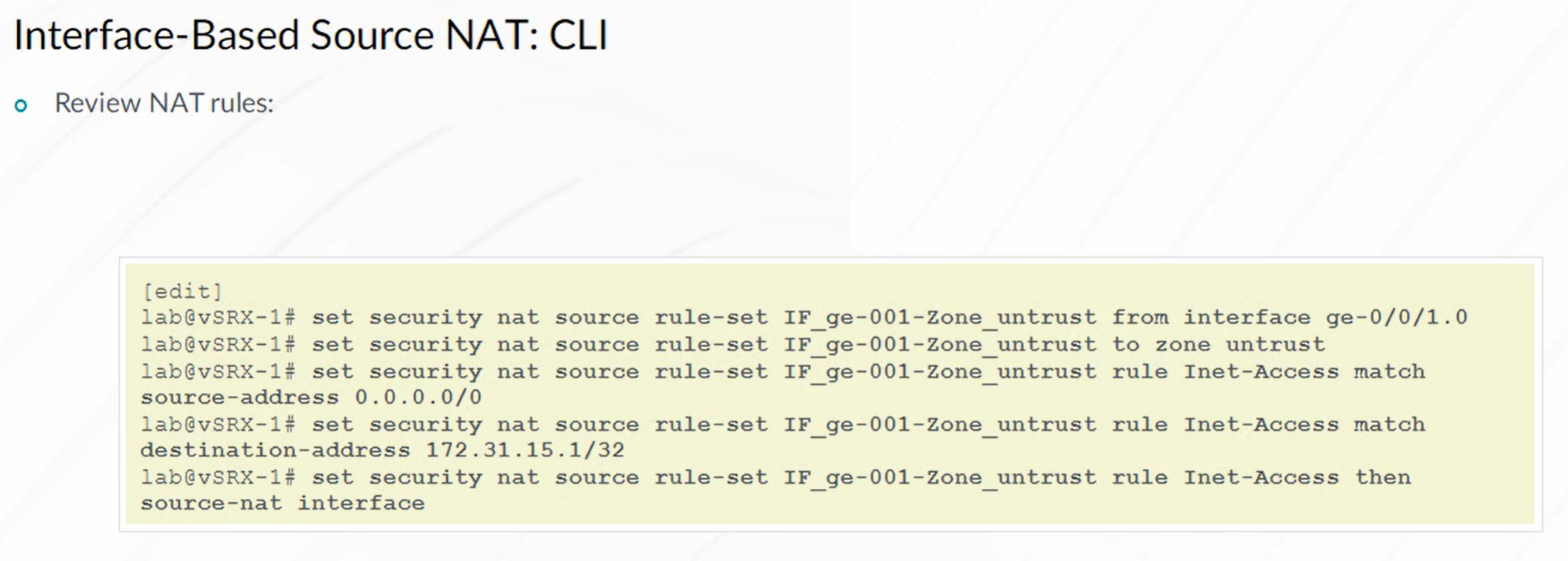
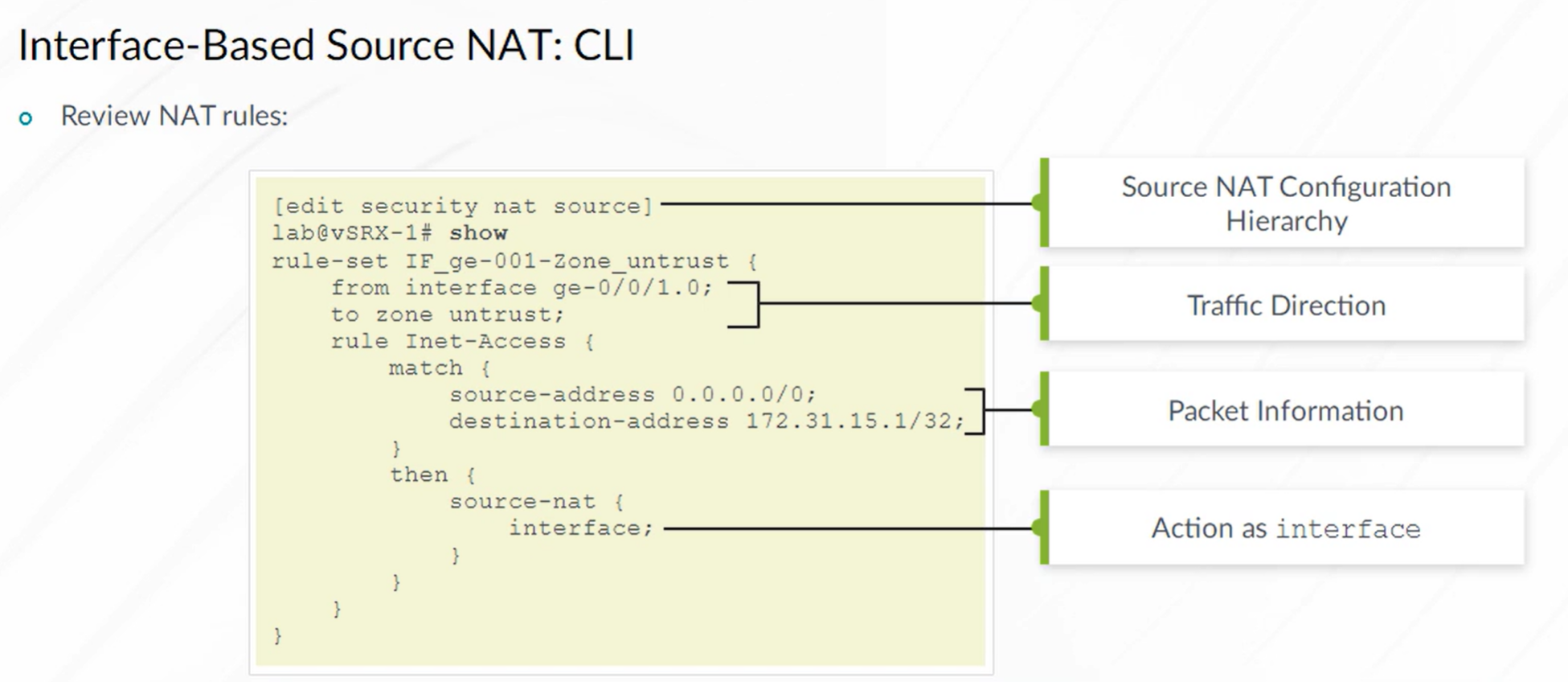
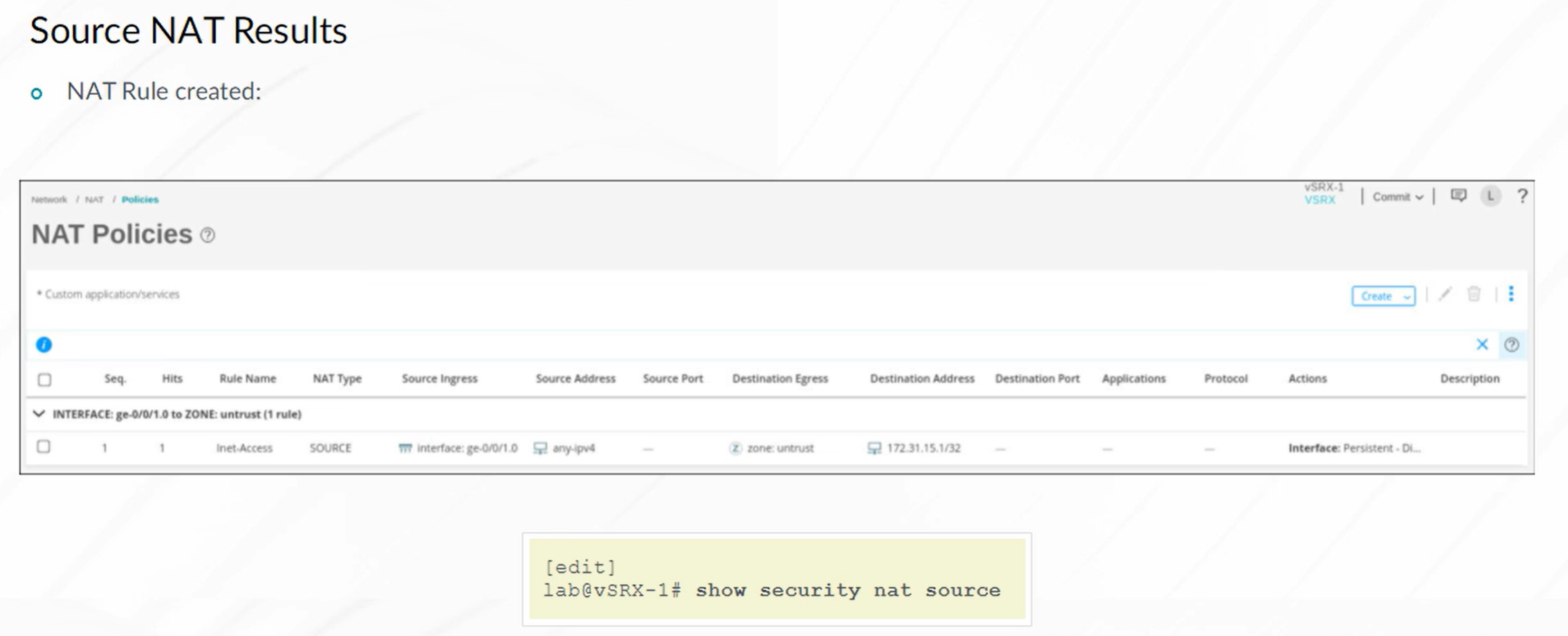
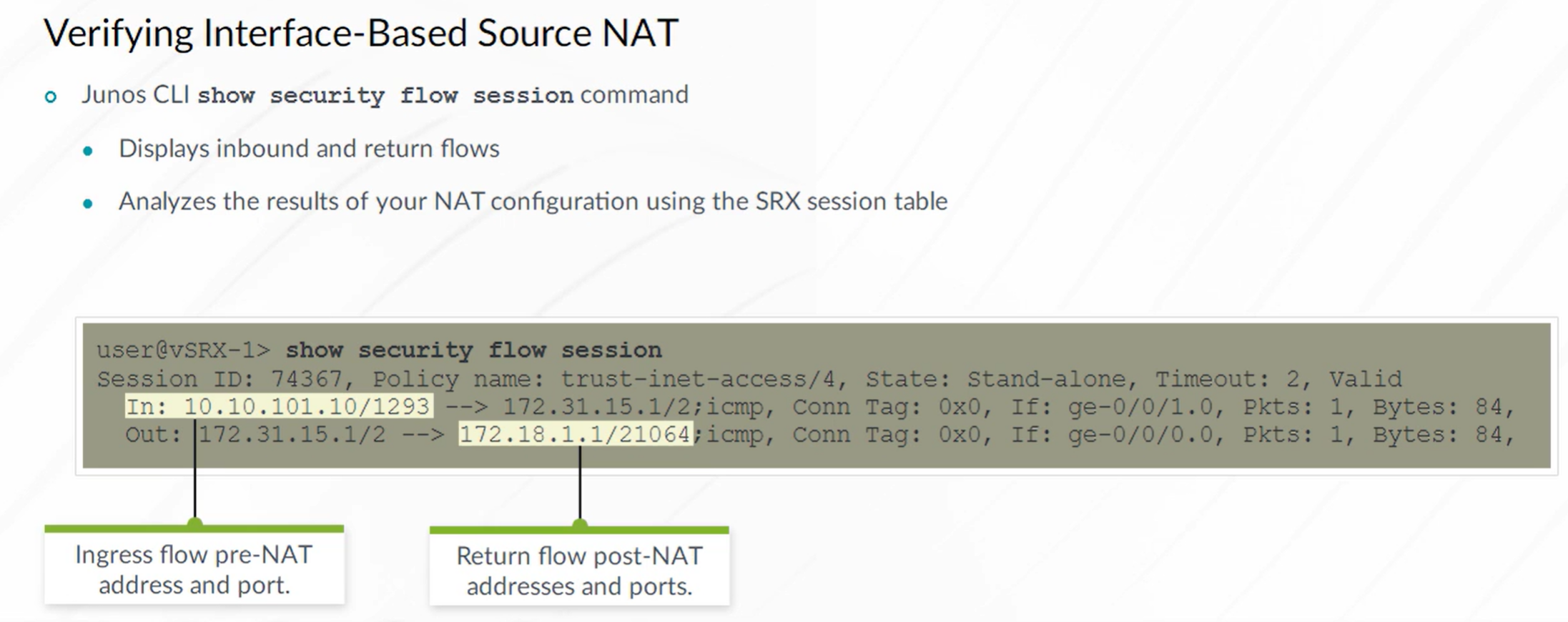
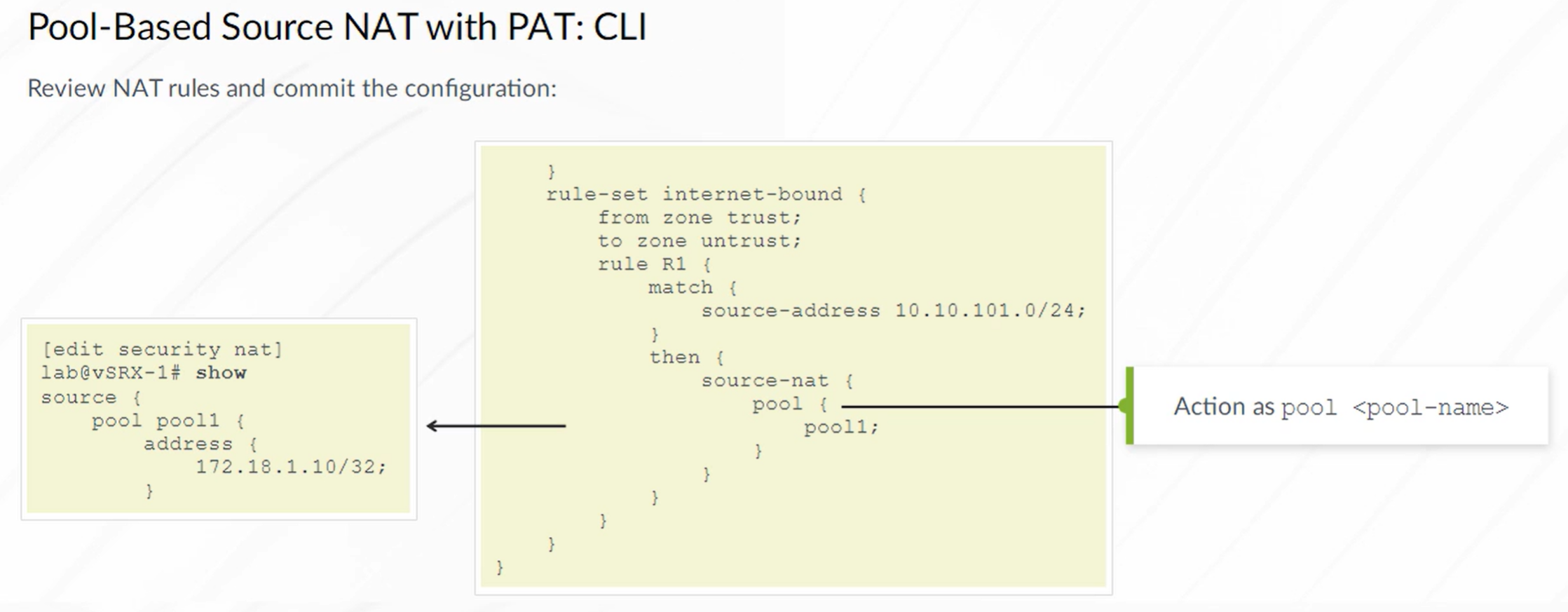
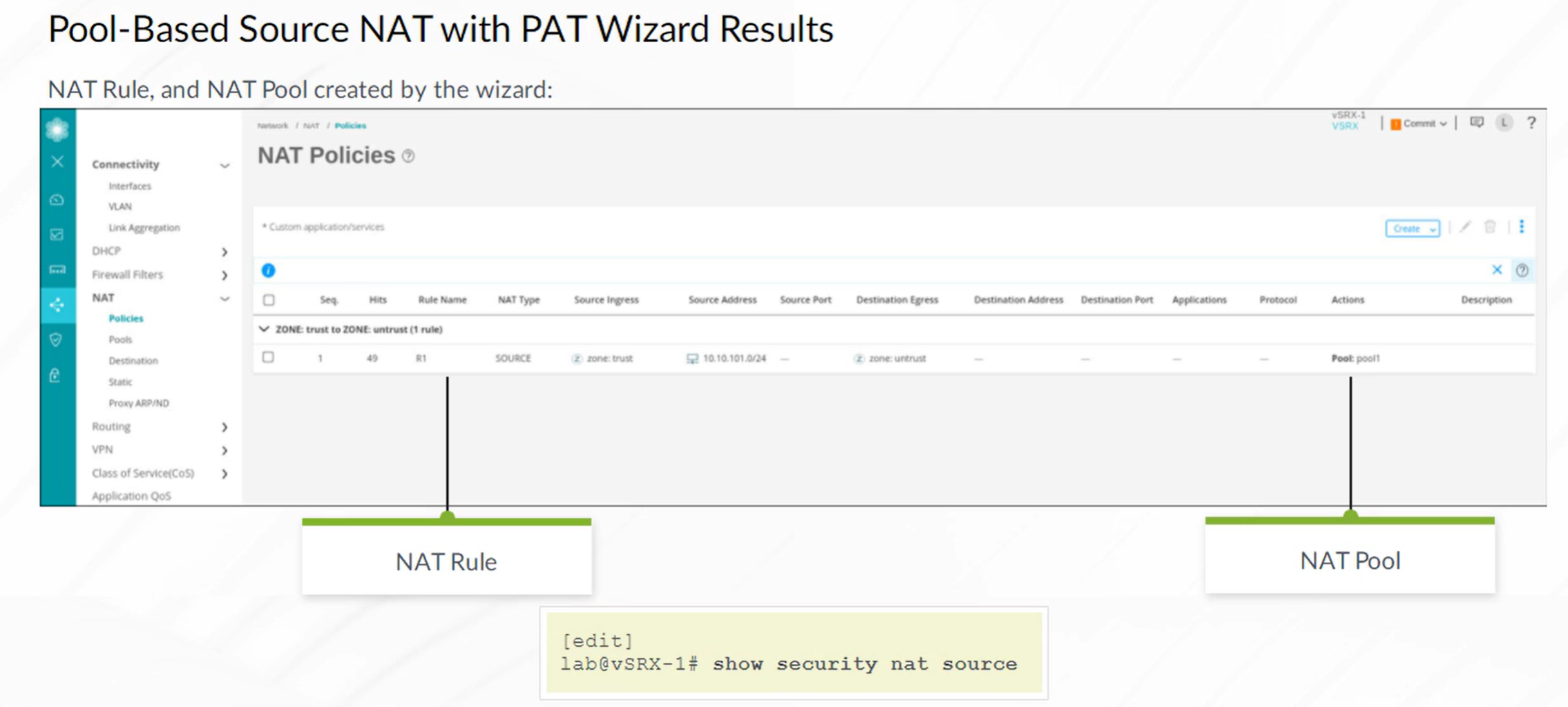
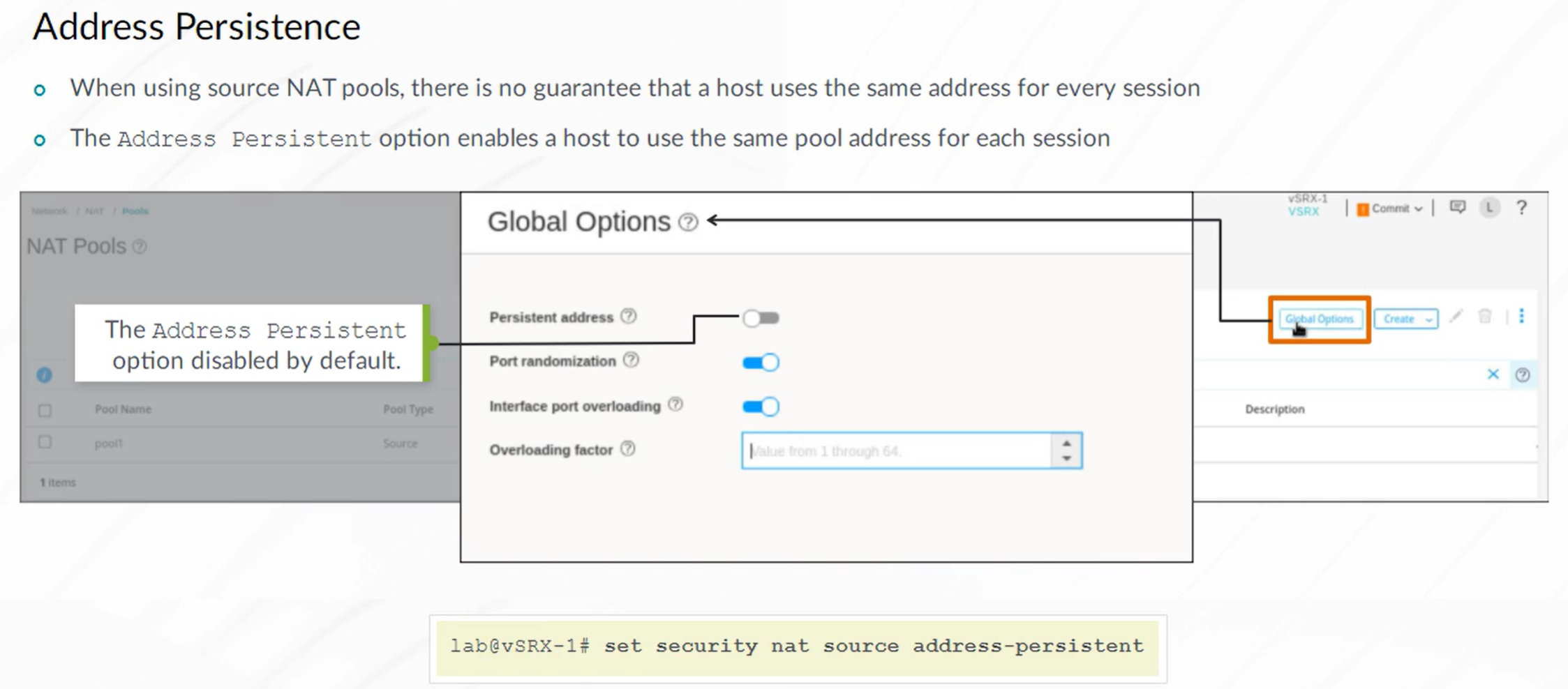
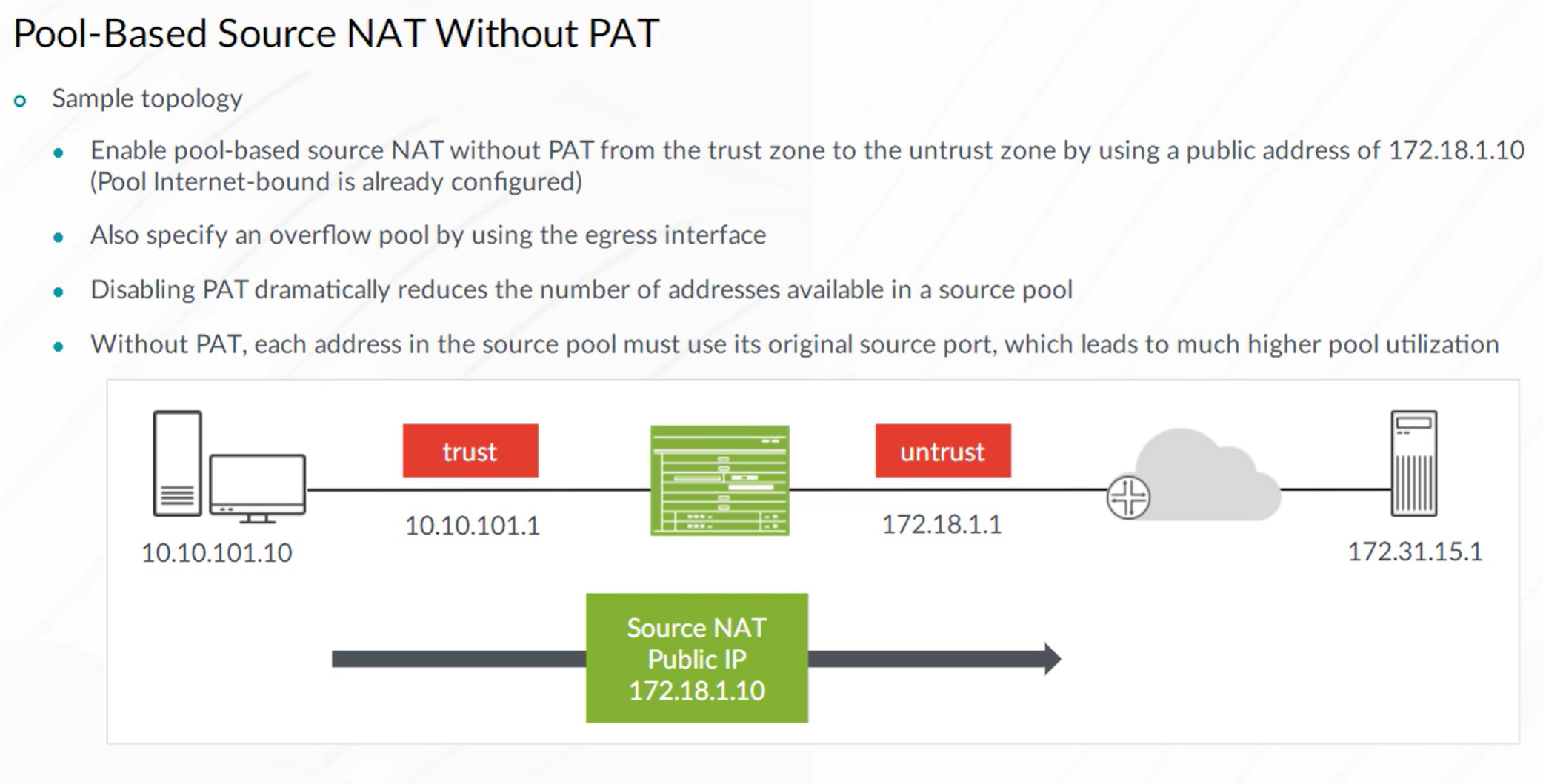
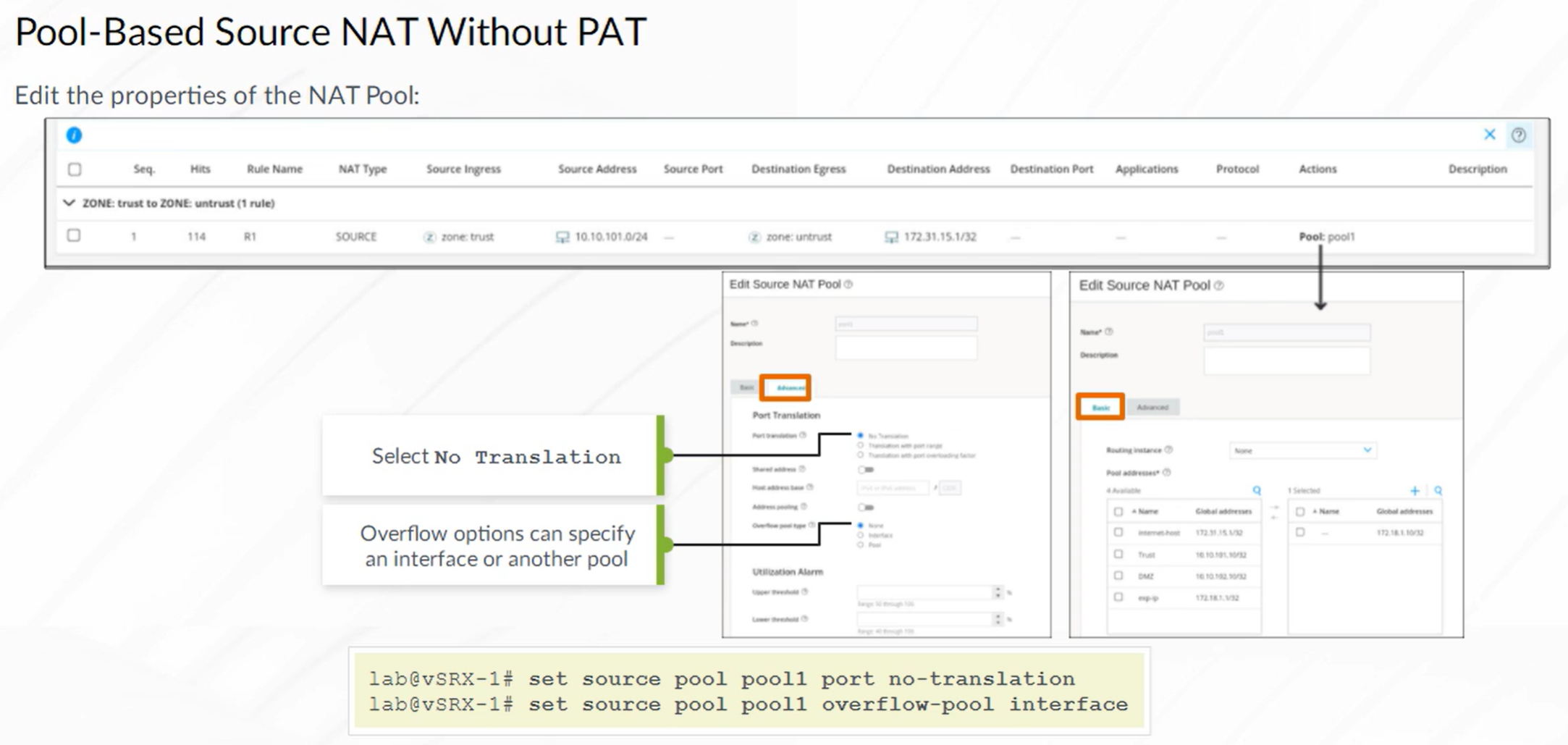
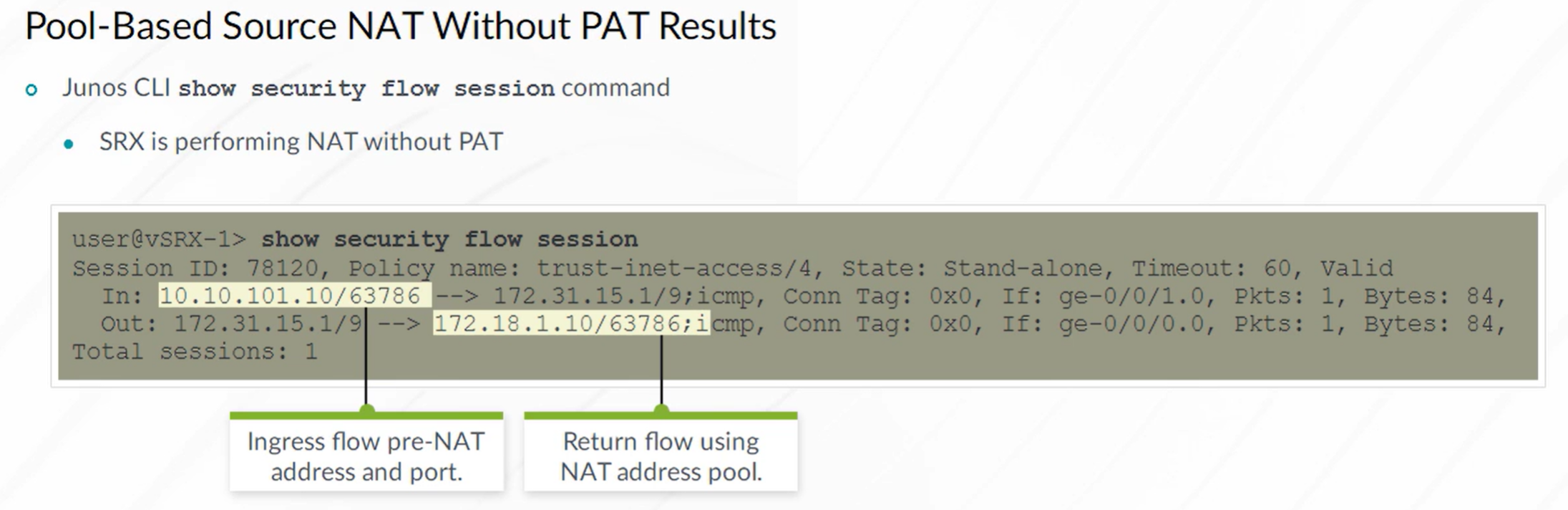
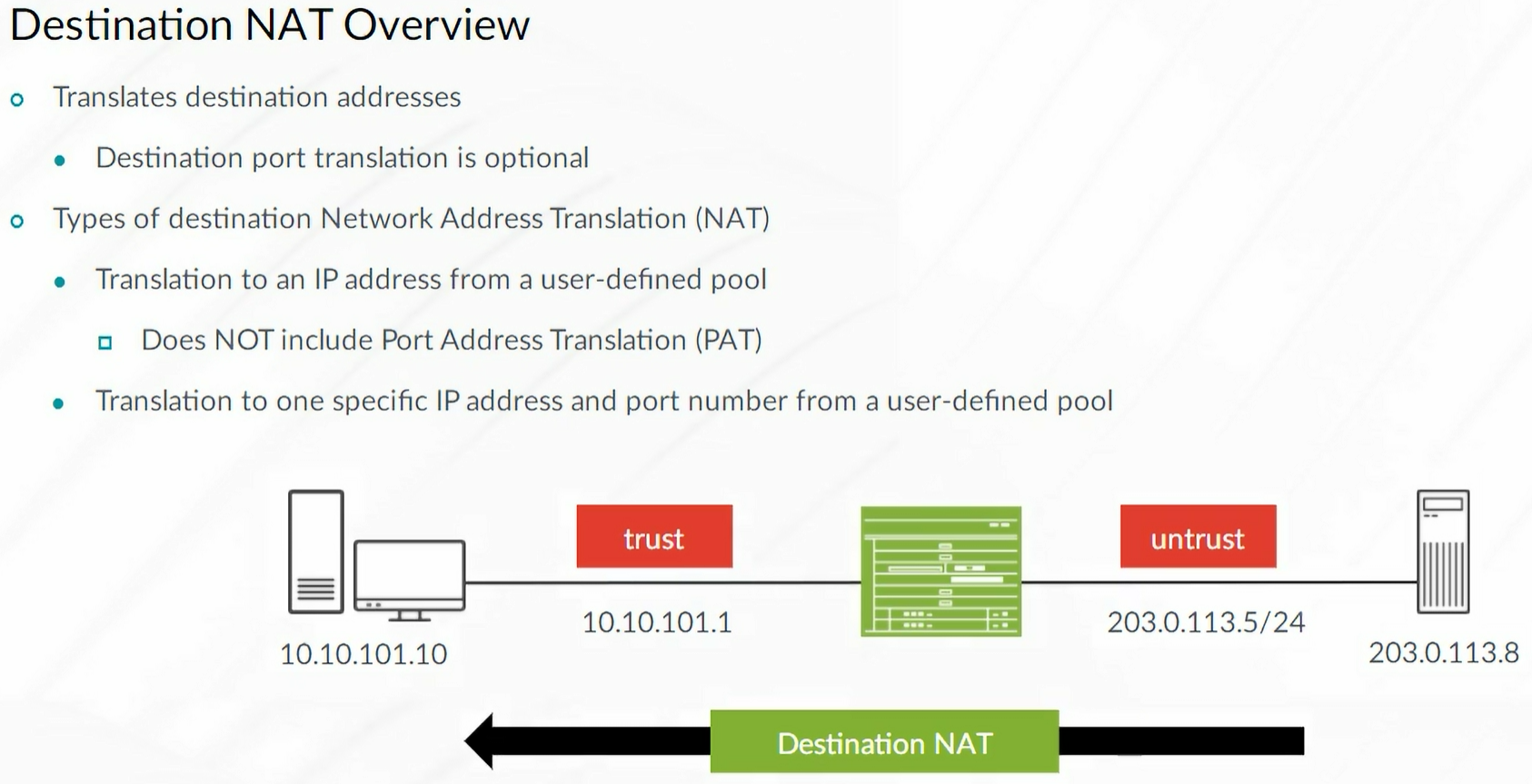
Source NAT
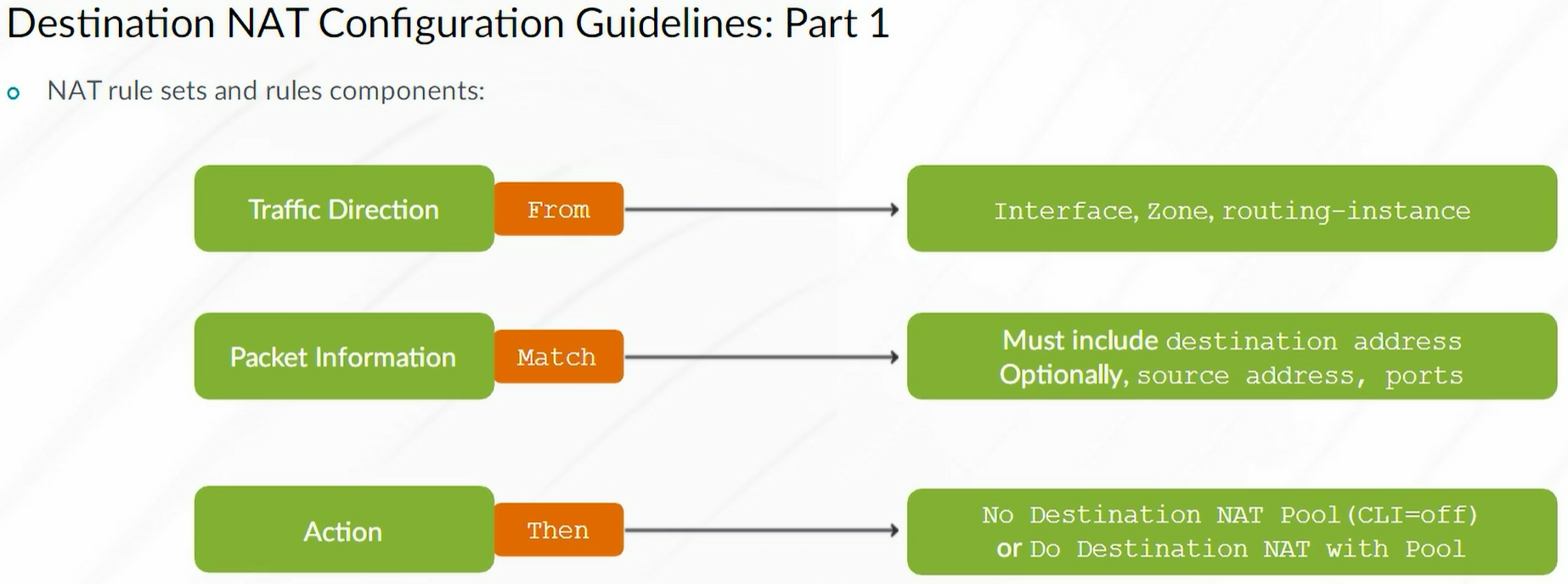
Destination NAT
Main use case is allow a device on the Internet to connect to an internal device behind NAT.
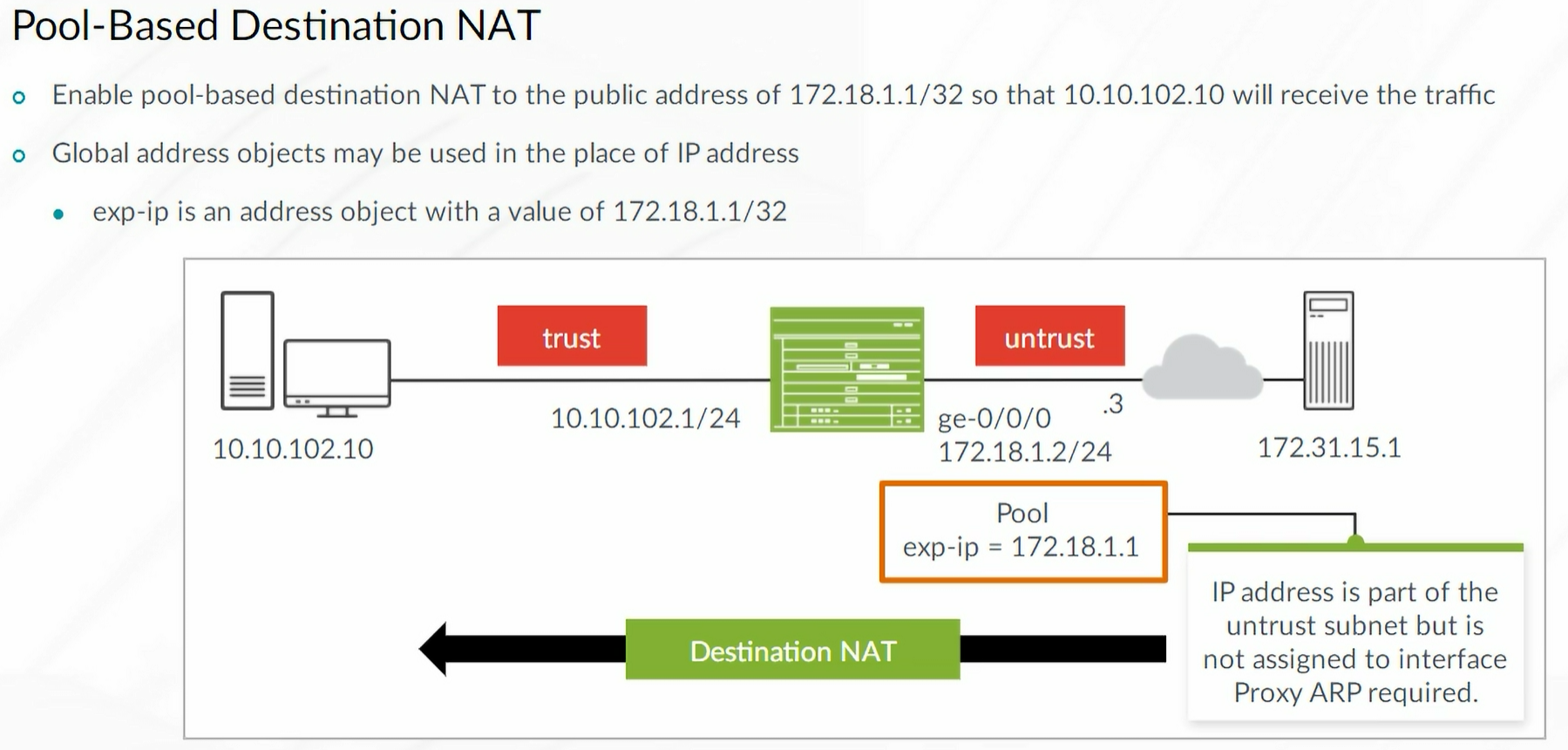
Destination NAT example:
1
2
3
4
5
| set security nat destination pool WEB-SERVER-POOL address 10.10.102.10/32
set security nat destination rule-set WEB-SERVER from zone unstrust
set security nat destination rule-set WEB-SERVER rule WEB-SERVER-ACCESS match source-address 0.0.0.0/0
set security nat destination rule-set WEB-SERVER rule WEB-SERVER-ACCESS match destination-address-name EXP-IP
set security nat destination rule-set WEB-SERVER rule WEB-SERVER-ACCESS then destination-nat pool WEB-SERVER-POOL
|
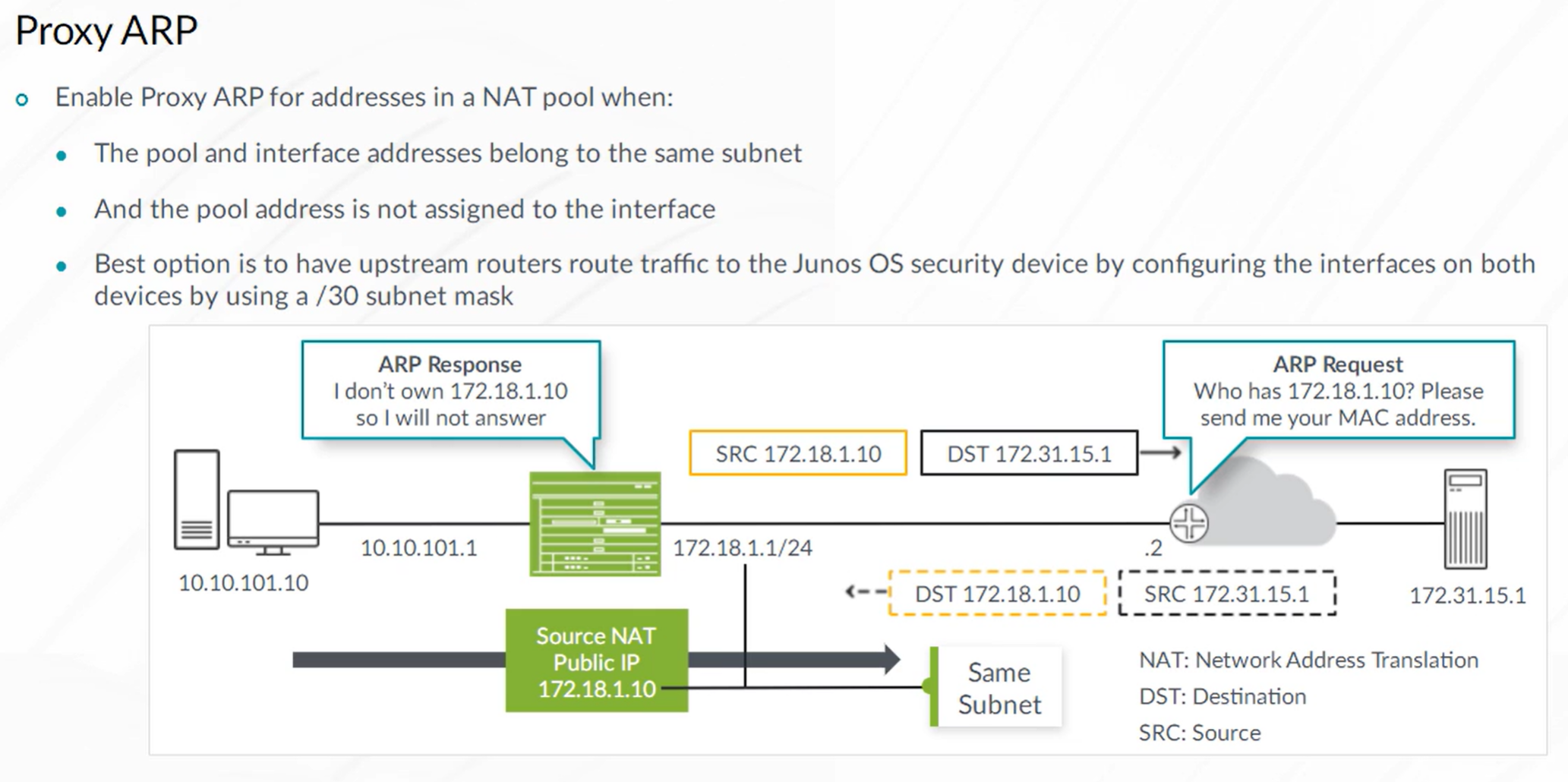
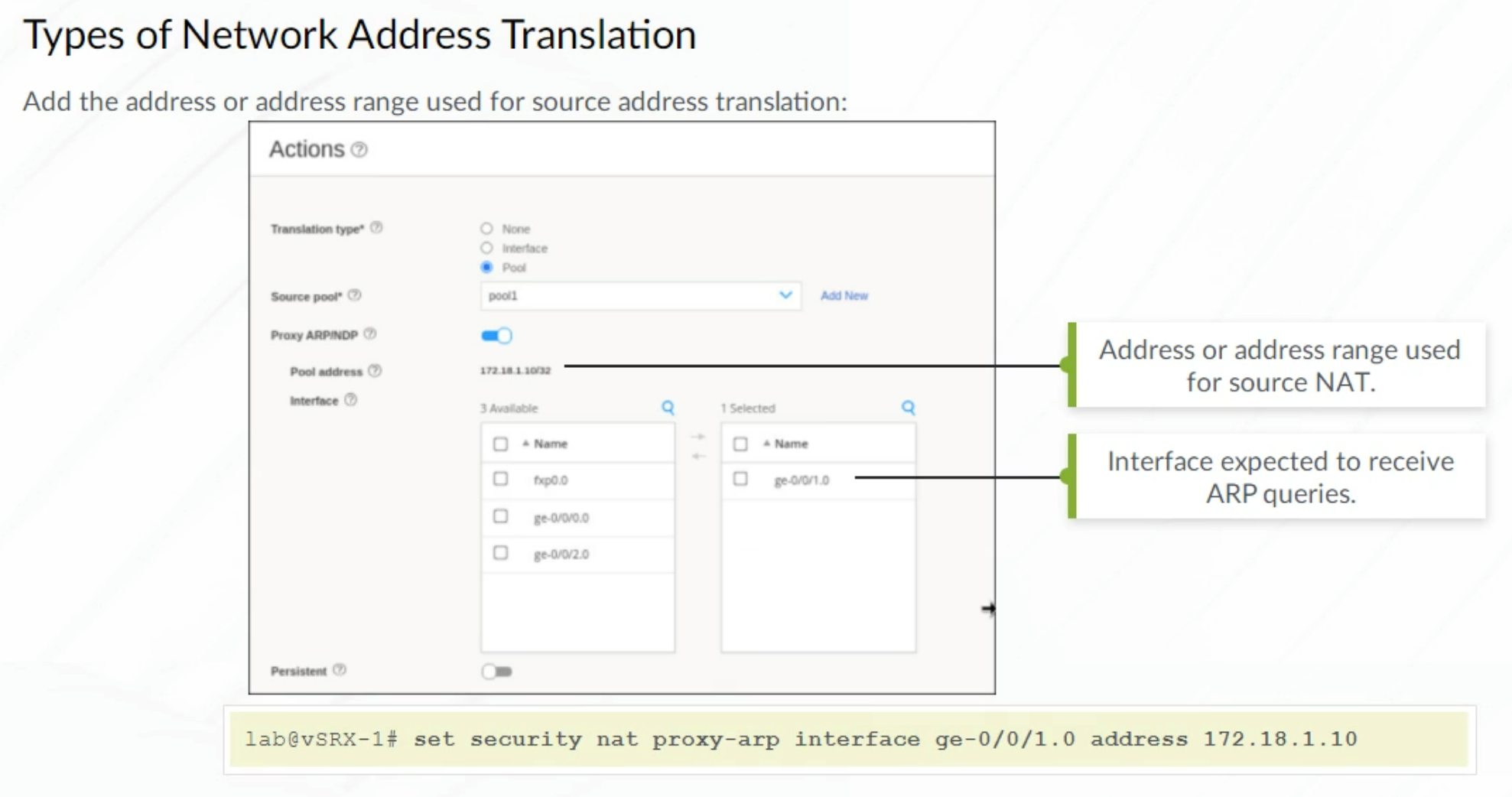
Proxy ARP must be configured to enable the device to respond to ARP queries for the destination NAT IP address.
Note: Only required when both the interface IP network and NAT IP are on the same subnet
1
| set security nat proxy-arp interface ge-0/0/0 address 172.18.1.1
|
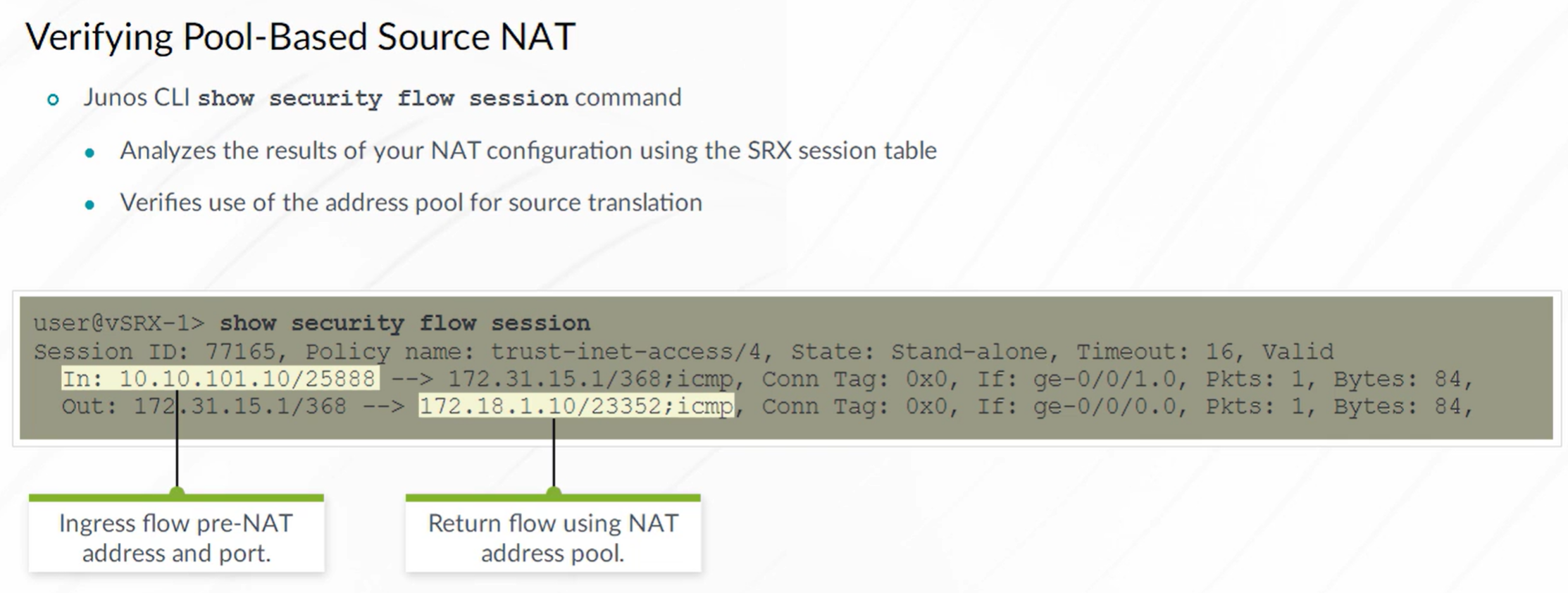
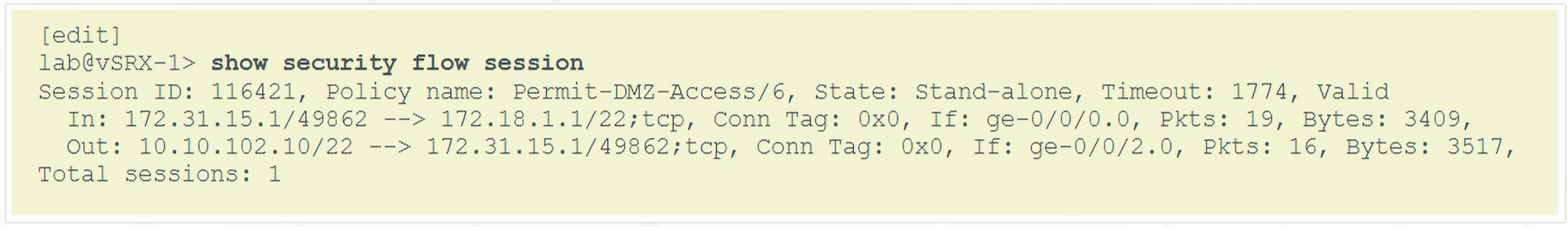
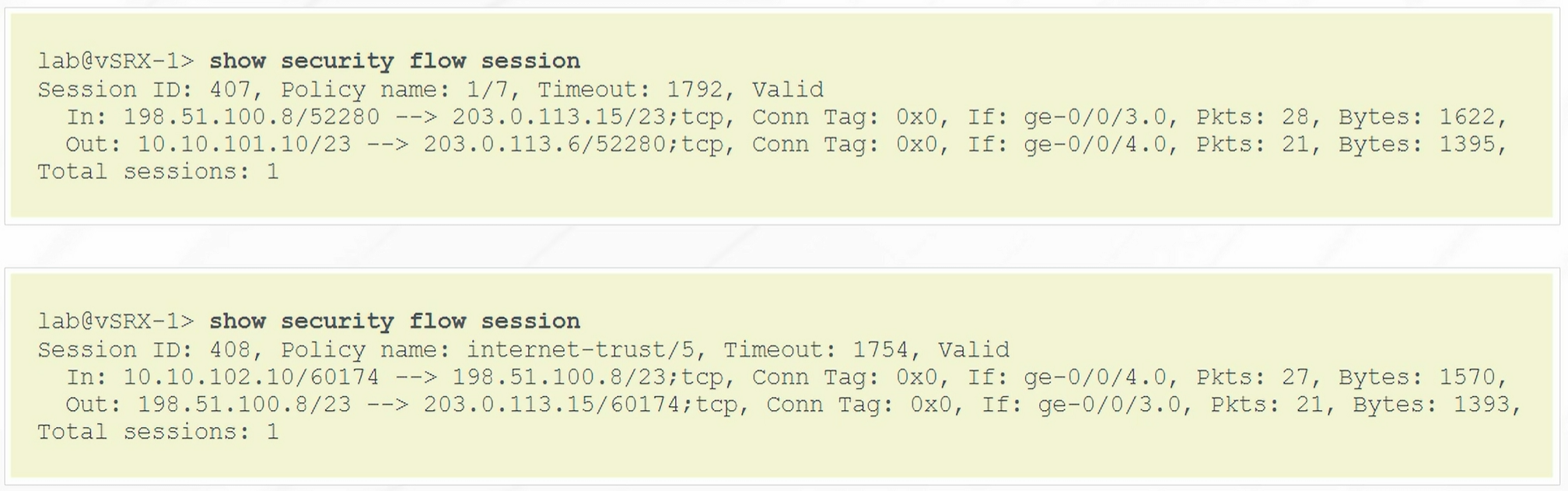
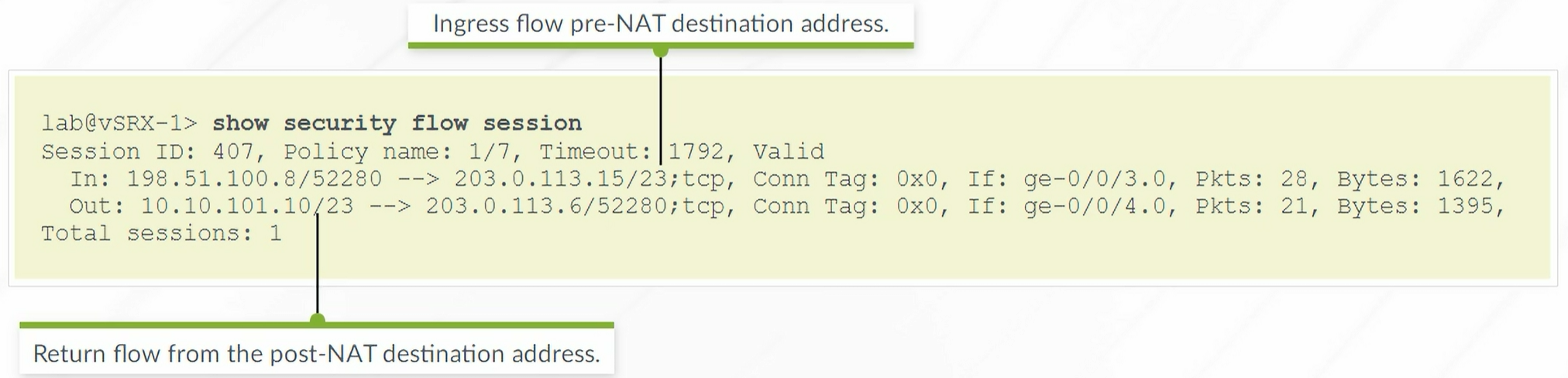
To verify Destination NAT
1
| show security flow session
|
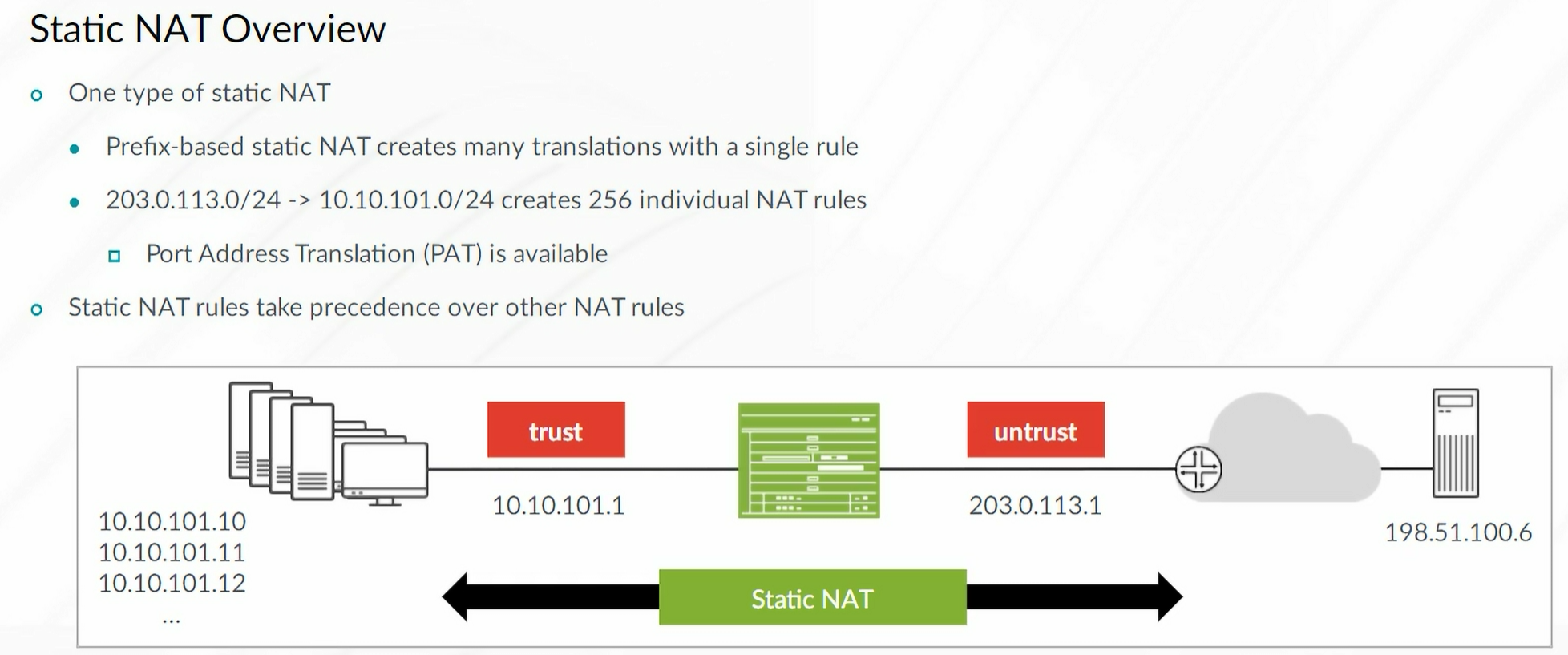
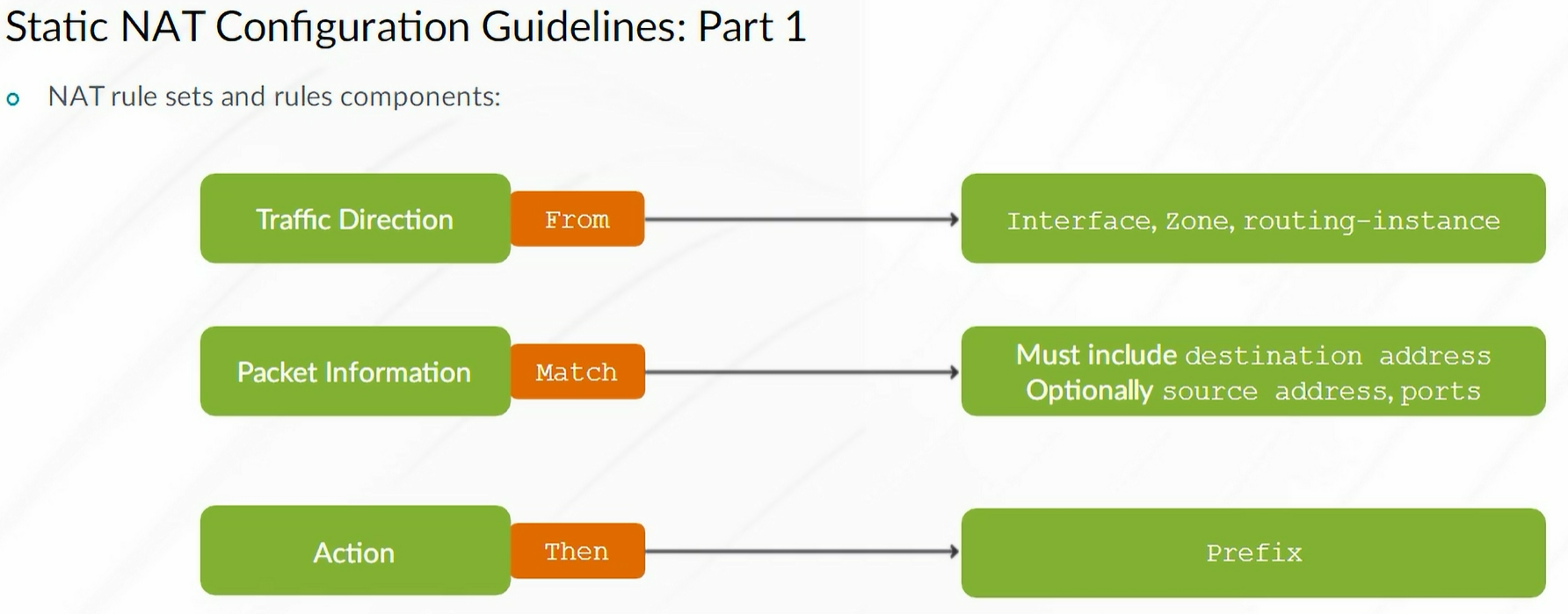
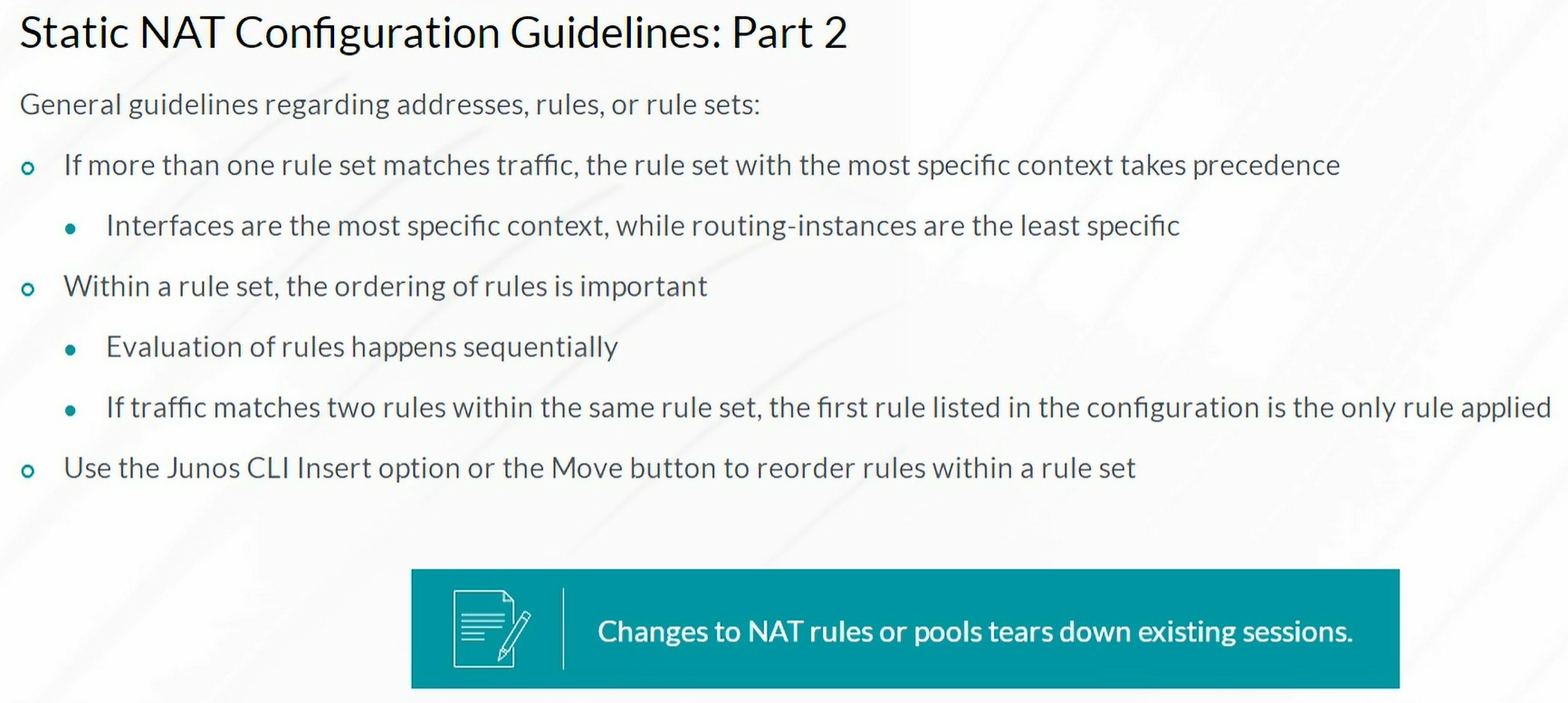
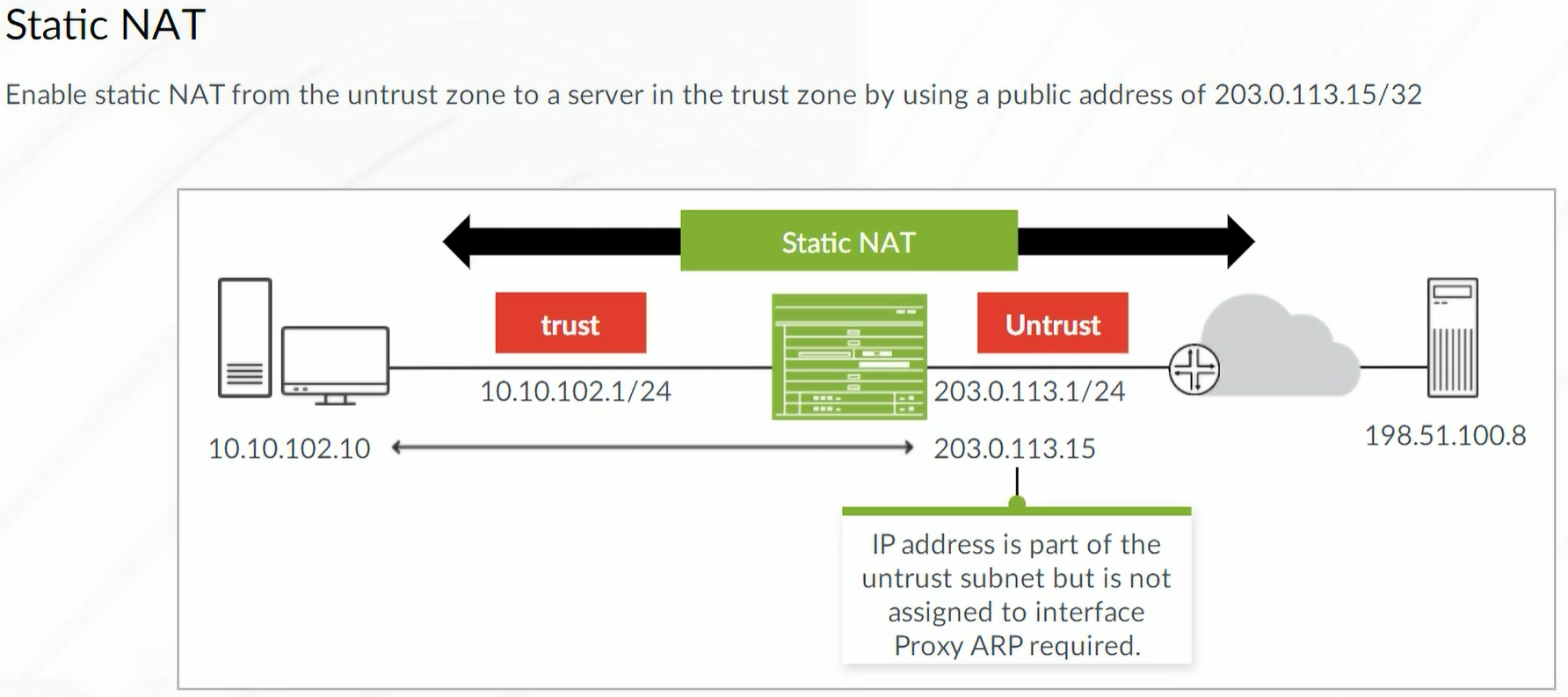
Static NAT
Static NAT mapping includes destination IP address translation in one direction and source IP address translation in the reverse direction. Static NAT is bidirectional.
Note: Static NAT always takes precedence over Source or Destination NAT rules
Static NAT example:
1
2
3
| set security nat static rule-set RULE-SET1 from zone untrust
set security nat static rule-set RULE-SET1 rule R1 match destination-address 203.0.113.15/32
set security nat static rule-set RULE-SET1 rule R1 then static-nat prefix 10.10.102.10/32
|
Proxy ARP must be configured to enable the device to respond to ARP queries for the destination NAT IP Address.
Note: Only required when both the interface IP network and NAT IP are on the same subnet
1
| set security nat proxy-arp interface ge-0/0/0.0 address 203.0.113.15
|
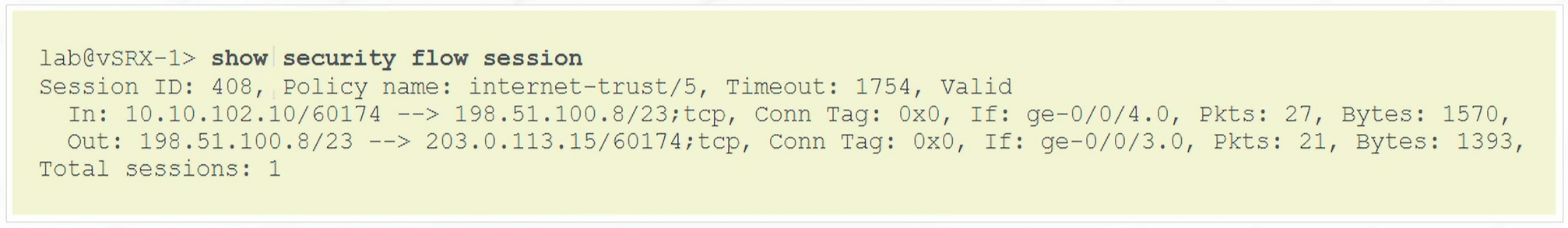
To verify Static NAT
1
| show security flow session
|
Troublehsoot NAT
1
2
3
4
| show security nat source rule all
show security nat destination rule all
show security nat static rule all
show security flow session protocol tcp
|
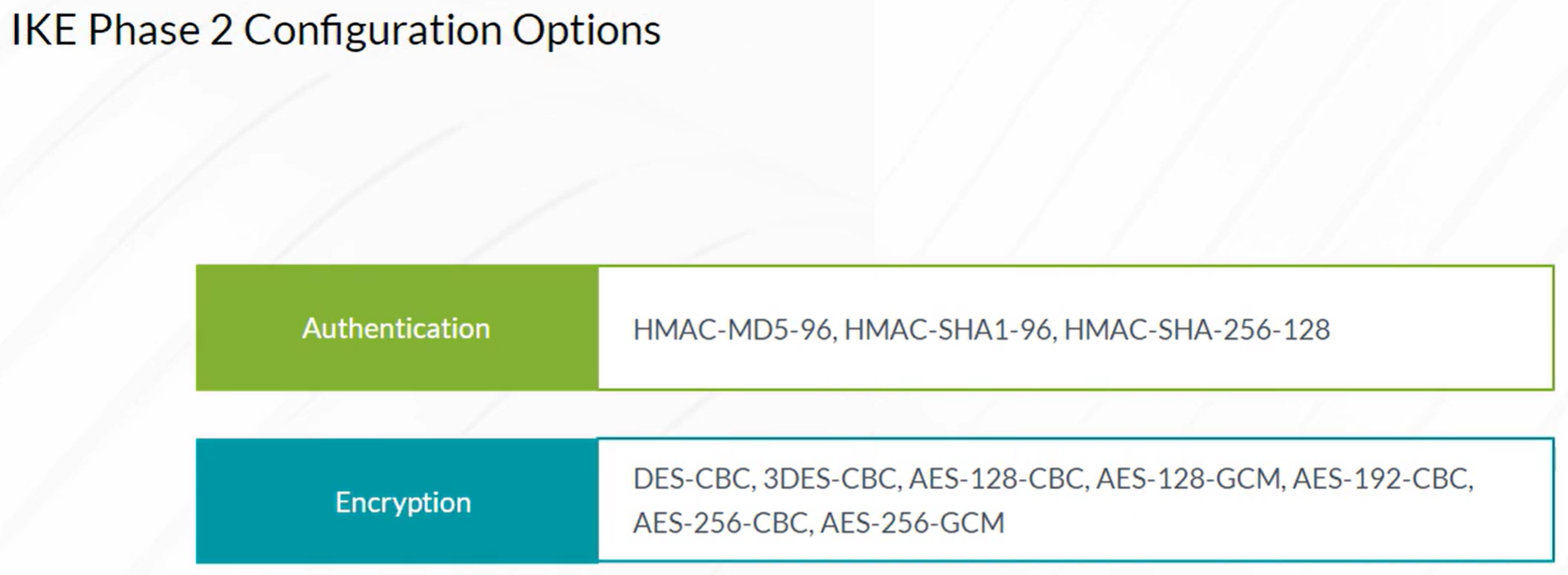
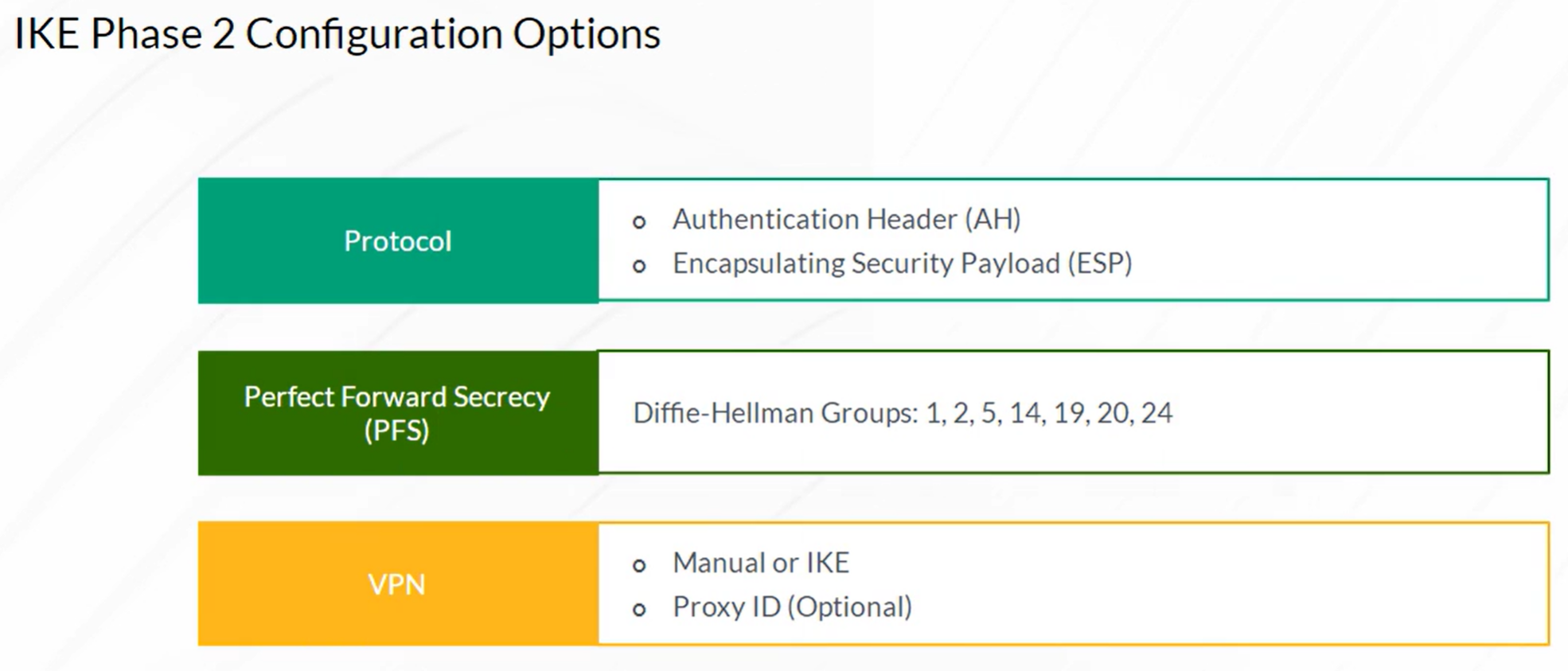
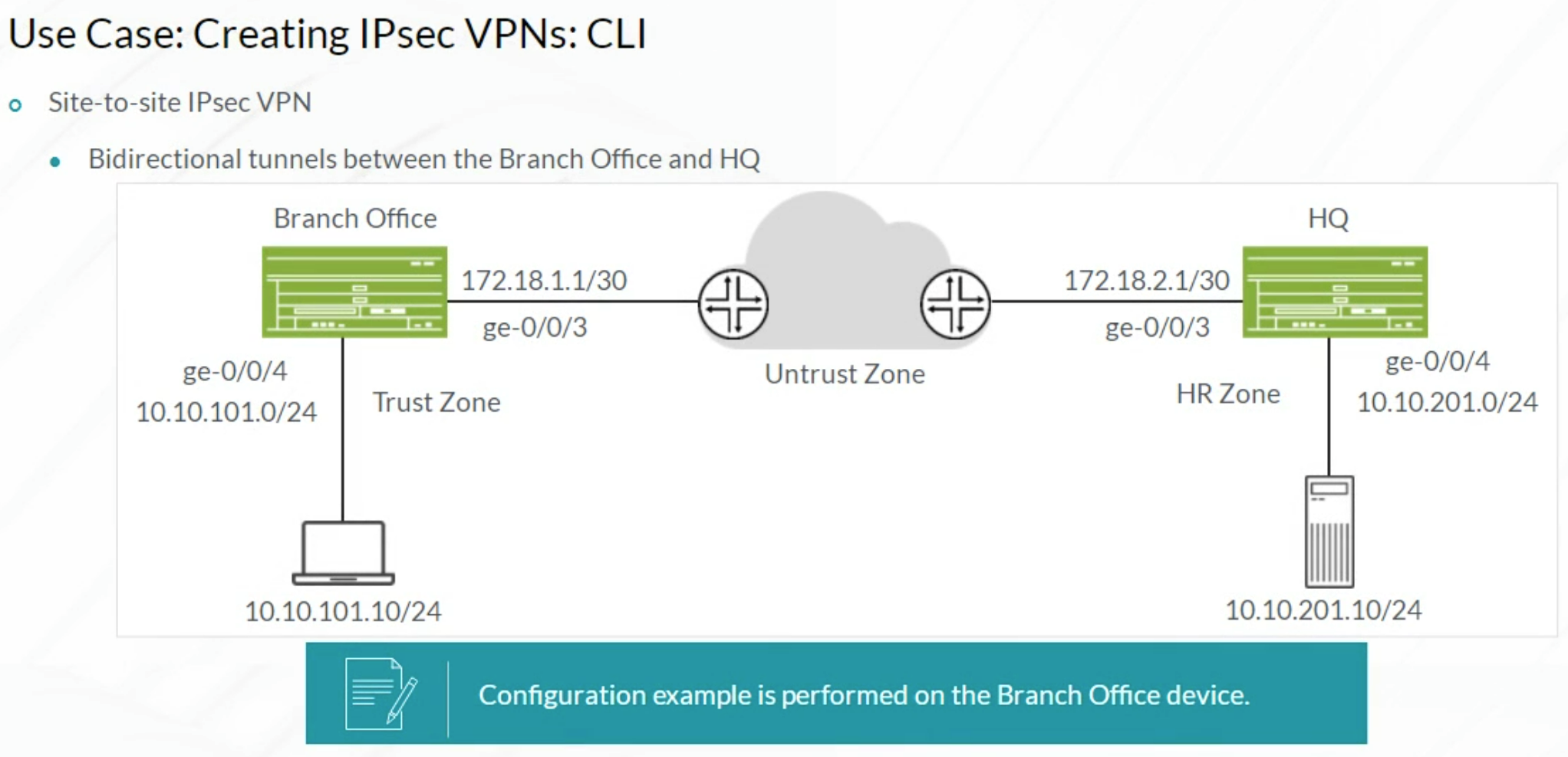
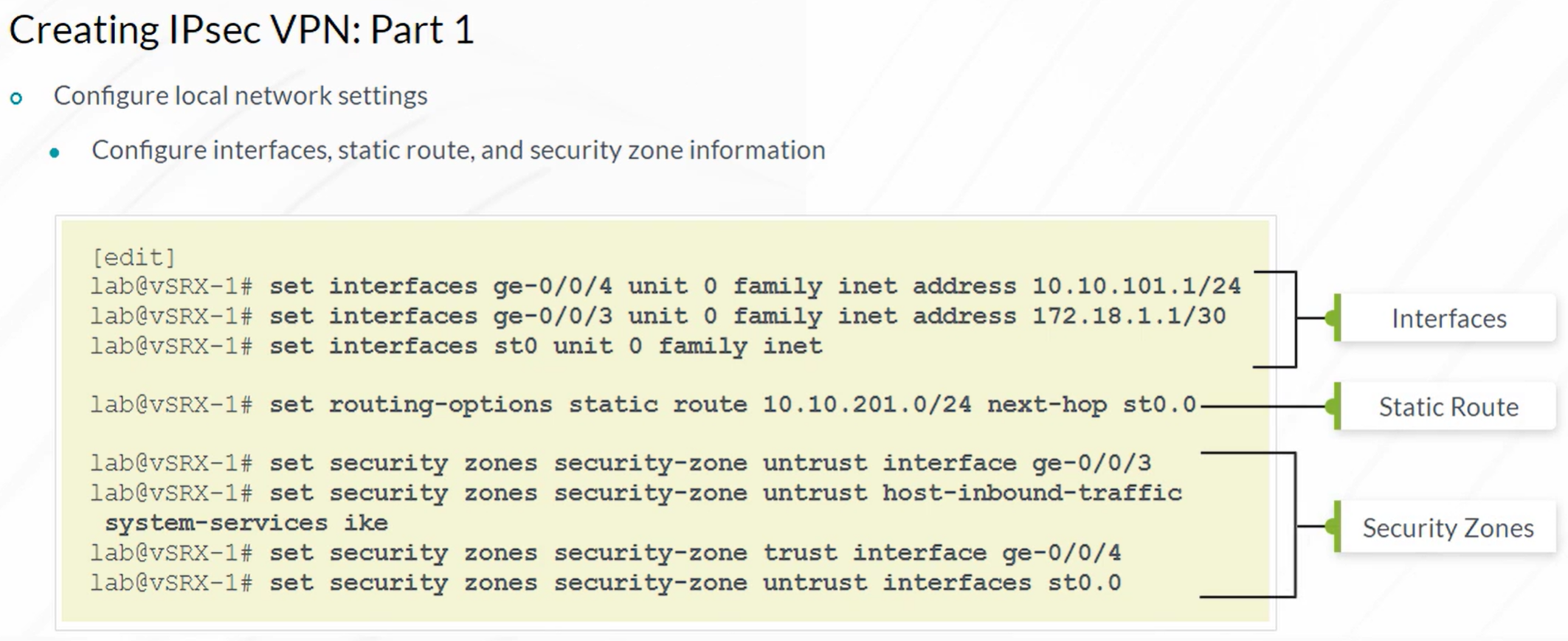
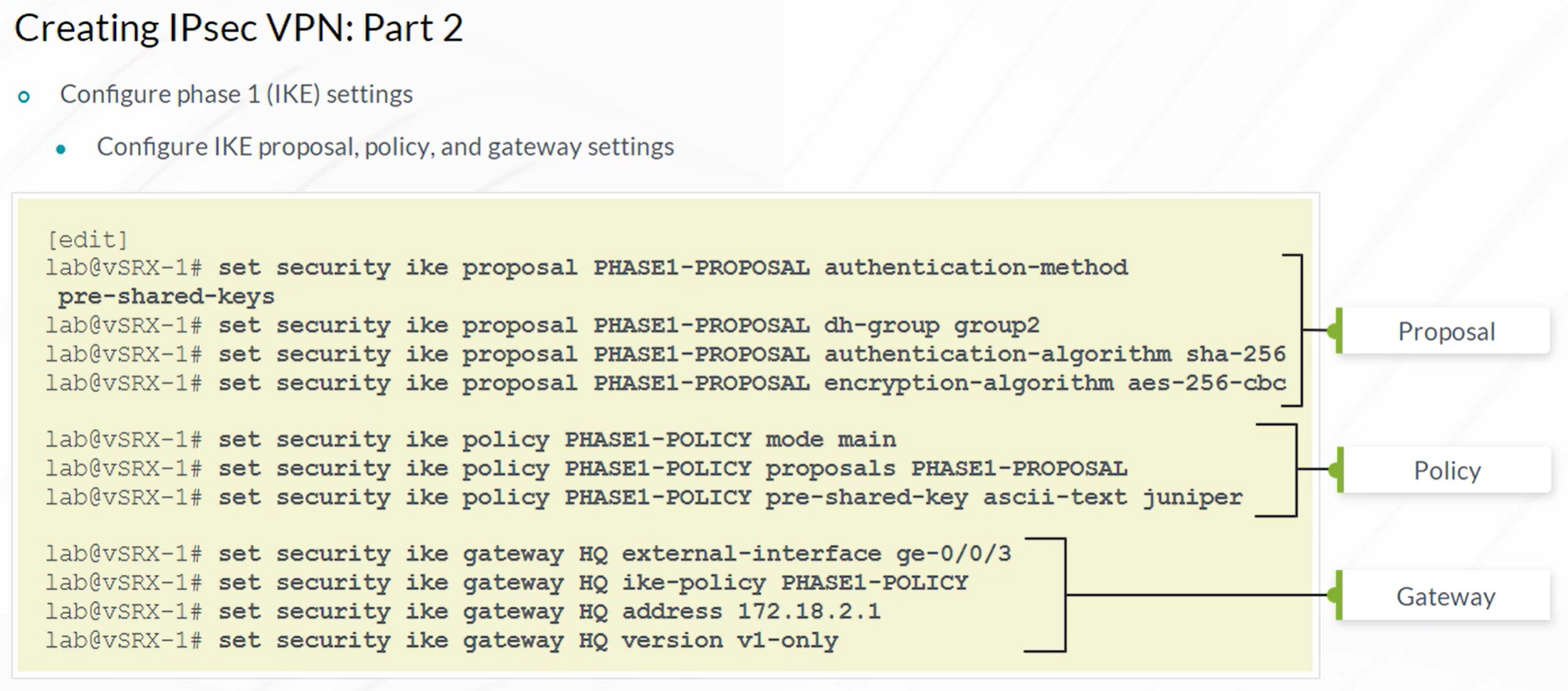
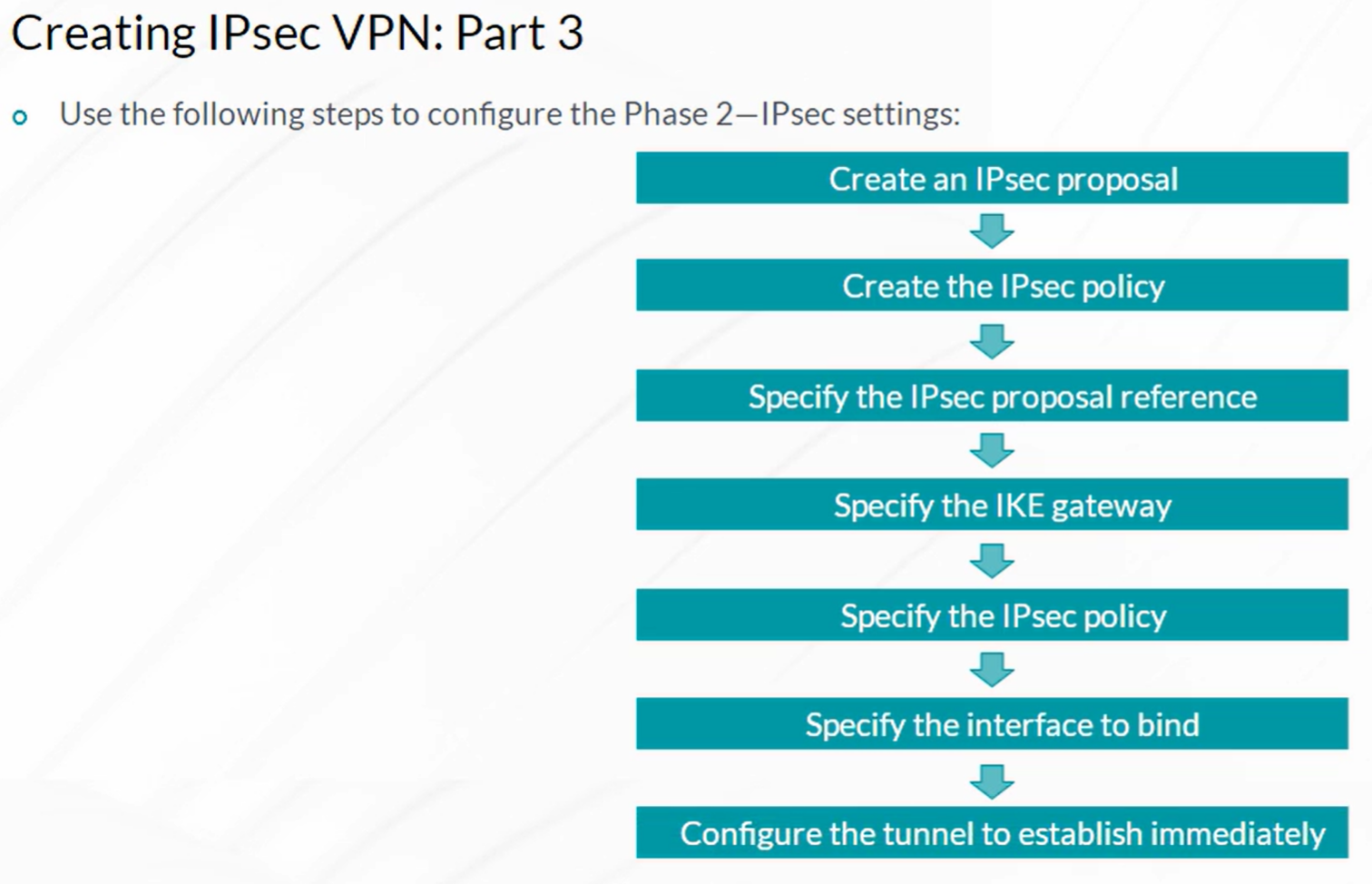
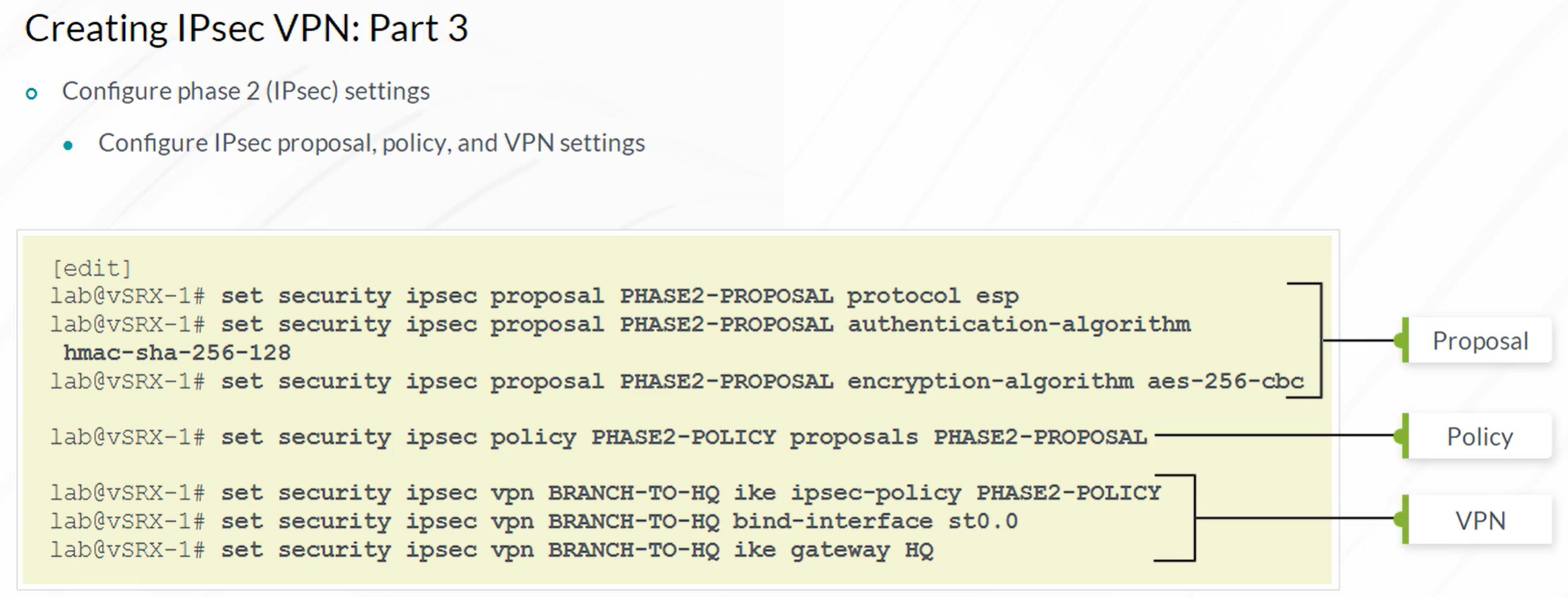
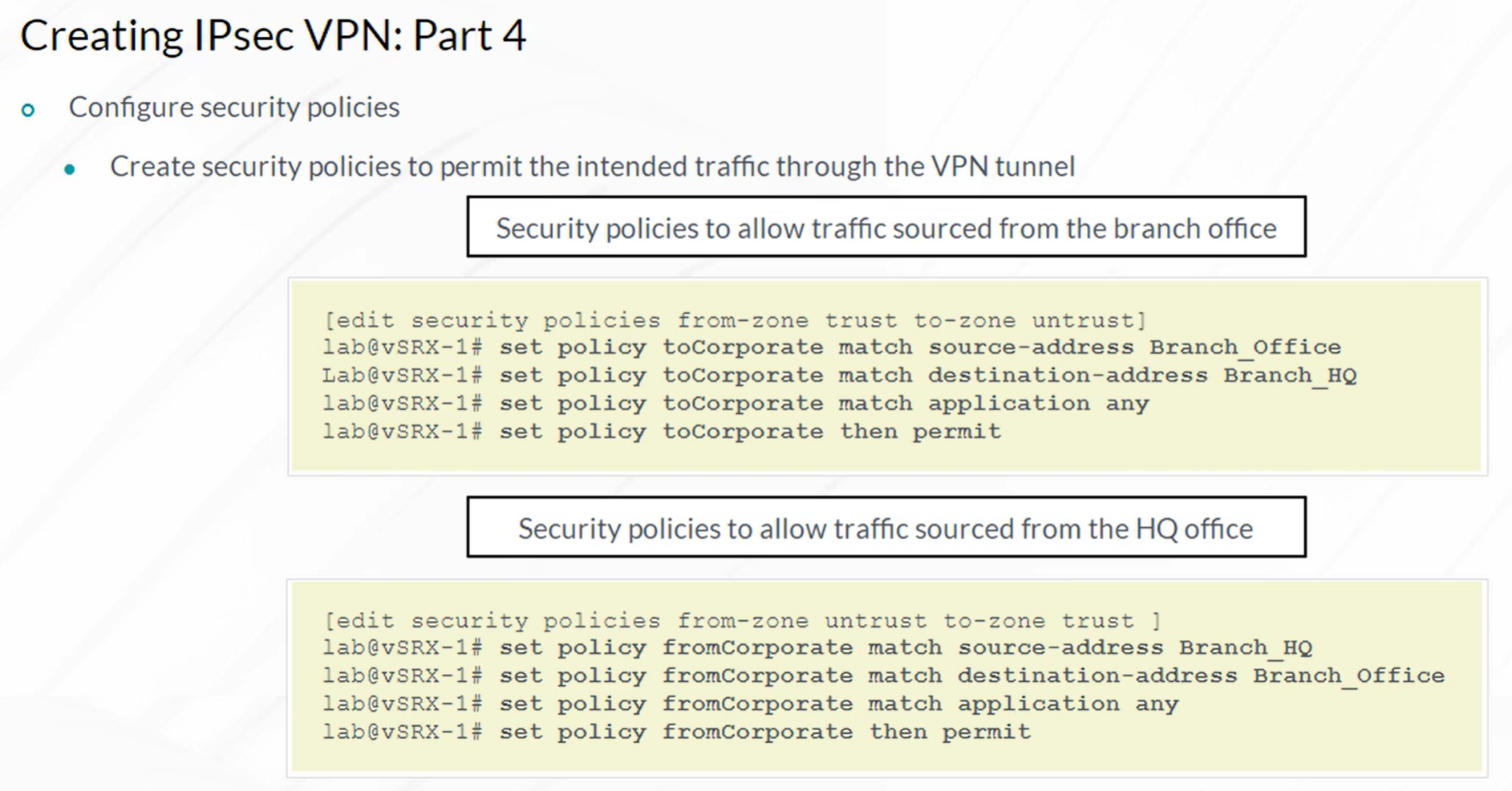
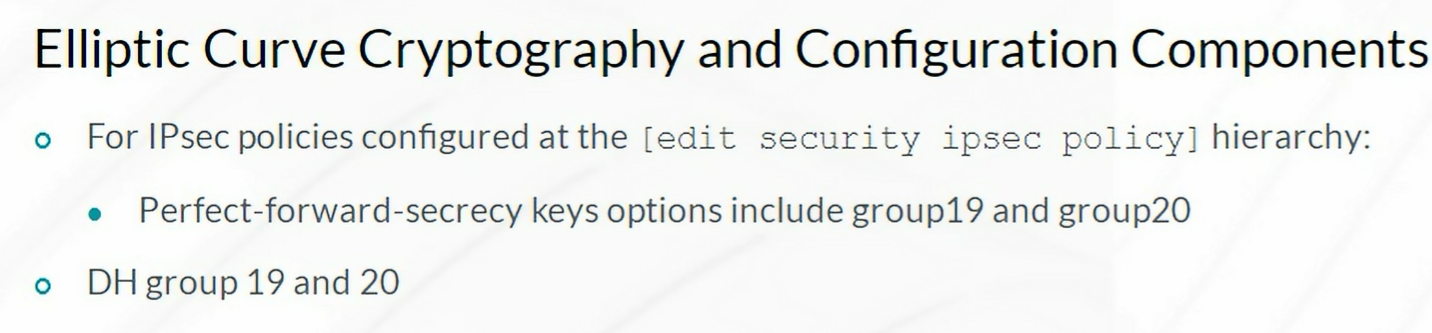
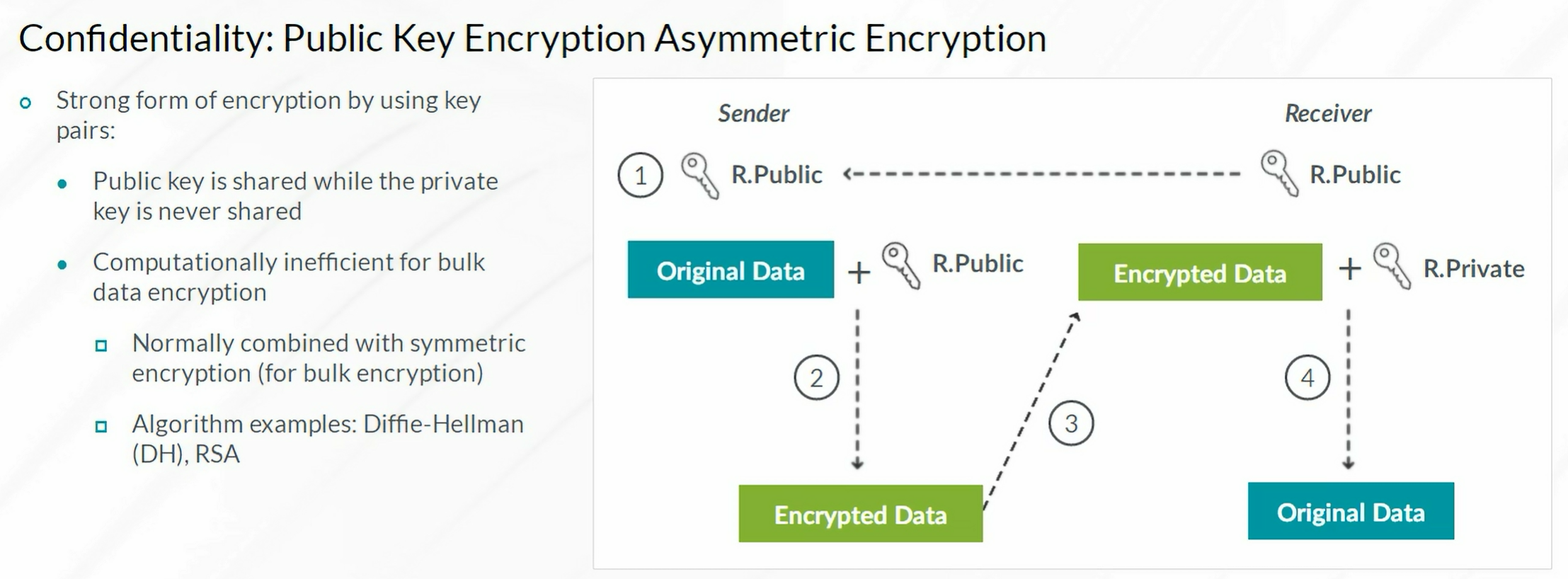
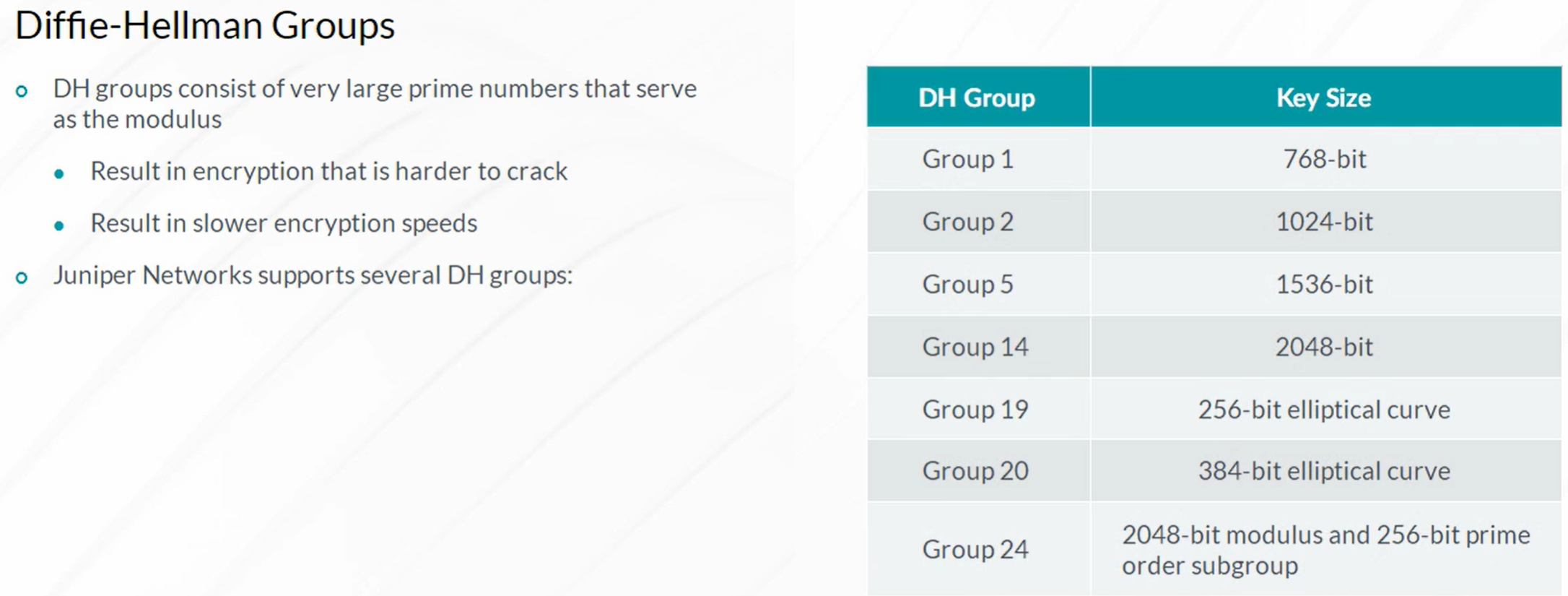
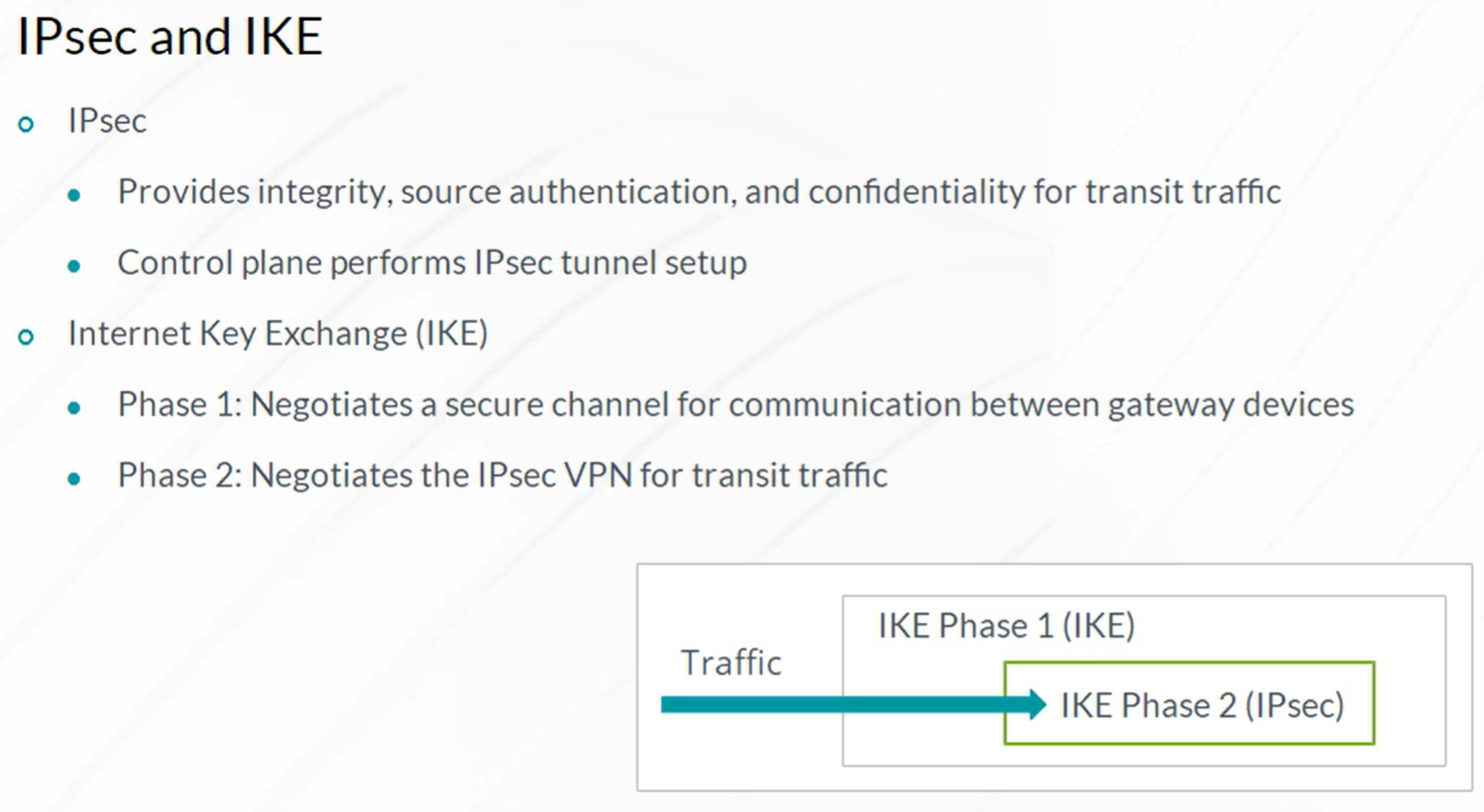
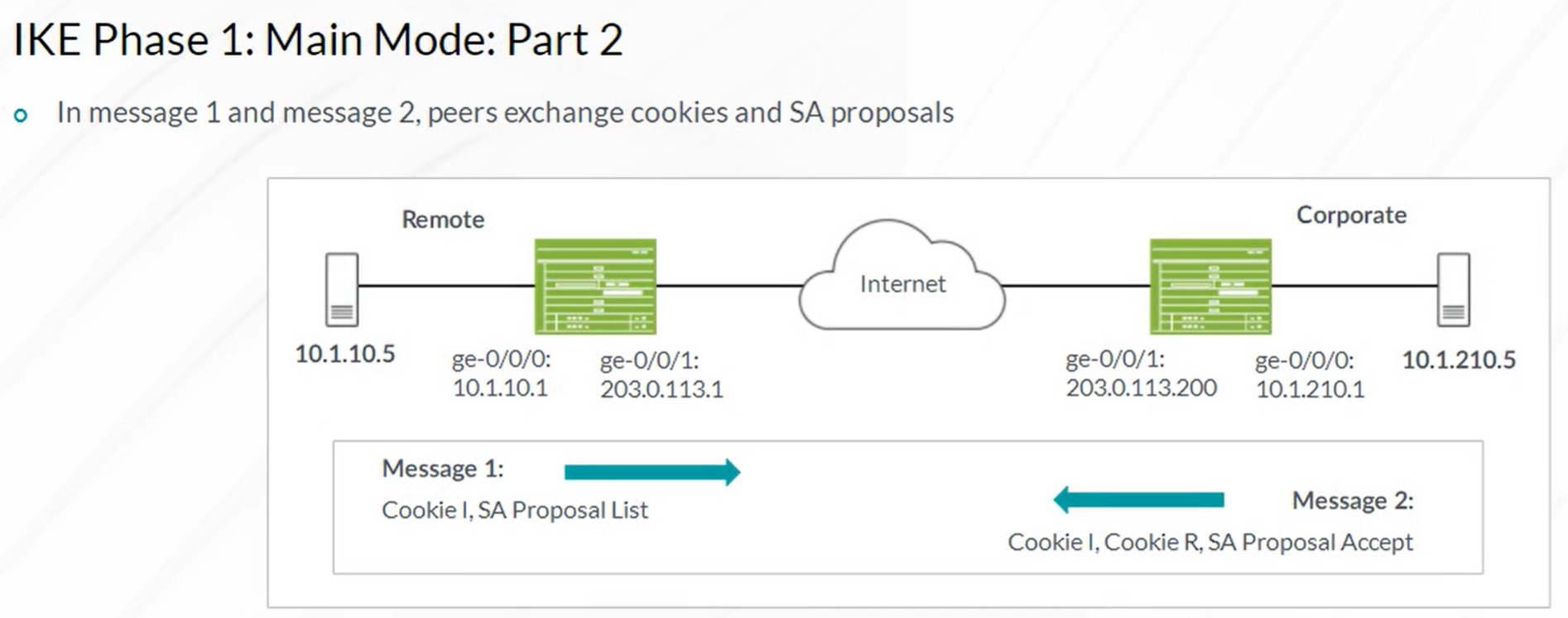
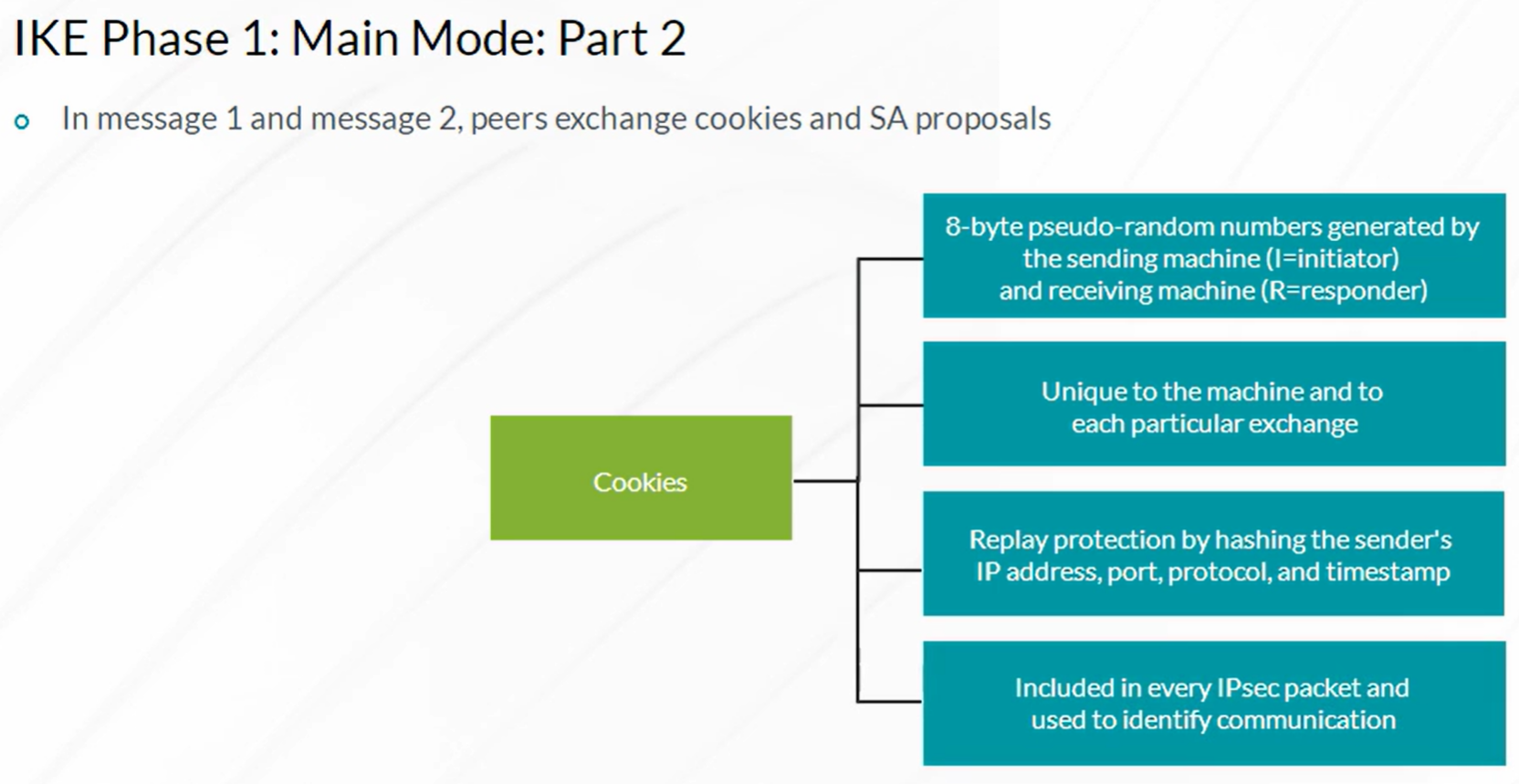
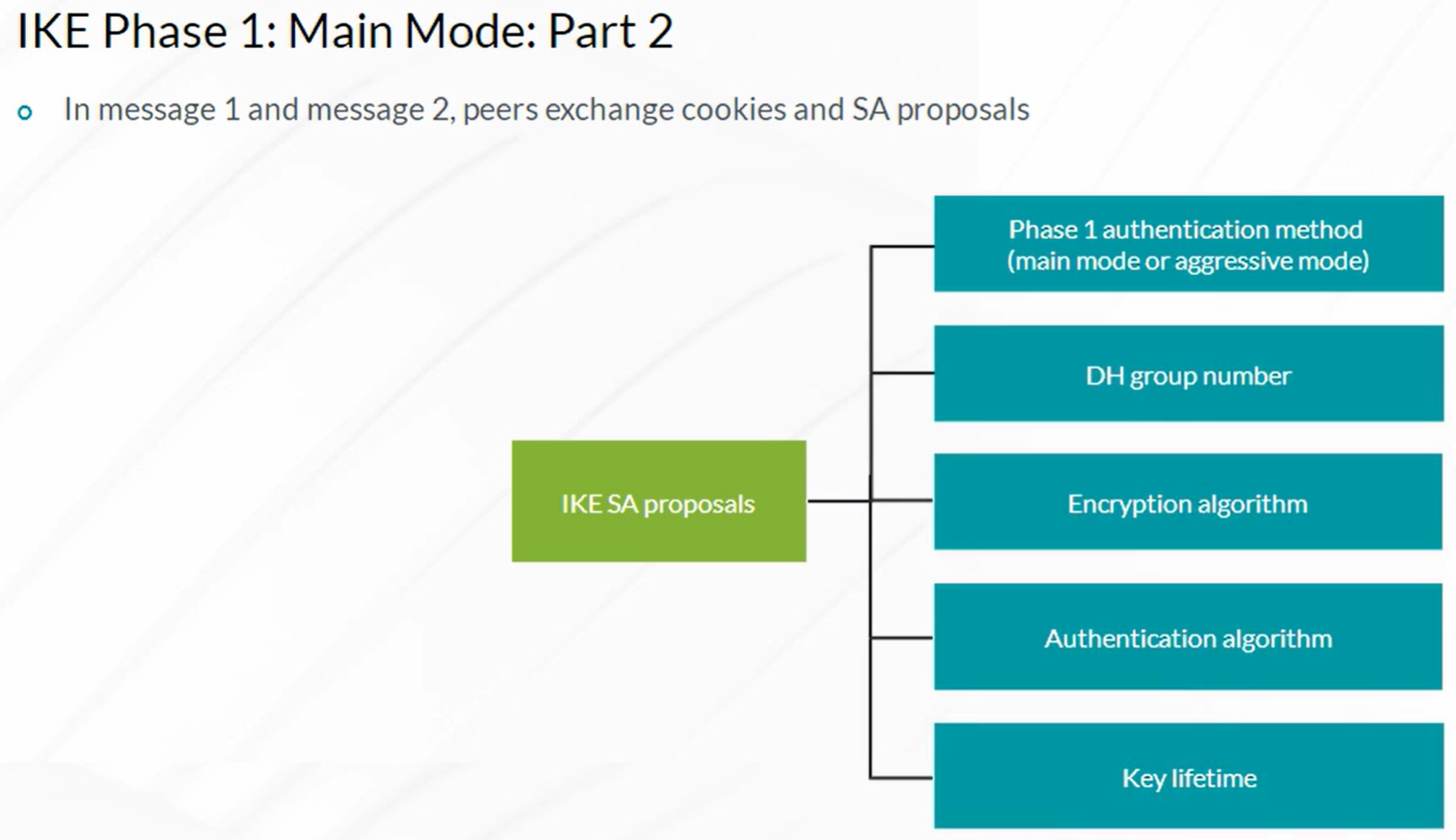
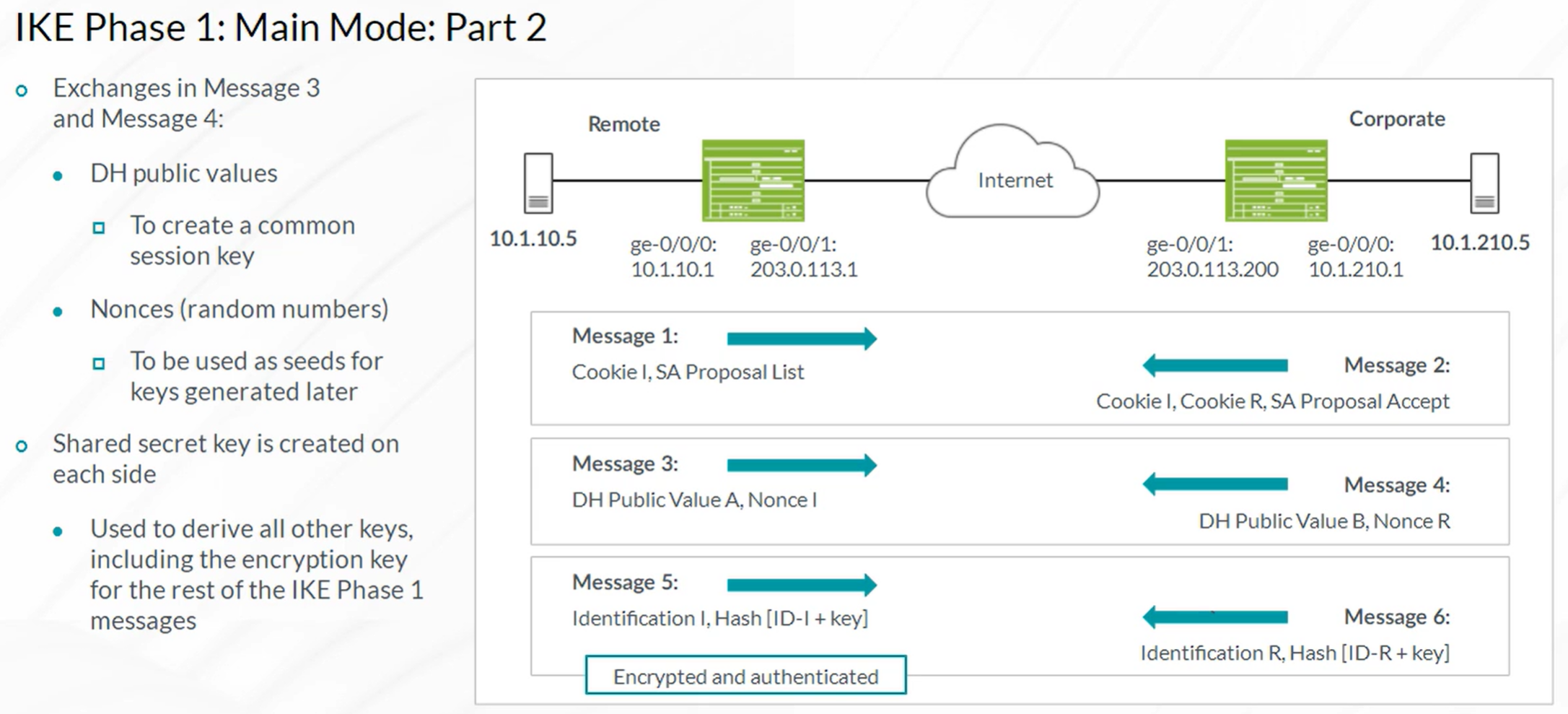
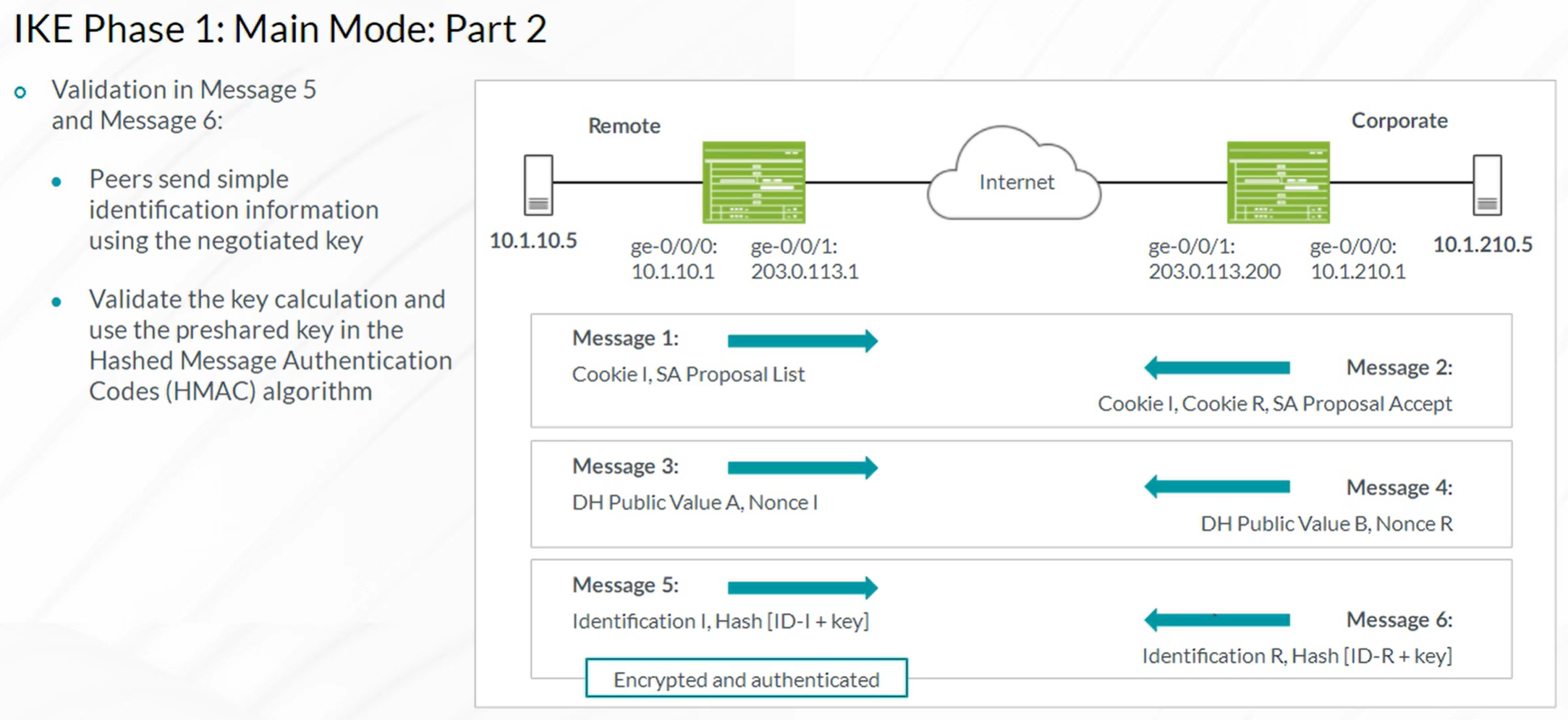
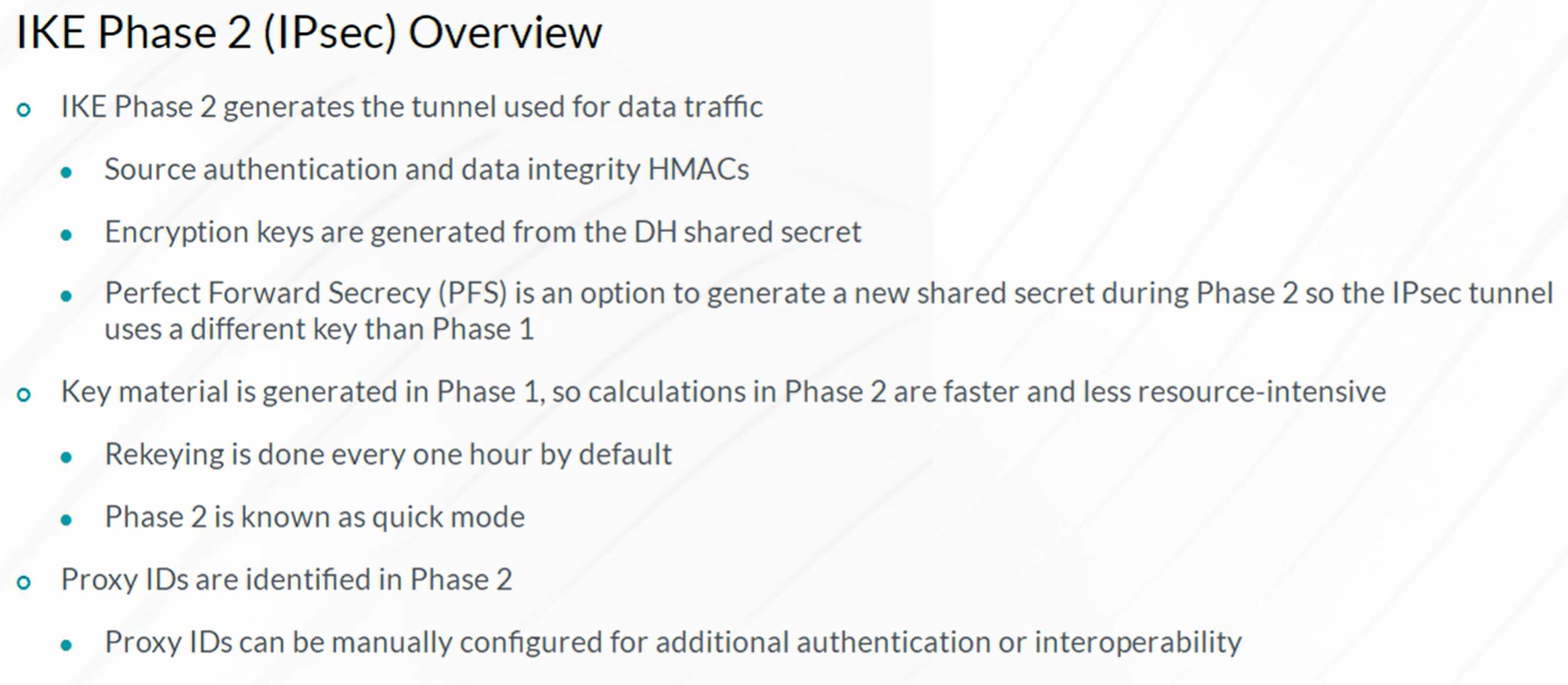
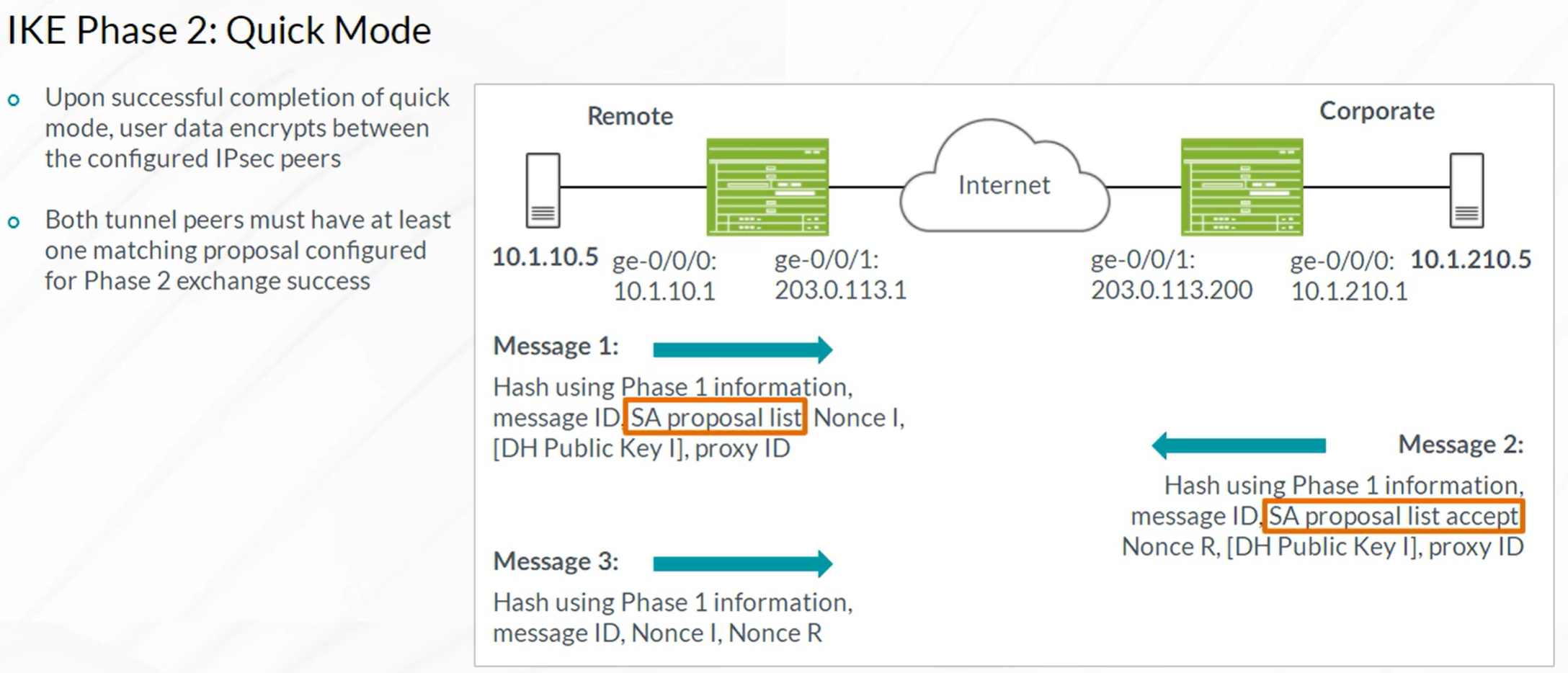
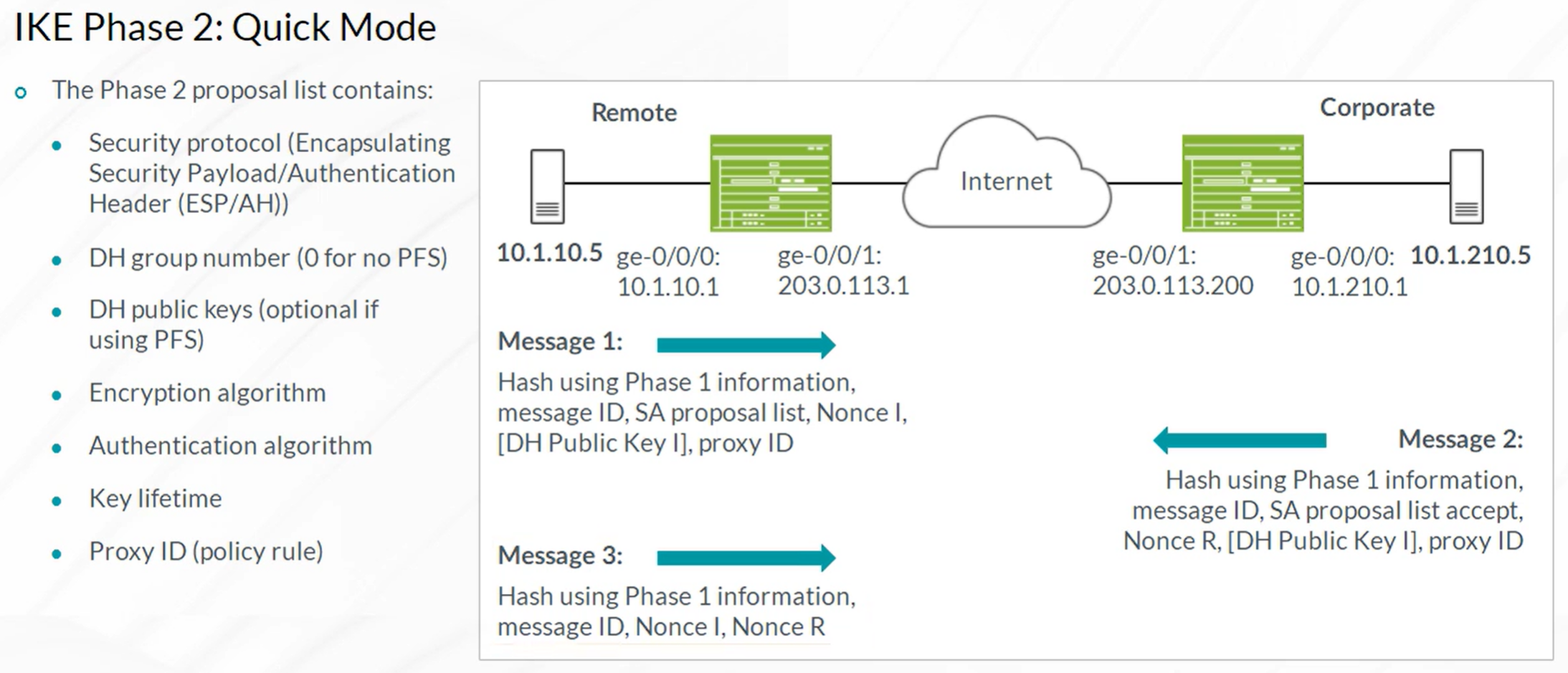
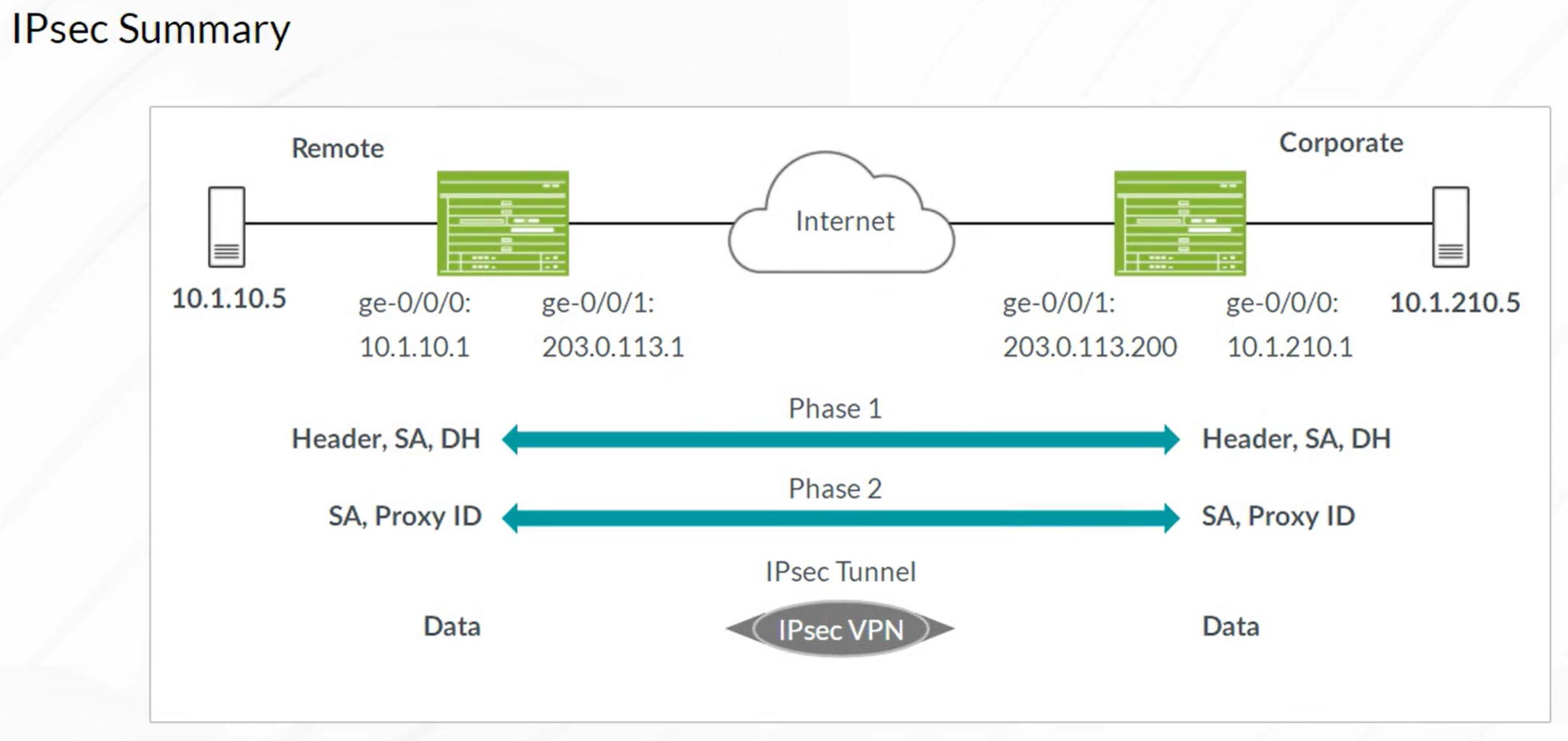
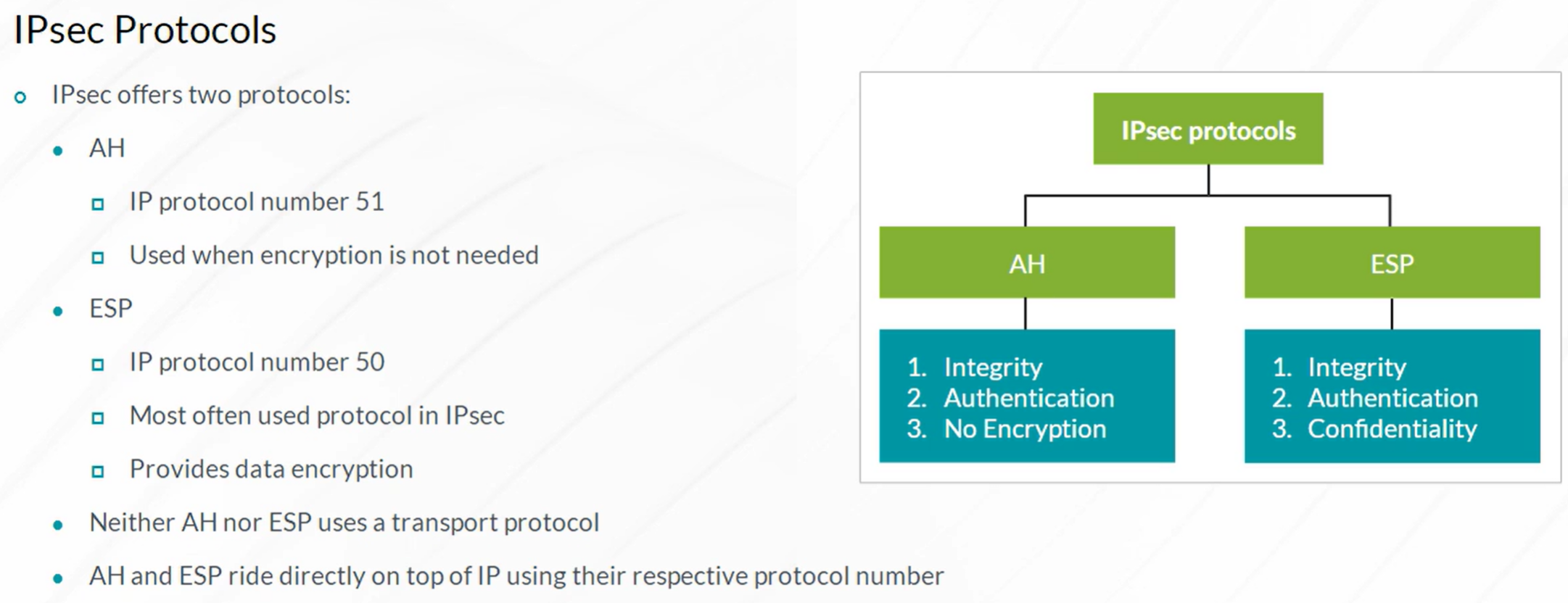
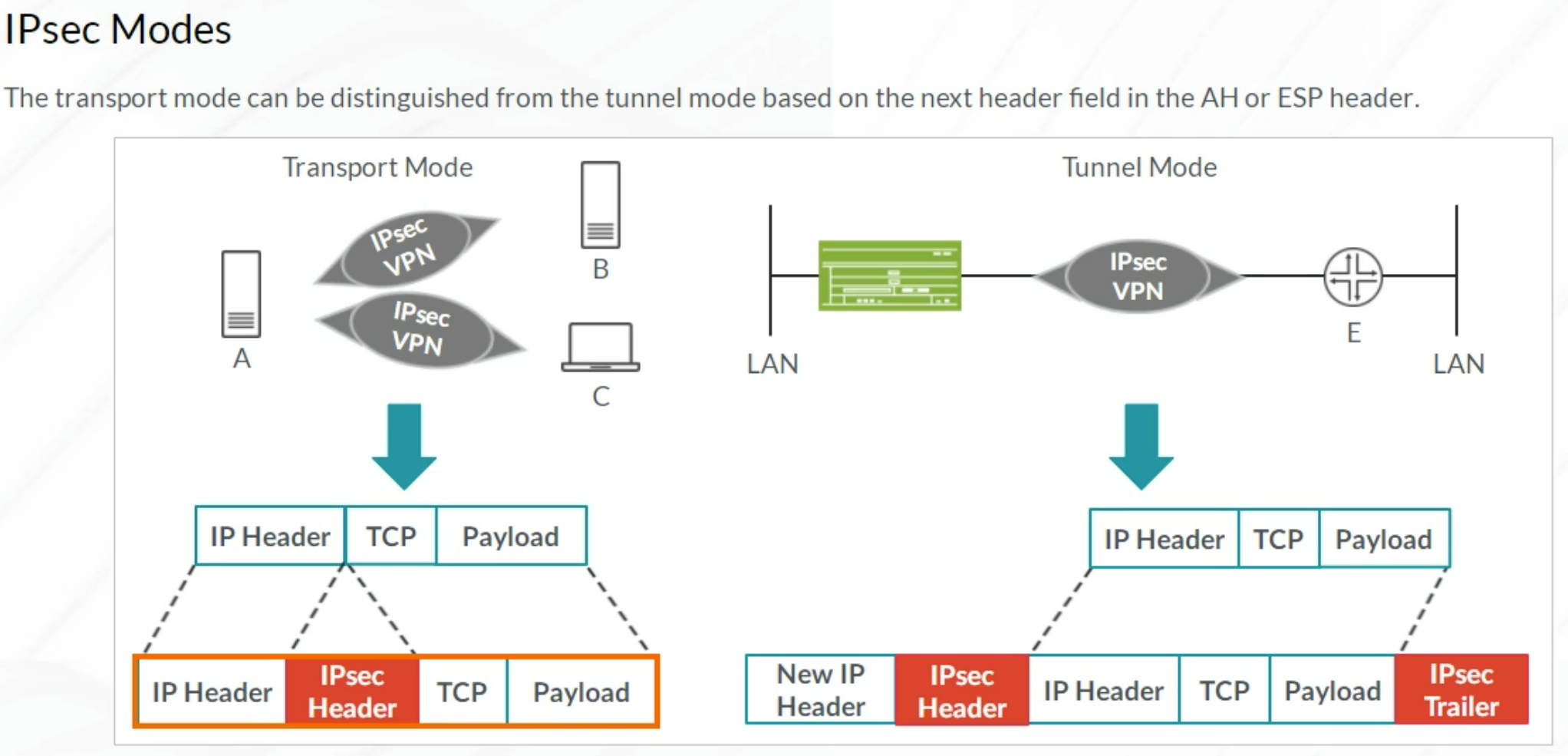
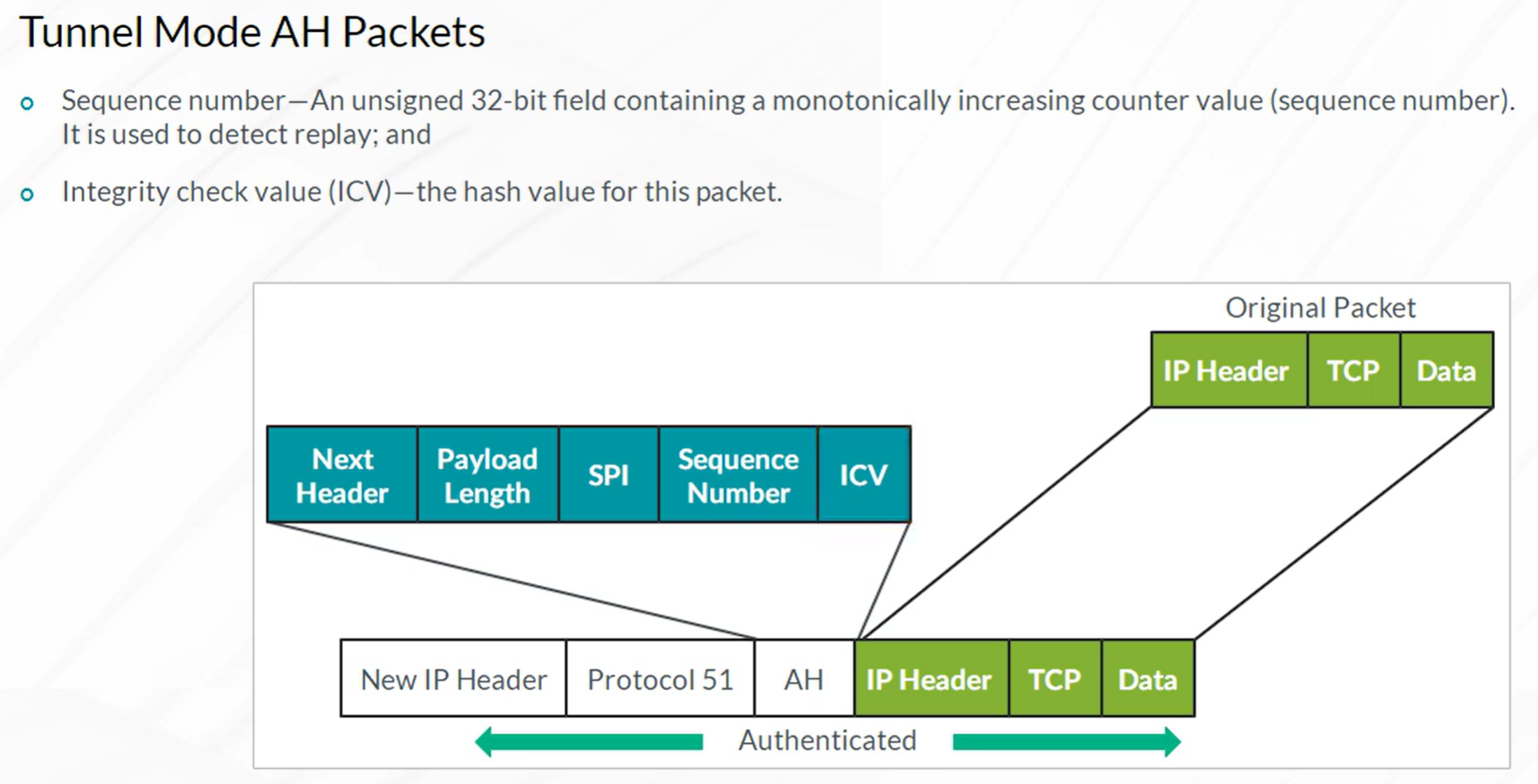
IPsec VPN
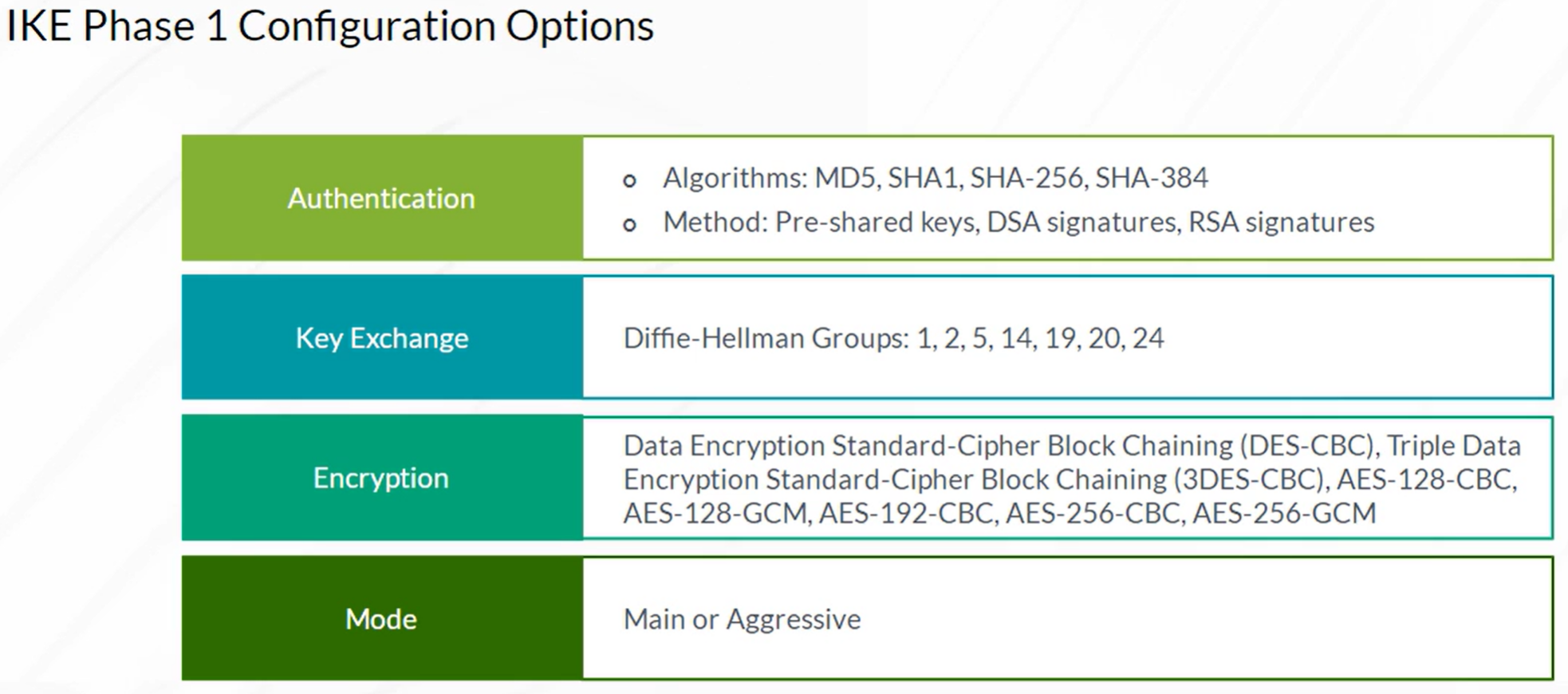
Steps to configure IPSec VPN
- Configuration of Internet Key Exchange (IKE) Phase 1
- Configuration of IKE Phase 2 (IPSec)
- Configuration of the required VPN Routing Parameters
- Configuring the st0 interface and bind to VPN
- Configure routes to remote networks with st0 interface as next hop
IPSec VPN config example
Configuring Proxy ID (optional)
1
| set security ipsec vpn BRANCH-TO-HQ ike proxy-identity local 10.10.101.0/24 remote 10.10.201.0/24
|
Traffic Selector (optional)
1
| set security ipsec vpn BRANCH-TO-HQ traffic-selector local-ip 10.10.101.0/24 remote-ip 10.10.201.0/24
|
DPD (Dead Peer Detection) (optional)
1
| set security ike gateway HQ dead-peer-detection interval 10 threshold 5
|
VPN Monitoring (optional) - Juniper proprietary method to monitor the VPN’s health
1
| set security ipsec vpn BRANCH-TO-HQ vpn-monitor destination-ip 10.10.201.10 optimized source-interface st0.0
|
Troubleshooting IPSec VPN
Tunnel setup
1
2
| show security ike security-associations
show security ipsec security-associations
|
Data Plane traffic statistics
1
| show security ipsec statistics
|
Verify the st interface
1
2
| show security st0 extensive
show security ipsec traffic-selector interface-name st0.0 detail
|
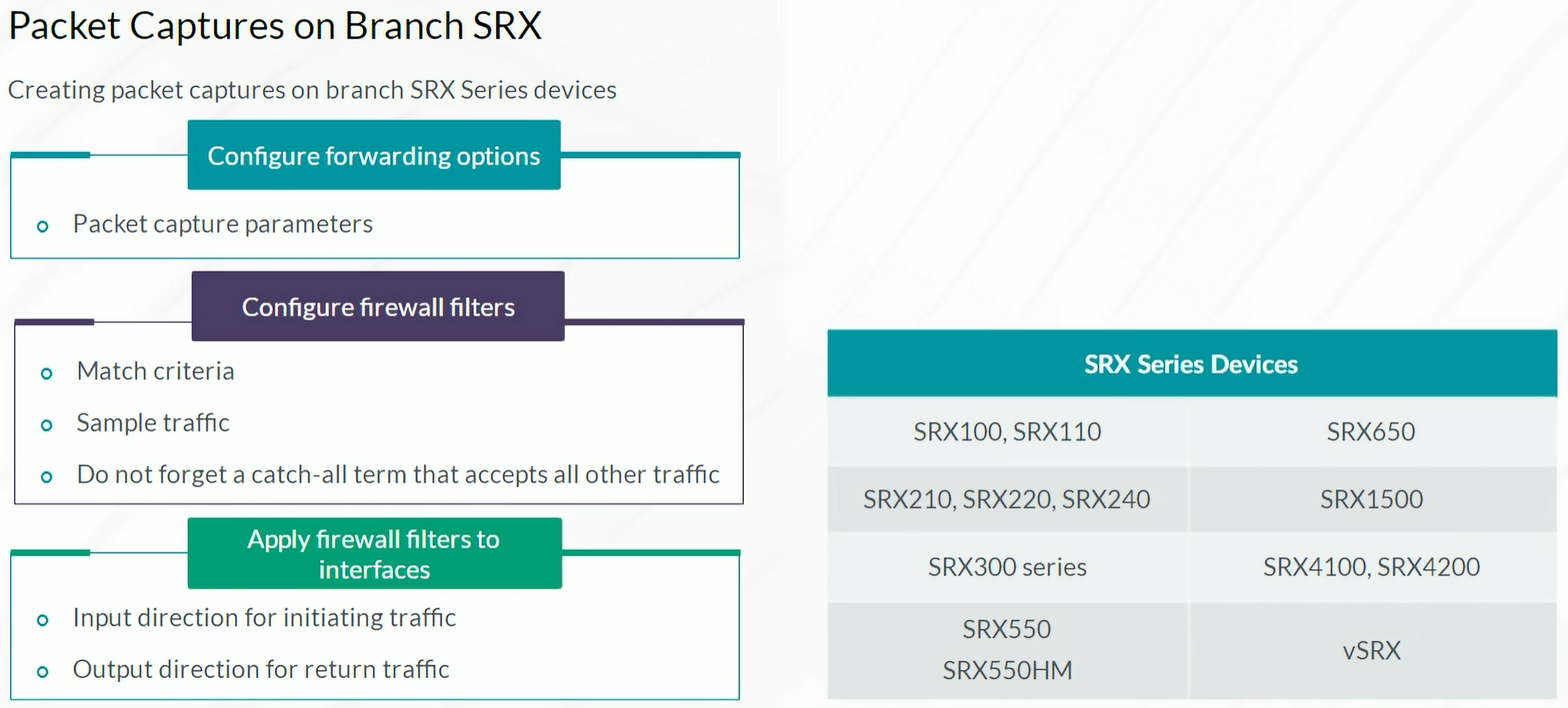
Packet Captures
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| set forwarding-options packet-capture file filename PACKET-CAPTURE
set forwarding-options packet-capture maximum-capture-size 1500 (optional)
set firewall family inet filter PACKET-CAP term INIT from source-address 172.25.99.1/32
set firewall family inet filter PACKET-CAP term INIT from destination-address 198.51.100.8/32
set firewall family inet filter PACKET-CAP term INIT then sample (important)
set firewall family inet filter PACKET-CAP term INIT then accept
set firewall family inet filter PACKET-CAP term RETURN from source-address 198.51.100.8/32
set firewall family inet filter PACKET-CAP term RETURN from destination-address 172.25.99.1/32
set firewall family inet filter PACKET-CAP term RETURN then sample (important)
set firewall family inet filter PACKET-CAP term RETURN then accept
set firewall family inet filter PACKET-CAP term ALLOW-ALL then accept
set interfaces ge-0/0/0 unit 0 family inet filter input PACKET-CAP
set interfaces ge-0/0/0 unit 0 family inet filter output PACKET-CAP
set interfaces ge-0/0/0 unit 0 family inet address 172.25.99.254/24
|
The capture is stored in /var/tmp/
1
| file list /var/tmp/ | match PACKET-CAPTURE
|
Packet Captures on High-End SRX
Configure datapath debugging. Drop to the shell to remove unnecessary fields.
Warning: The datapath-debug should not be used in IPv6 environments when using hash-based session distribution
Important: Works only on: SRX1400 SRX3400, SRX3600 SRX5400, SRX5600, SRX5800
1
2
3
4
5
6
7
8
9
| set security datapath-debug capture-file MY-CAPTURE format pcap size 1m files 5
set security datapath-debug maximum-capture-size 1500
set security datapath-debug action-profile perform-capture event np-egress packet-dump
set security datapath-debug action-profile perform-capture event np-ingress packet-dump
set security datapath-debug packet-filter cap-filter action-profile perform-capture
set security datapath-debug packet-filter cap-filter source-prefix 172.25.99.1/32
set security datapath-debug packet-filter cap-filter destination-prefix 198.51.100.8/32
|
Start the packet capture and stop it when finished
1
| request security datapath-debug capture [start | stop]
|
View the packet capture locally
1
| show security datapath-debug capture
|
View the packet capture offline. We need to remove some fields:
1
2
3
4
5
| start shell
su
cd /var/log
e2einfo -Ccapture -Snormalize -I MY-CAPTURE -F MY-CAPTURE.pcap
|
Collecting Control Plane traffic
1
2
3
4
5
6
| start shell
su root
tcpdump -i ge-0/0/0 -s 1500 -w /var/tmp/TO-HOST.pcap -c 5000
ls /var/tmp/ | grep TO-HOST.pcap
|
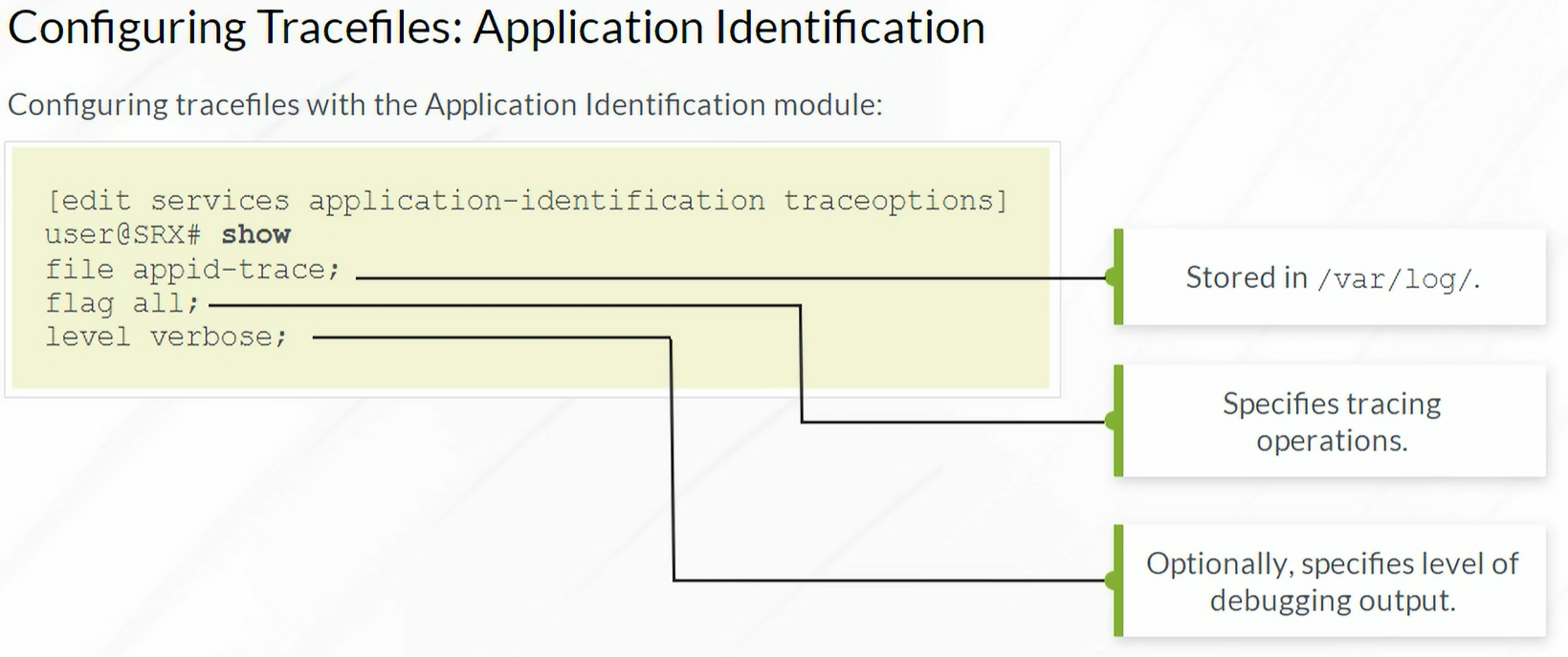
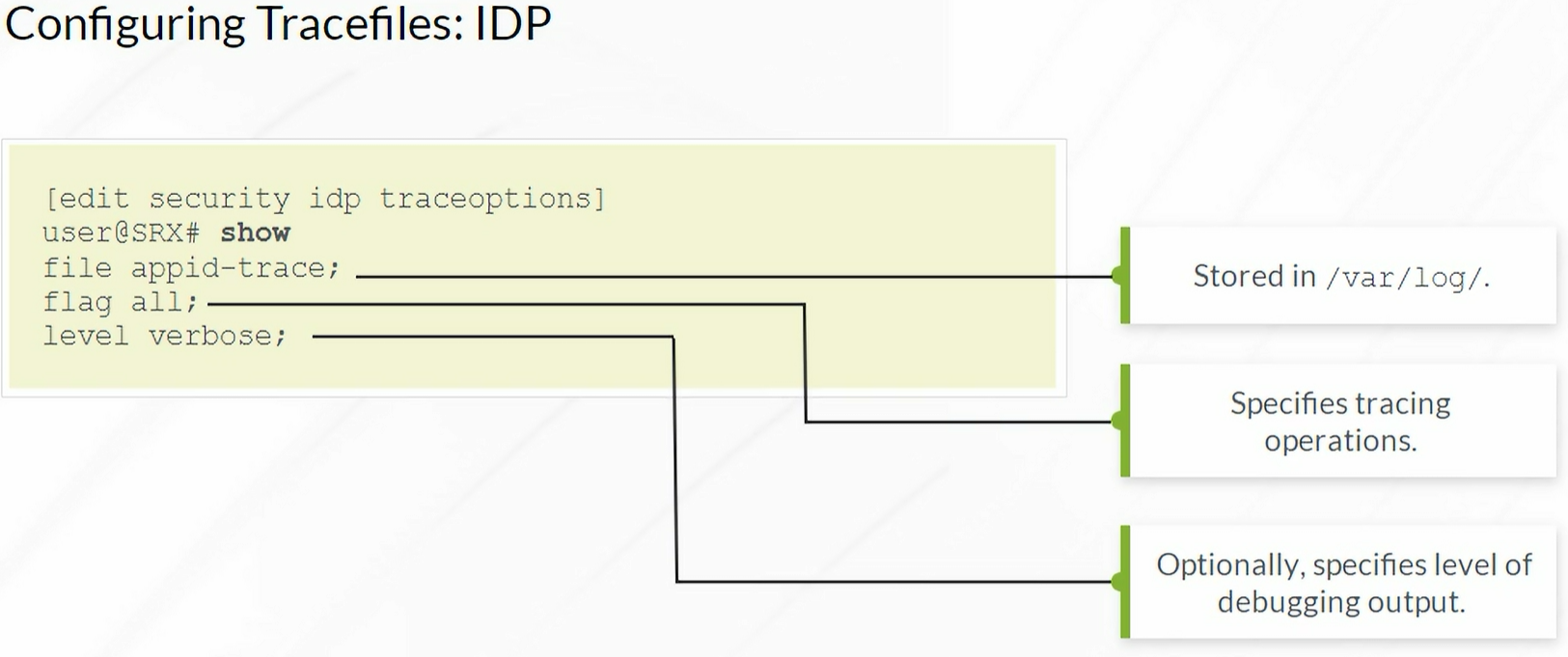
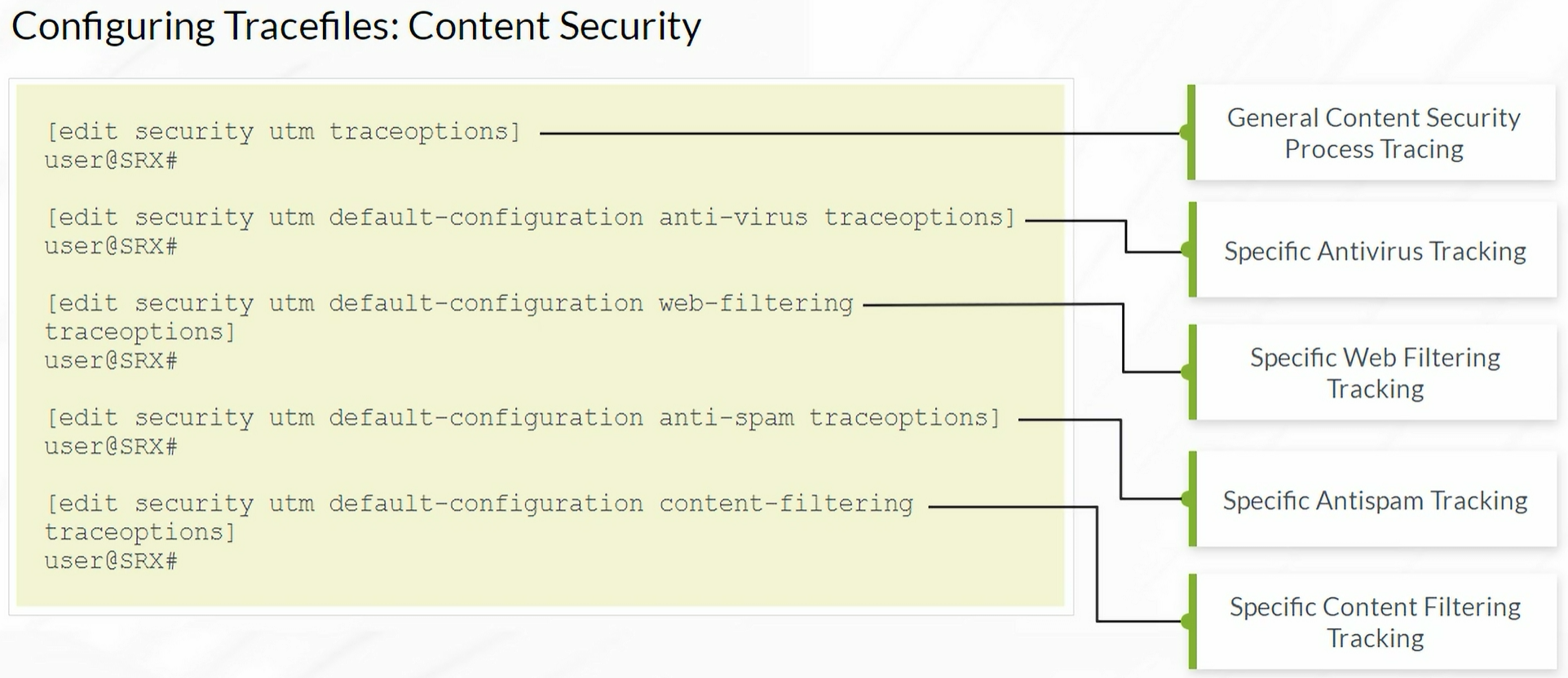
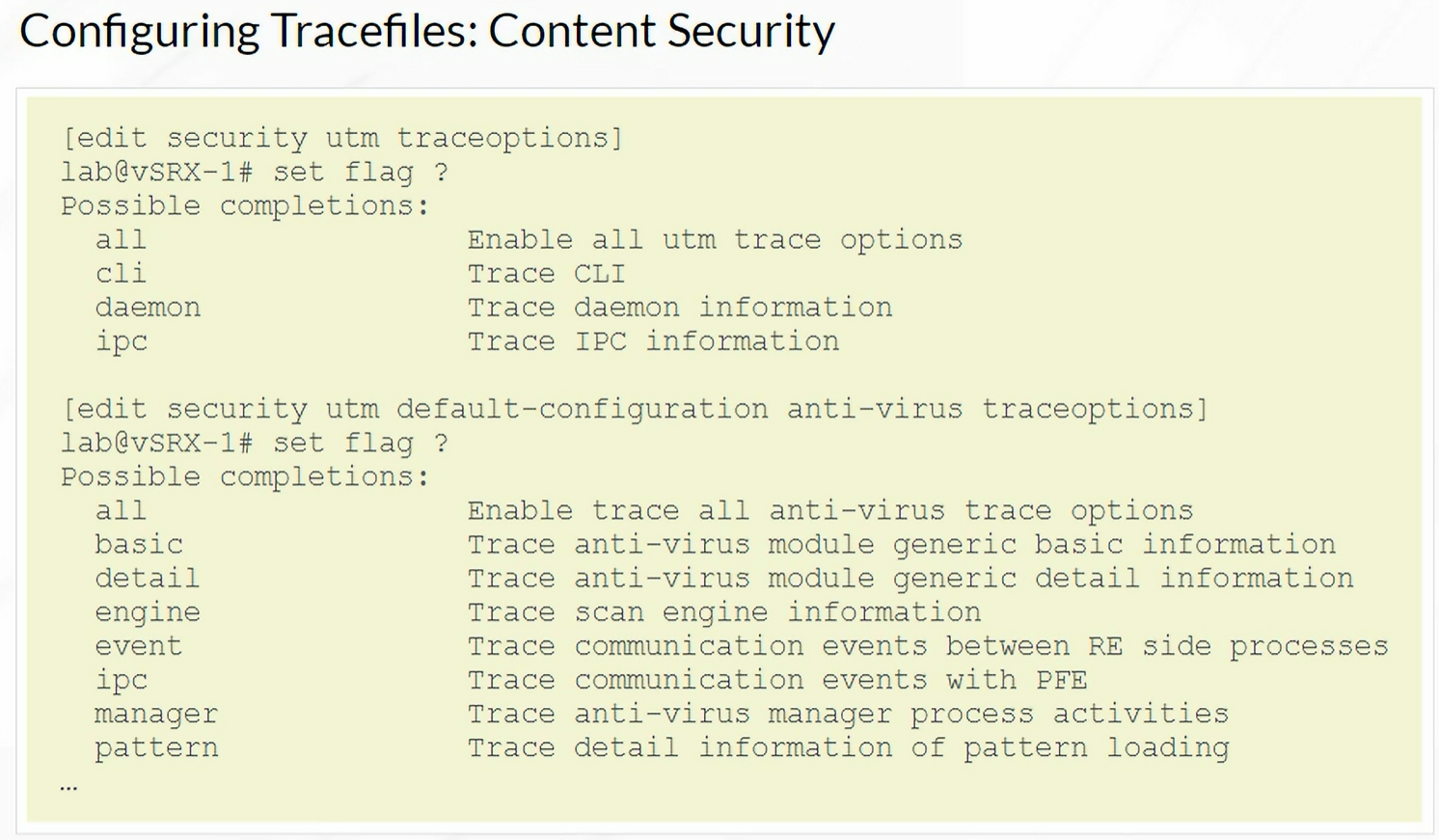
Traceoptions
Always stored in /var/log
Enabling Tracefiles for Application Identification
Enabling Tracefiles for IDP
Enabling Tracefiles for Content Security
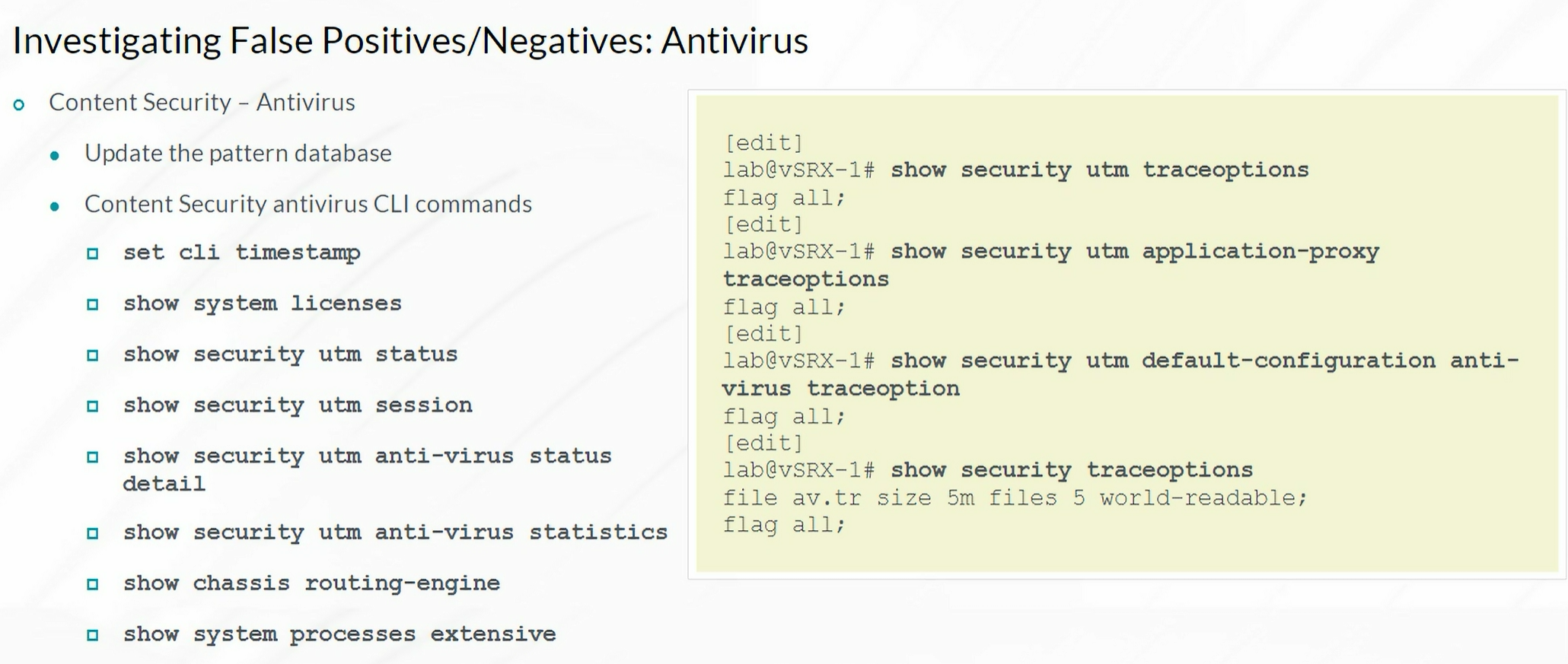
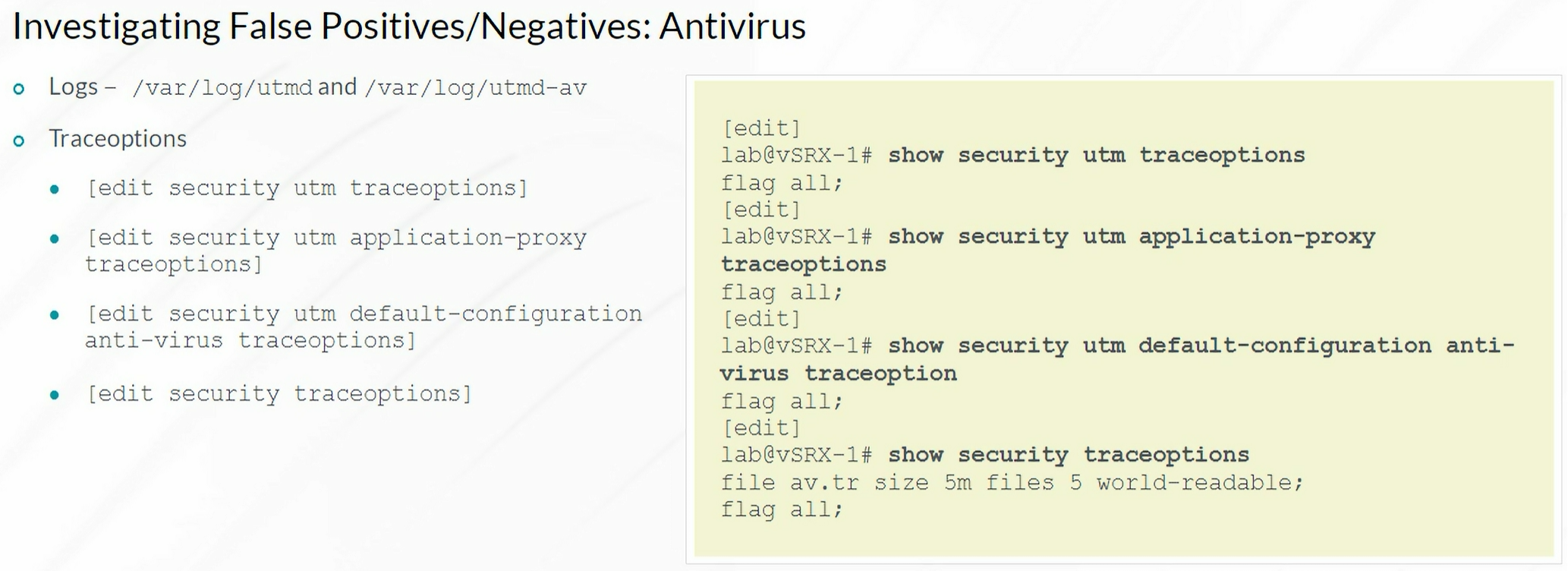
Investigating False Positives/Negatives
Antivirus
1
| show security utm anti-virus statistics
|
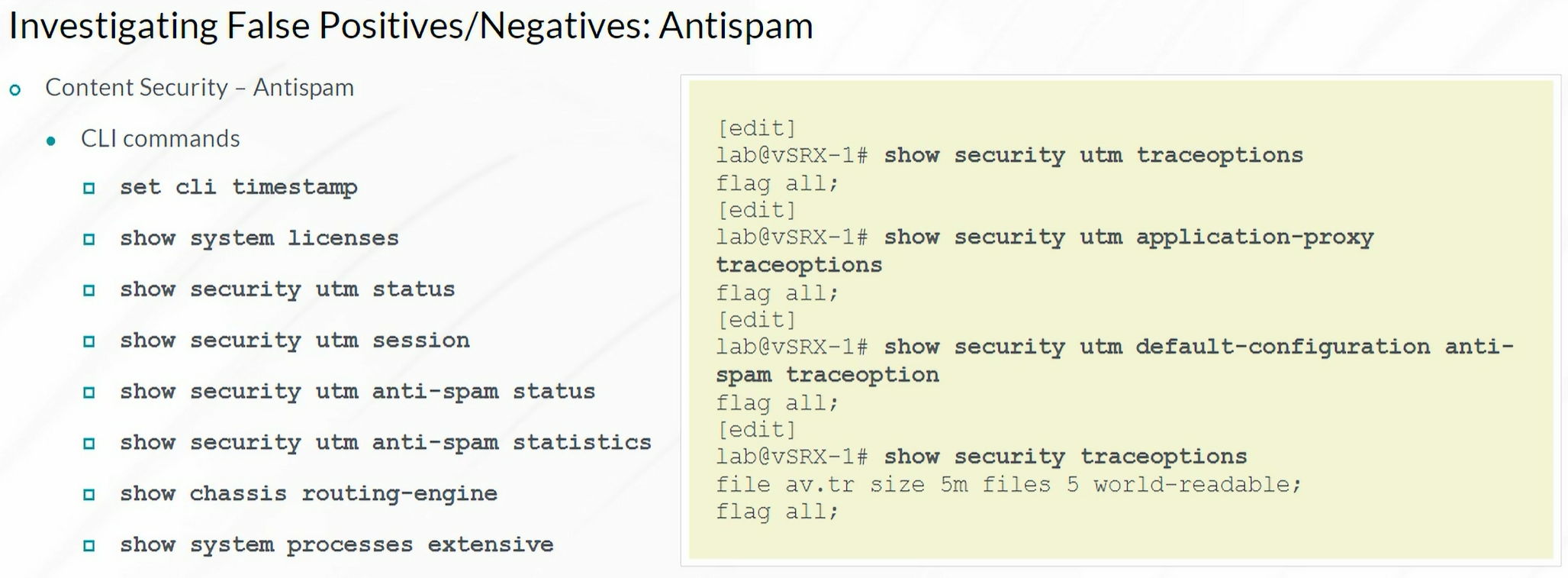
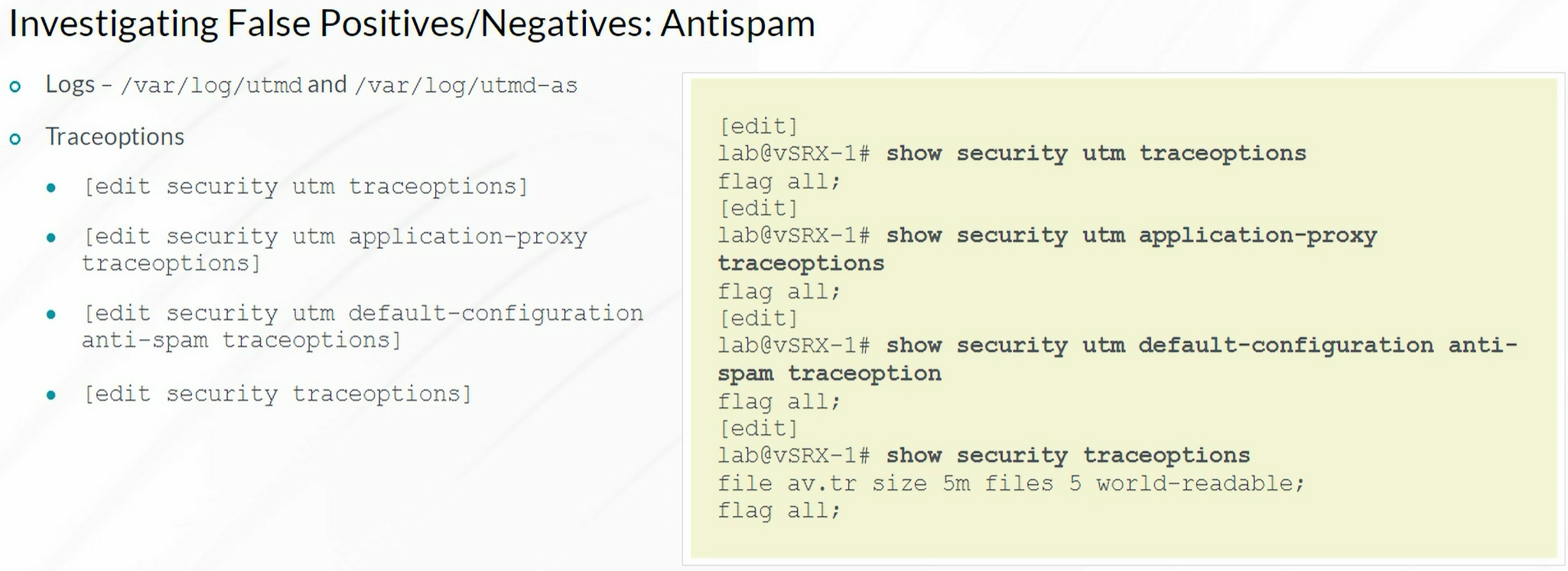
Antispam
1
| show security utm anti-spam statistics
|
1
| test security utm anti-spam ip-check 10.1.1.1
|
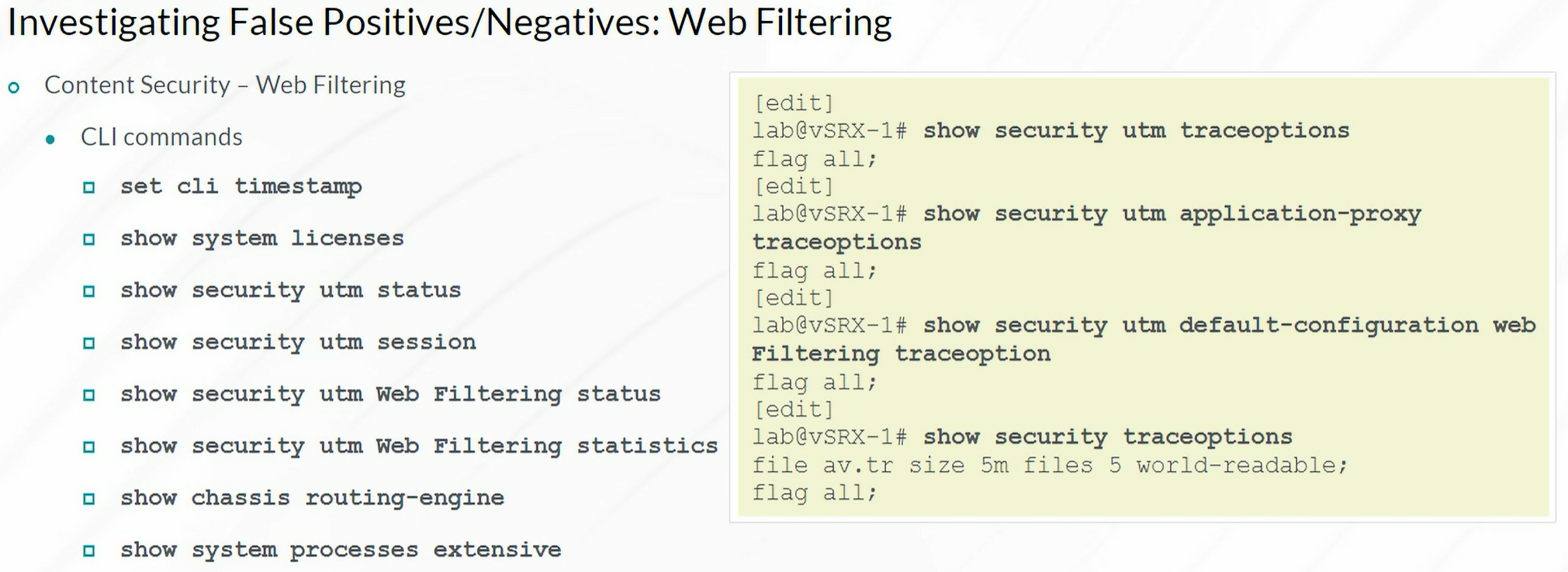
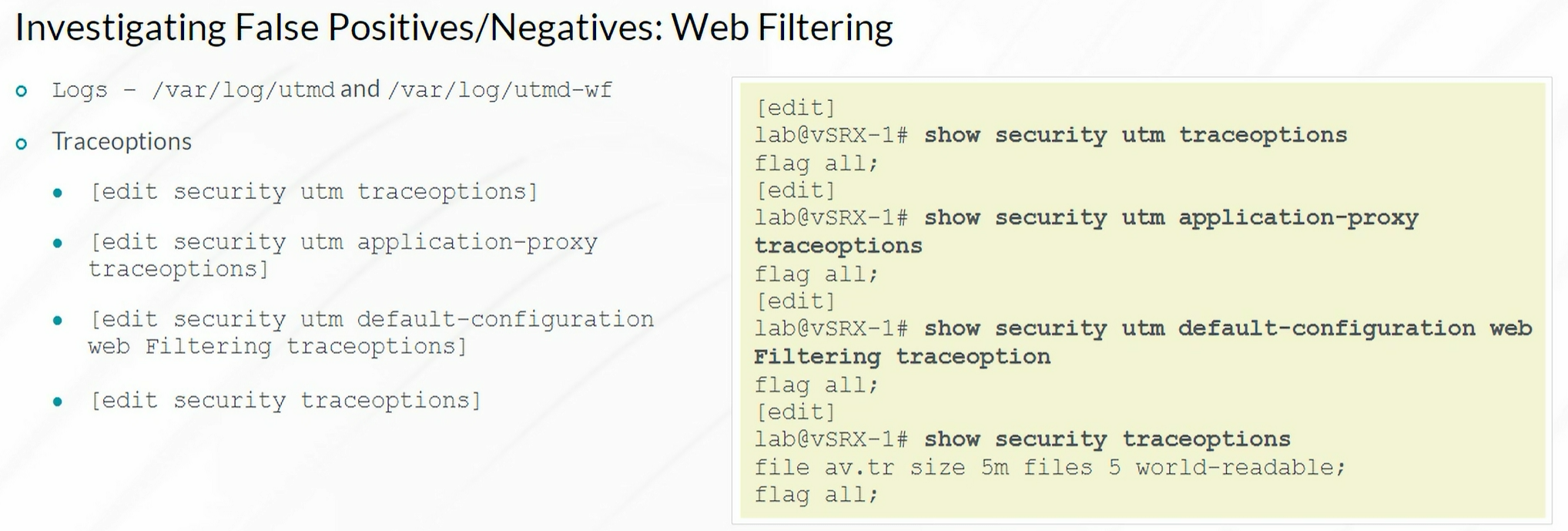
Web Filtering
1
| show security utm web-filtering statistics
|
1
2
3
4
| test security utm enhanced-web-filtering url-check juniper.net
test security utm web-filtering profile WF-pro juniper.net
test security utm web-filtering profile WF-pro example.com
|
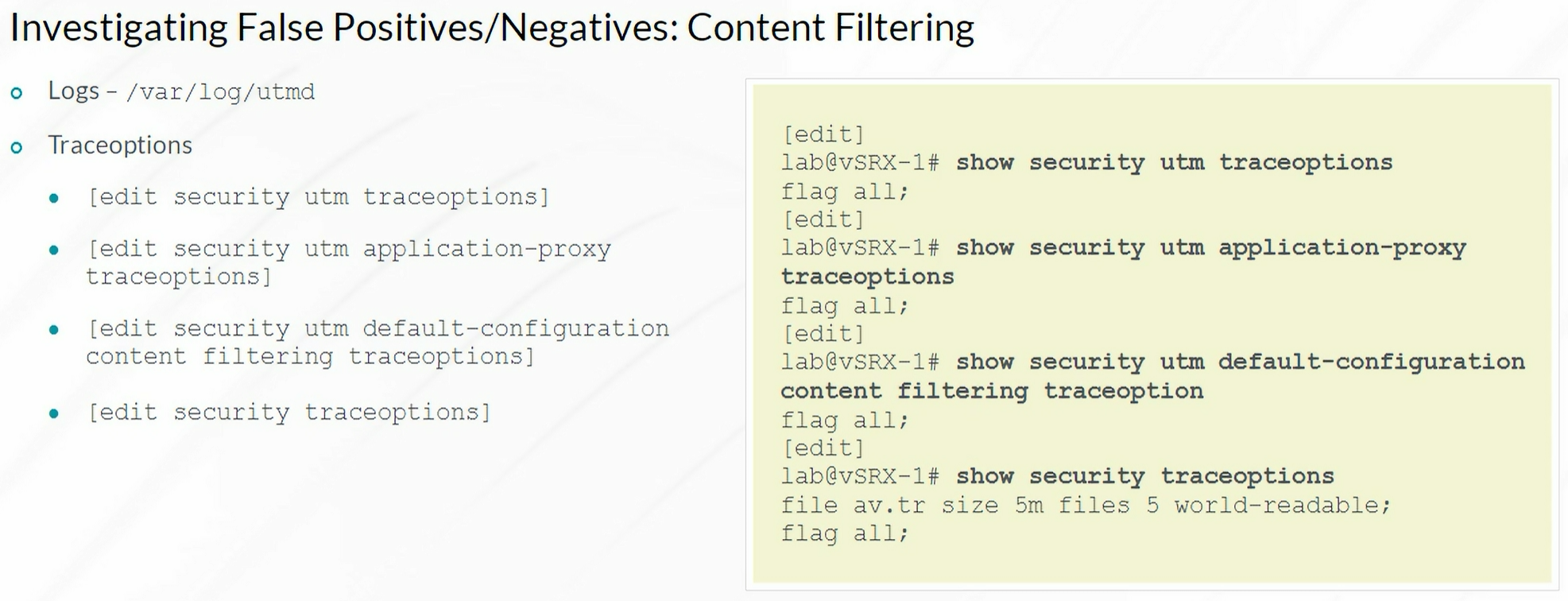
Content Filtering
1
| show security utm content-filtering statistics
|
Examining Syslog Logging
1
| show log message | match RT_UTM
|
Basic Monitoring
1
2
3
4
5
6
7
| show system uptime
show chassis routing-enginge
show chassis hardware
show chassis forwarding
show system storage
show system virtual-memory
file list recursive
|
1
| monitor interface traffic
|
1
2
3
4
5
6
| show chassis status
show fan status (doesn't apply to vSRX)
show chassis fan
show chassis routing-engive
show chassis hardware
show chassis forwarding
|
1
2
3
| show interfaces terse
show interfaces statistics
show interfaces ge-0/0/0.0
|
1
| show ethernet-switching table
|
- Displaying Junos OS Release
1
2
3
4
| show system uptime
show version
show system information
show system firmware
|
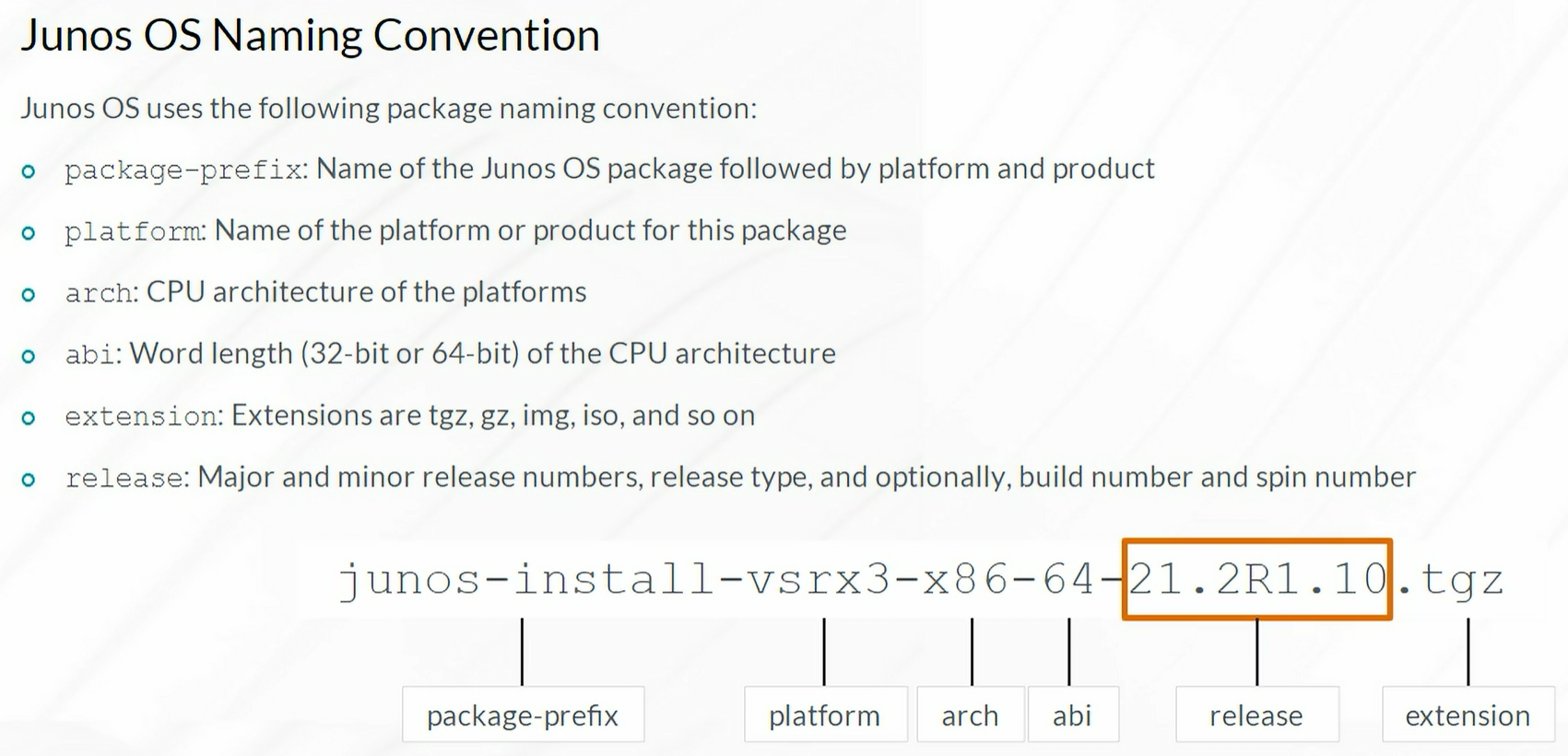
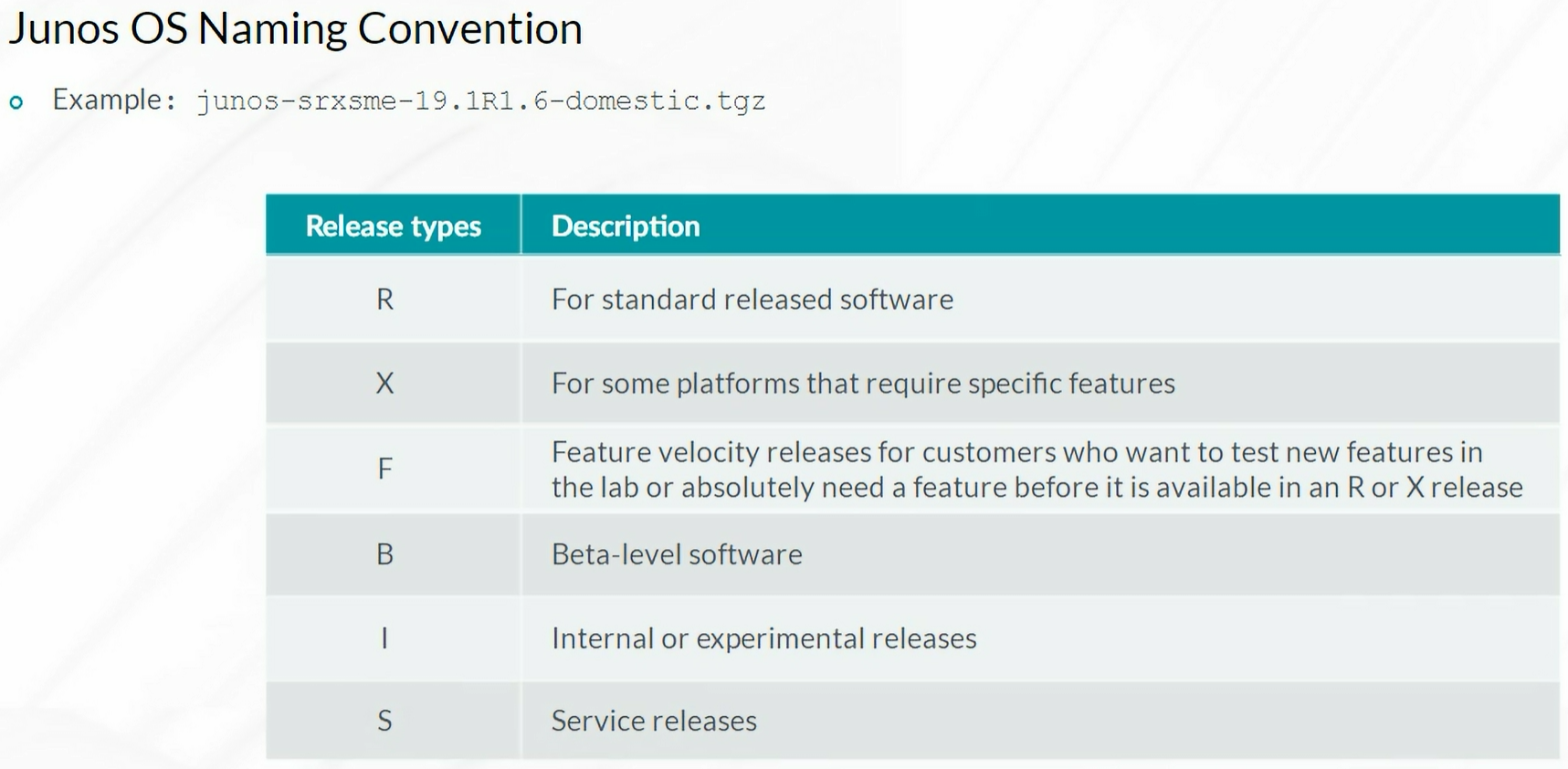
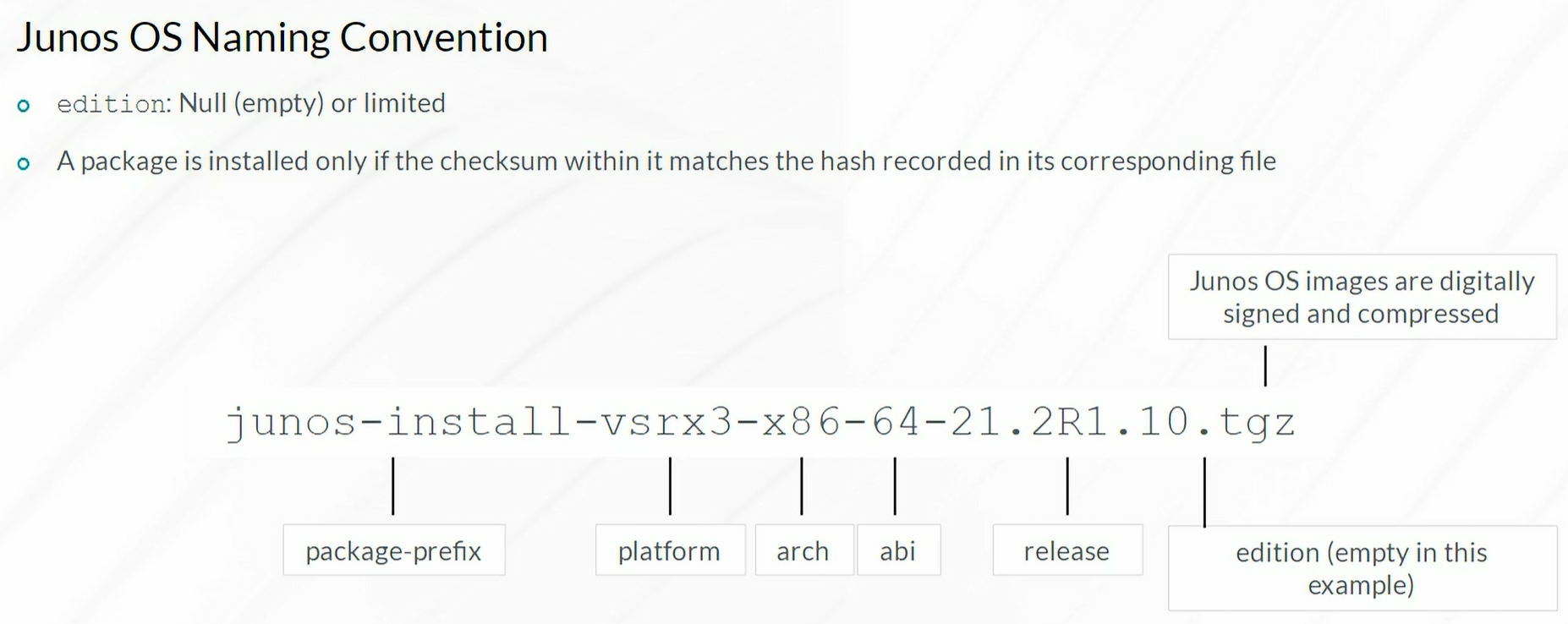
- Junos OS Naming Convention
1
| request system software add /var/tmp/junos-srxsme-20.1r1 no-copy reboot
|
Tip: Add the reboot option rather than executing an additional command to reboot the SRX
- Rollback to Previoos Junos OS version
1
| request system software rollback reboot
|
1
2
| show log messages | match Events
show log interactive-commands
|
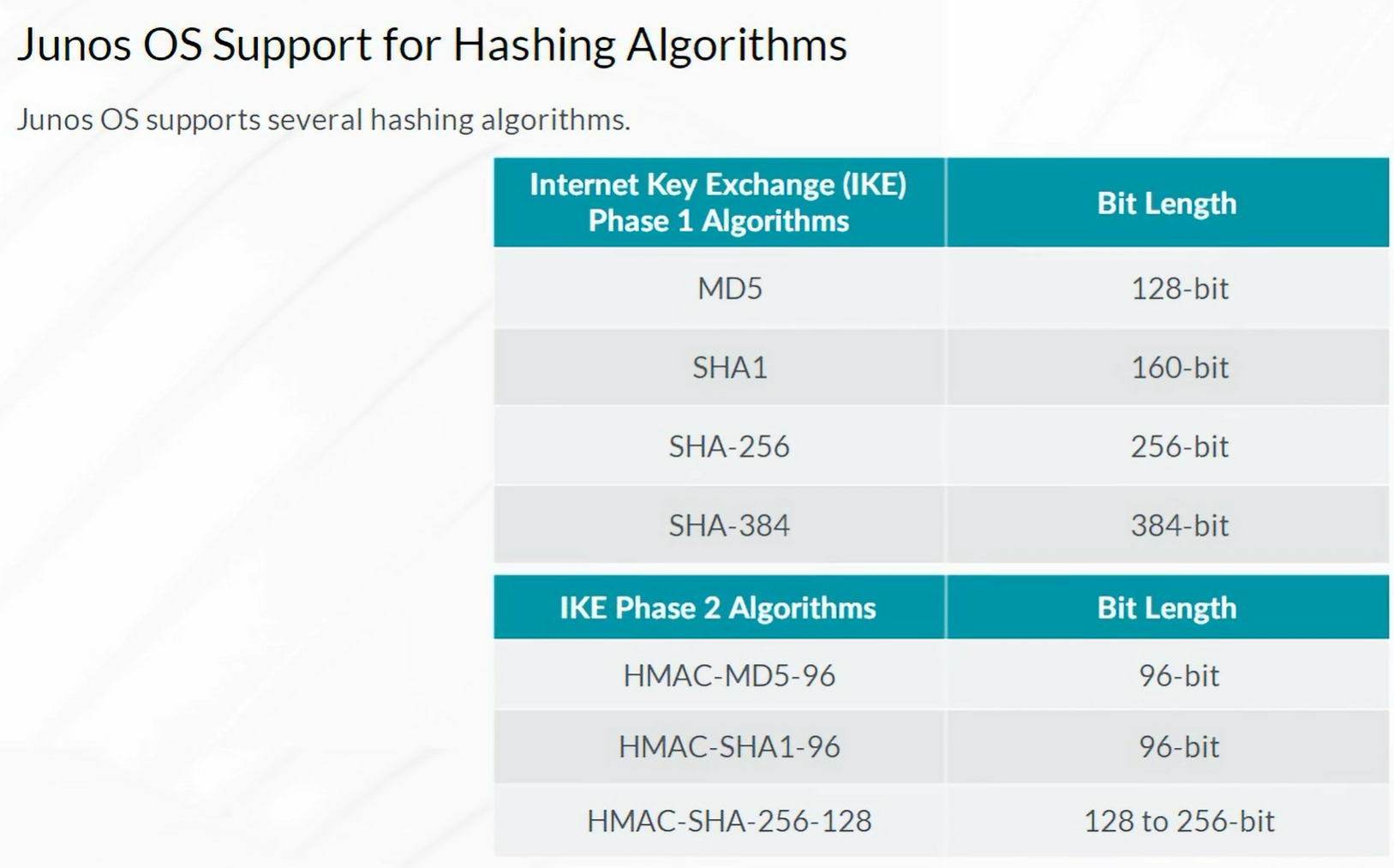
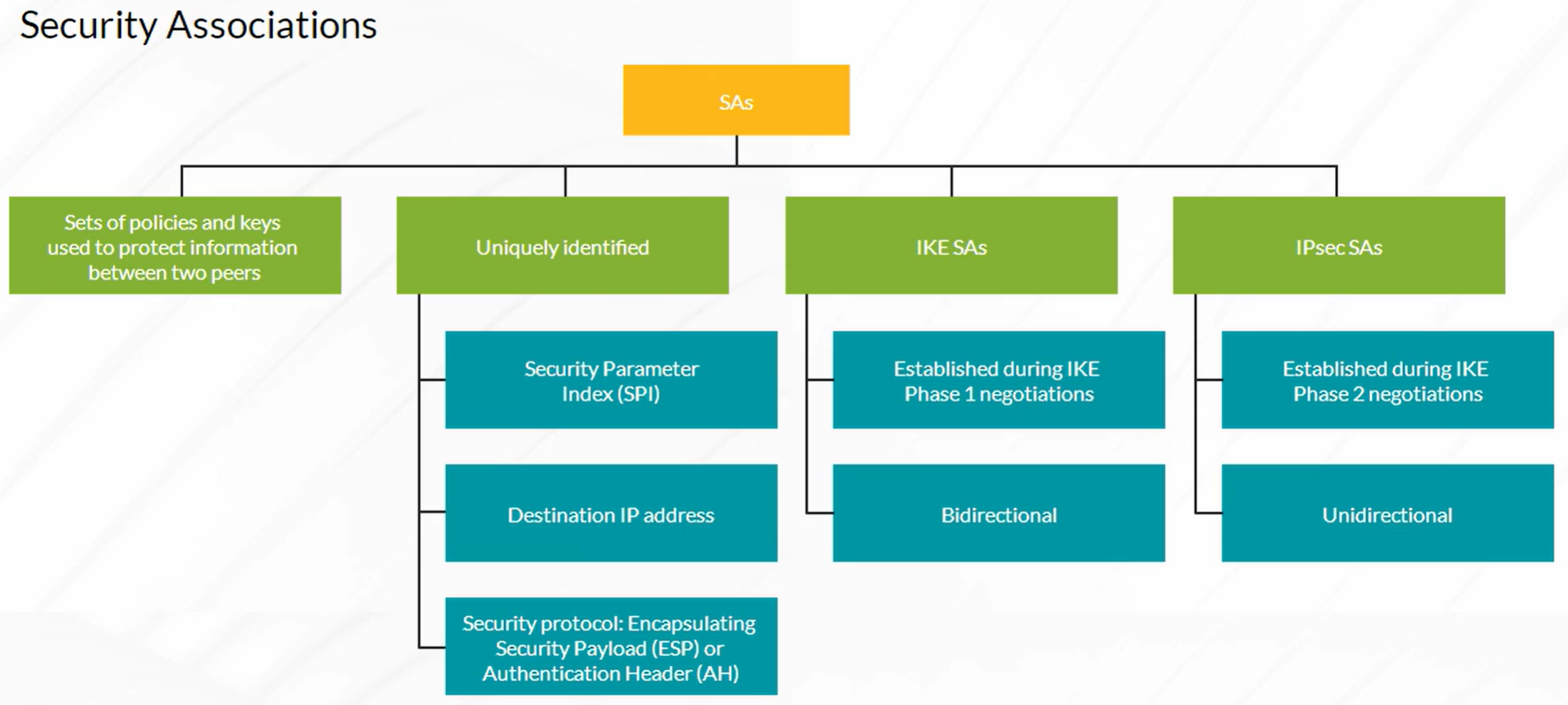
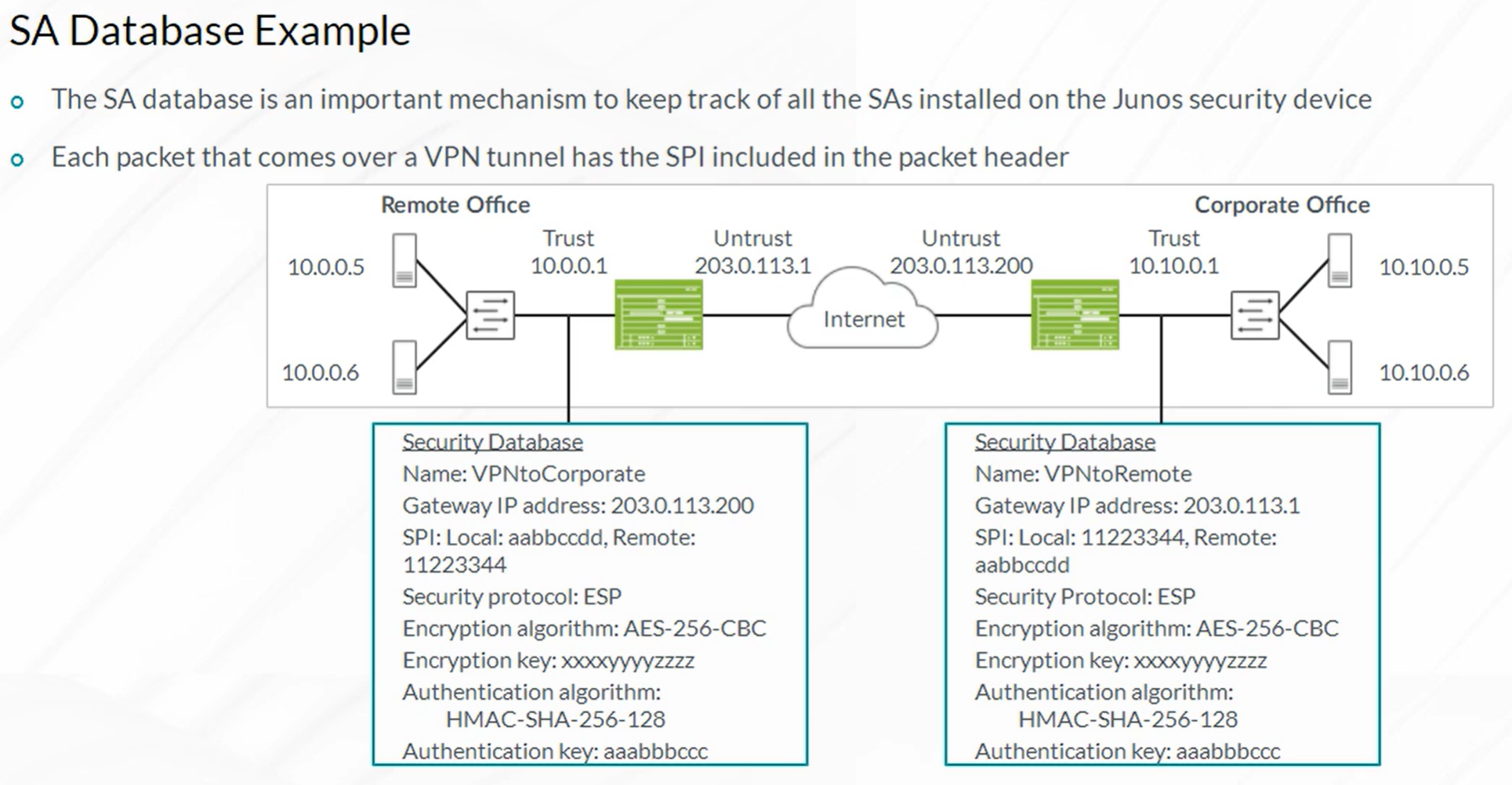
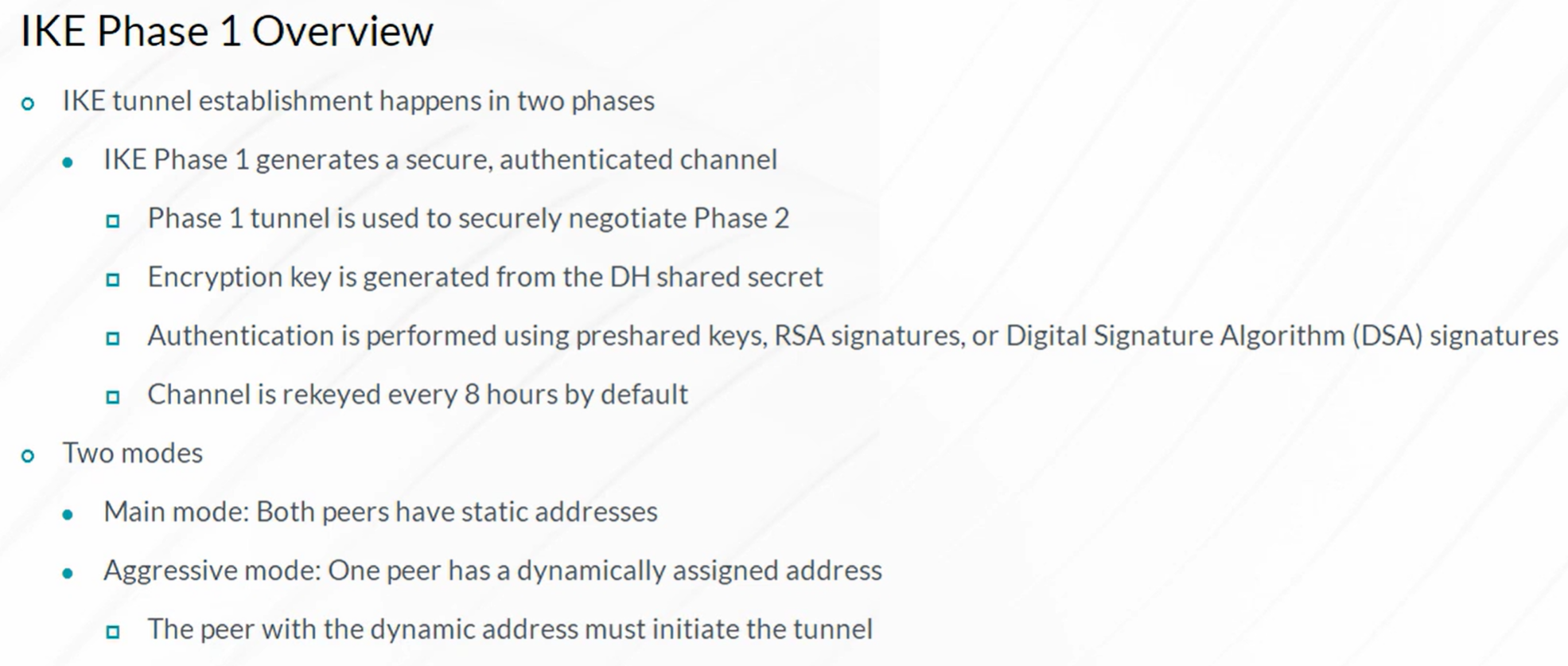
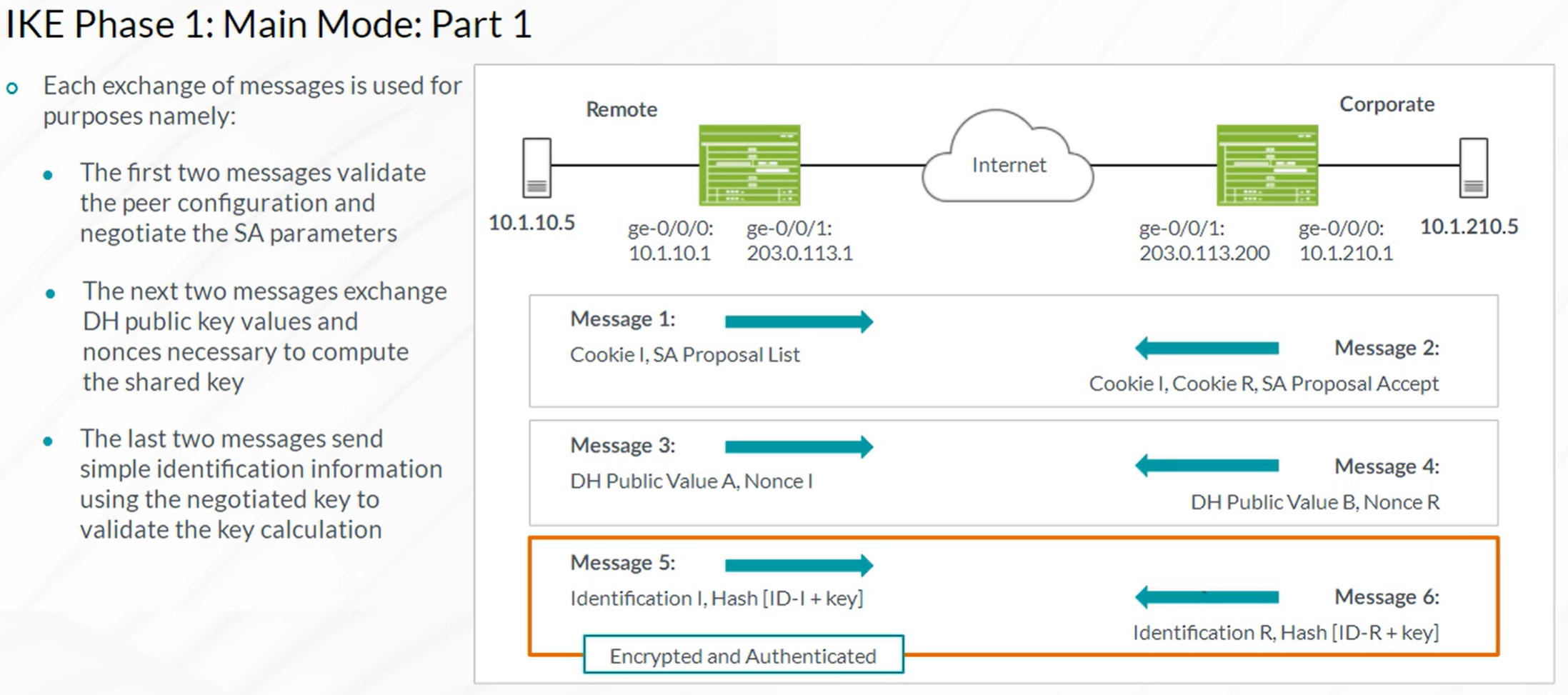
IPsec VPN Concepts
Useful Resources